Solve your biggest cloud security risks — Today
Cloud applications are no longer optional. They lower your costs, increase agility and become a standard piece of every modern digital infrastructure. Unfortunately, the cloud also creates a wide range of new security risks that leave your critical assets and workloads exposed to criminals. To drive a secure digital transformation, you must find a way to map, measure, and manage these risks.
Our Cloud Security Assessment (CSA) services help you do just that. Our CSA services protect your data and workloads in the cloud, ensure reliable access to your cloud assets, and help you dive into a secure, confident digital transformation.
1 in 4
IT professionals have experienced data theft from the public cloud according to McAfee
To follow or contact us:
![]()
Atos CSA Services: what it is?
Our assessments give you a practical, proven, and reliable way to measure your cloud risk against leading security industry standards. We will provide you a clear picture of what cloud-based risks you carry and how to reduce them systematically. Each of our assessments covers every major cloud security threat, and:
- Follow a proven step-by-step approach that exceeds industry standards
- Built and delivered by experienced cloud security experts
- Deploy non-invasive processes that preserve business operations
- Provide executive-ready reports and precise technical recommendations
- Give you a cloud security roadmap that you can quickly bring to life.

Map, measure, and manage your cloud risks
Our CSA services can assess every corner of your cloud deployment. Our world-class cloud security experts and proven methodology will give you a comprehensive picture of your risks and how to remediate them, all within a tightly scoped service. Our CSA services follow a simple, practical three-step framework.
Step 1: Program evaluation
We perform a “deep dive” on every detail of your cloud security. We then collect and analyze this data to measure your risk. Finally, we give you detailed reports that tell you what we found — from technical and non-technical perspectives.
Step 2: Recommendations
We provide an actionable list — prioritized by risk — of every security challenge we discover. This list will provide technical and non-technical actions you can take to remediate every issue that we find.
Step 3: Cloud Security roadmap
We will give you a clear, visual representation of your short and long-term recommendations for improvement. We will place these recommendations on a timeline to tell you exactly when to execute each modification.
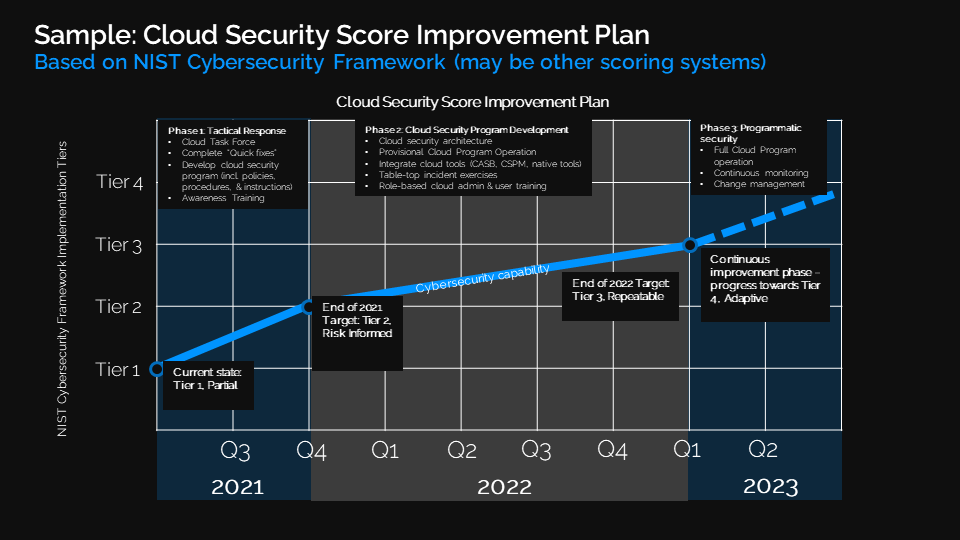
What you will get: core outcomes
At the end of every CSA service, we will provide a well-defined suite of deliverables that crystalize our assessment and leave you with actionable strategies and concrete next steps. Our service’s deliverables include structured executive-ready briefings, technical views of your results, and a clear security improvement plan.
Each of these deliverables will fit easily into your existing strategy and project plans. With them, you will improve a wide range of uses cases, including:
- Enhancing your risk management strategies
- Improving your regulatory compliance
- Identifying new investments in security technology and services
- Making “go / no go” decisions for acquisitions
- Updating your policies and procedures
- Taking direct action to mitigate your most significant risks immediately.
What you will get: key benefits
Improve your baseline cloud security
You will identify your cloud-based security risks, develop effective methods to close those risks, and prioritize your end-to-end remediation actions.
Achieve and maintain compliance
You will objectively measure how well your current cloud environment aligns with specific regulatory standards and learn how to meet your requirements.
Develop granular cloud security
You will receive tailored assessments that analyze and provide recommendations for individual security domains in your posture (e.g., access controls).
Eliminate supply chain threats
You will uncover any security concerns within your current supply chain and make sure you are securely storing your information with third-party providers.
Keep your evolving cloud landscape secure
You will assess a wide range of popular cloud platforms against an up-to-date library of threats to deploy well-protected digital environments rapidly.
Related resources
Brochure
Cybersecurity: Building trust in Hybrid Cloud
The cloud security challenge – The Cloud is a key enabler of digital transformation. It is transforming business, organizations and government, enabling new levels of speed, agility and focus.

Magazine
In this edition of the Atos Digital Security Magazine, security experts from all horizons and specialties have shared their unique and in-depth knowledge on how to make cybersecurity an enabler of your digital transformation.
Cloud security
Discover how Atos cloud security offering can help you to keep a complete security of your sensitive data, maintain control of compliance, ensure integrity of your applications in the cloud.




