SolarWinds attack: are you ready for the supply chain risk?
Shoring up your defenses against supply chain attacks.
A quick background of the SolarWinds attack and checklist to stay protected
The recent SolarWinds attack represented one of the more impactful and sophisticated events in recent times. The attacker performed a “supply-chain” attack to compromise network management software produced by SolarWinds. This note will provide background on this event, Atos’ perspective (including challenges, mitigating actions, and outlook) and further information resources.
Background
Recent large scale, sophisticated attacks are exploiting weaknesses in the implementation of supply chain management processes. The recent compromises involving SolarWinds Orion are distinguished in that the Advanced Persistent Threat (APT) actor targeted the supply chain to bypass traditional enterprise perimeter and detection defenses.
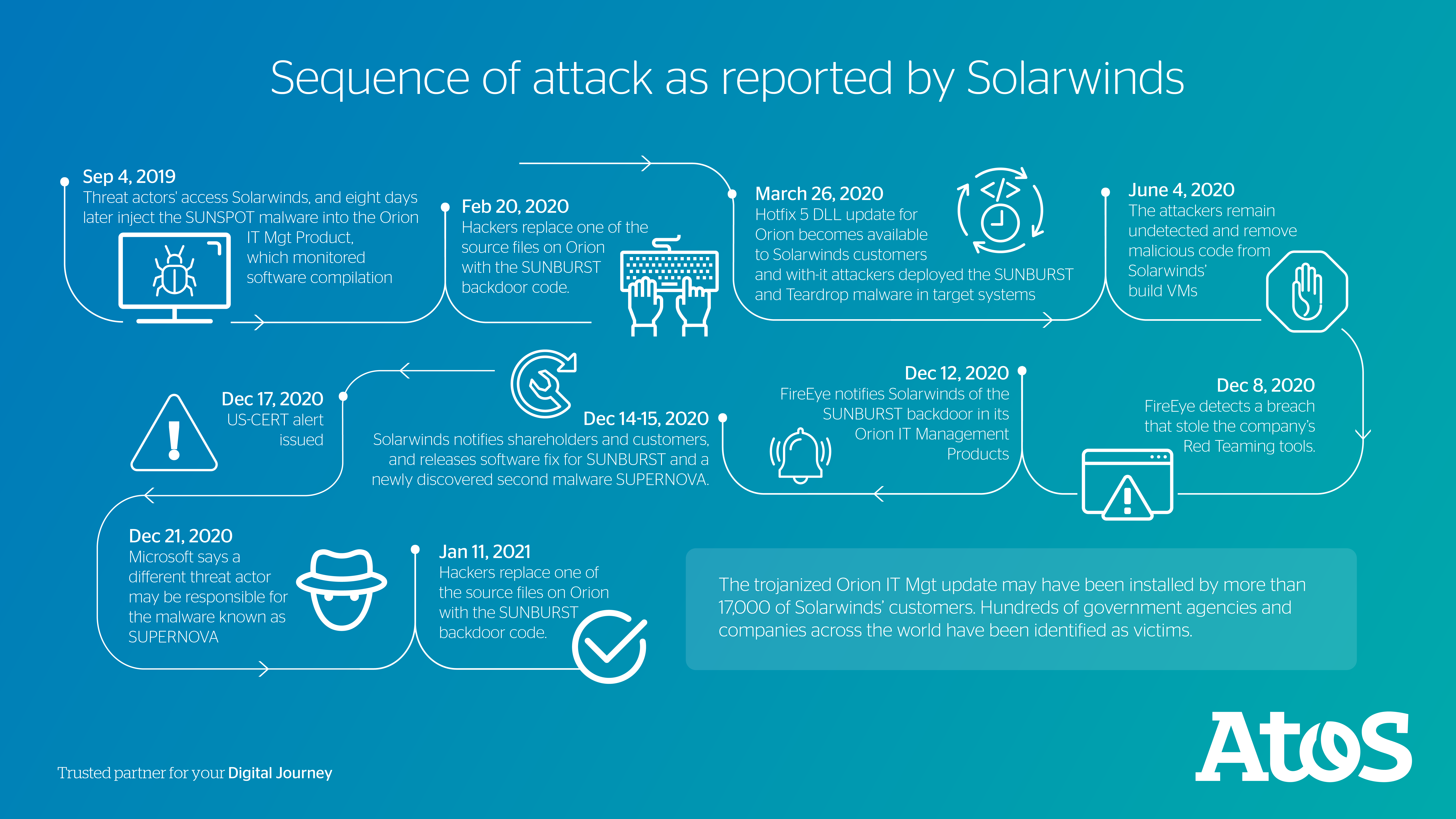
The attack involved cyber actors compromising SolarWinds' build infrastructure and used that access to distribute trojanized software updates to over 18,000 SolarWinds customers.
What is SolarWinds?
SolarWinds Inc. is a US-based company that develops software for businesses to help manage their Networks, Systems and Information technology infrastructure. SolarWinds has a customer database of 300’000 customers, including US Federal government, 80% of the Fortune 500 and diverse customers worldwide.
How did it happen?
The threat actors used sophisticated zero-day malware to compromise the build servers of SolarWinds, which could identify when installed on a developer system and waited until the developer accessed specific Orion source code files. It then activated to replace one of the source files to include the SUNBURST backdoor code, inserting the malicious code into SolarWinds Orion’s legitimate software update. SolarWinds customers unwittingly installed the malware by updating their Orion platform. This attack methodology is typically known as a supply-chain attack as it affects all companies applying a trusted piece of software containing malware.
The difficulty in detecting and responding to the threat
Firewalls, intrusion detection services, and other monitoring apparatus were arguably limited in their capabilities to detect the attack and permit a timely incident response. Although the incident came to prominence in December 2020 after the FireEye disclosures, initial reports indicate that the attack may have begun as early as September 2019. SolarWinds and their customers were likely subject to exposure for months until the incident was made public.
CISOs or Information Security Practitioners already know they should maintain mature supply chain management processes, including understanding how the vendor manages security, whether their quality program includes secure development principles, and maintain sound change management processes (in addition to other widely recognized standards and best practices). However, given the sophistication of this attack, it is worth considering whether conventional supply chain management practices adequately address the risks involved with incidents like SolarWinds.
A checklist to be better prepared
So, how should enterprises deal with such sophisticated attacks?
Go beyond conventional supply chain practices. At Atos, we rely on routine practices and sharable intelligence from our security services to anticipate and respond to threats. These best practices can be an opportunity for CISOs or other individuals responsible for enterprise defense to compare their response checklist to what we have provided here.
There is no single countermeasure to mitigate a supply-chain attack. The preparation must consider people and processes, as well as technologies.
Does your checklist include the following considerations?
- Routine review of intelligence from Information Sharing and Analysis Centers (ISACs), national and regional Community Emergency Response Teams (CERTS), and other organizations involving infrastructure management software
- Adopt a risk-based vulnerability management approach by using:
- Threat intelligence capabilities
- Risk scoring based on various aspects like the business context of the assets and criticality
- Ensure correct implementation of encryption for storage, transmission, and processing (tokenization)
- Review supply chain risk management standards and adopt best practices. One such resource, available at no-cost, is NIST-SP 800-161 “Supply Chain Risk Management”
- Deploy a Zero Trust architecture; implement a no trust strategy-based policy verifications
(see Atos publication “On the Road to Zero Trust”) - Exercize business continuity and disaster recovery plans in drills or tabletop exercises
- Deploy advanced threat detection capabilities, including those supported by artificial intelligence
- Identify the process to report a breach to your local crime complaint center
A practical approach to manage supply chain threats
As described in this note, there is no single countermeasure to mitigate a supply-chain attack. The preparation must consider people and processes, as well as technologies. These must be orchestrated through operational, tactical and strategic approaches to protect your organization. At Atos, we are committed to contributing our expertise and skills to our clients and the greater cybersecurity community. This includes perspective and resources to support greater enterprise and operational resilience.
Atos Intelligence Services were referenced for this report:
Global Threat Intelligence report
By Dan Schaupner, Head of Cloud and Innovation, Global Digital Security Consulting
Posted on January 28