How can you deploy secure, scalable IoT networks?
With the massive growth in IoT deployments, communication service providers are rolling out many dedicated networks. While adopting new industry standards such as low-power, wide-area network (LPWAN) protocols, they must also ensure that these systems are secure and that data privacy is maintained.
To address these challenges, network operators should consider the following nagging security questions:
- How can you secure the network and communication infrastructure?
- How can you maintain both security and performance while scaling up your operations?
- How can you control the manufacturers and devices accessing the network?
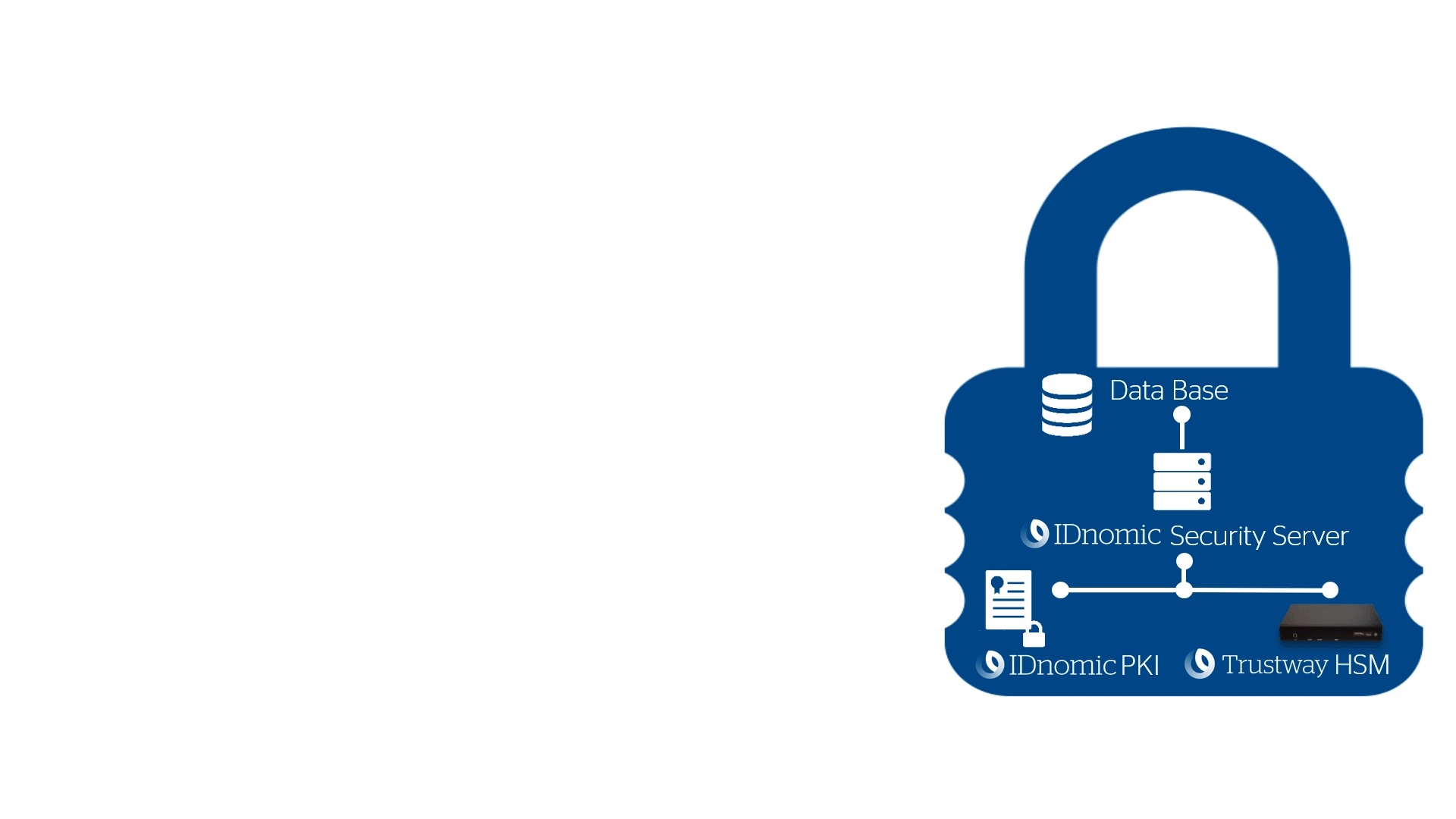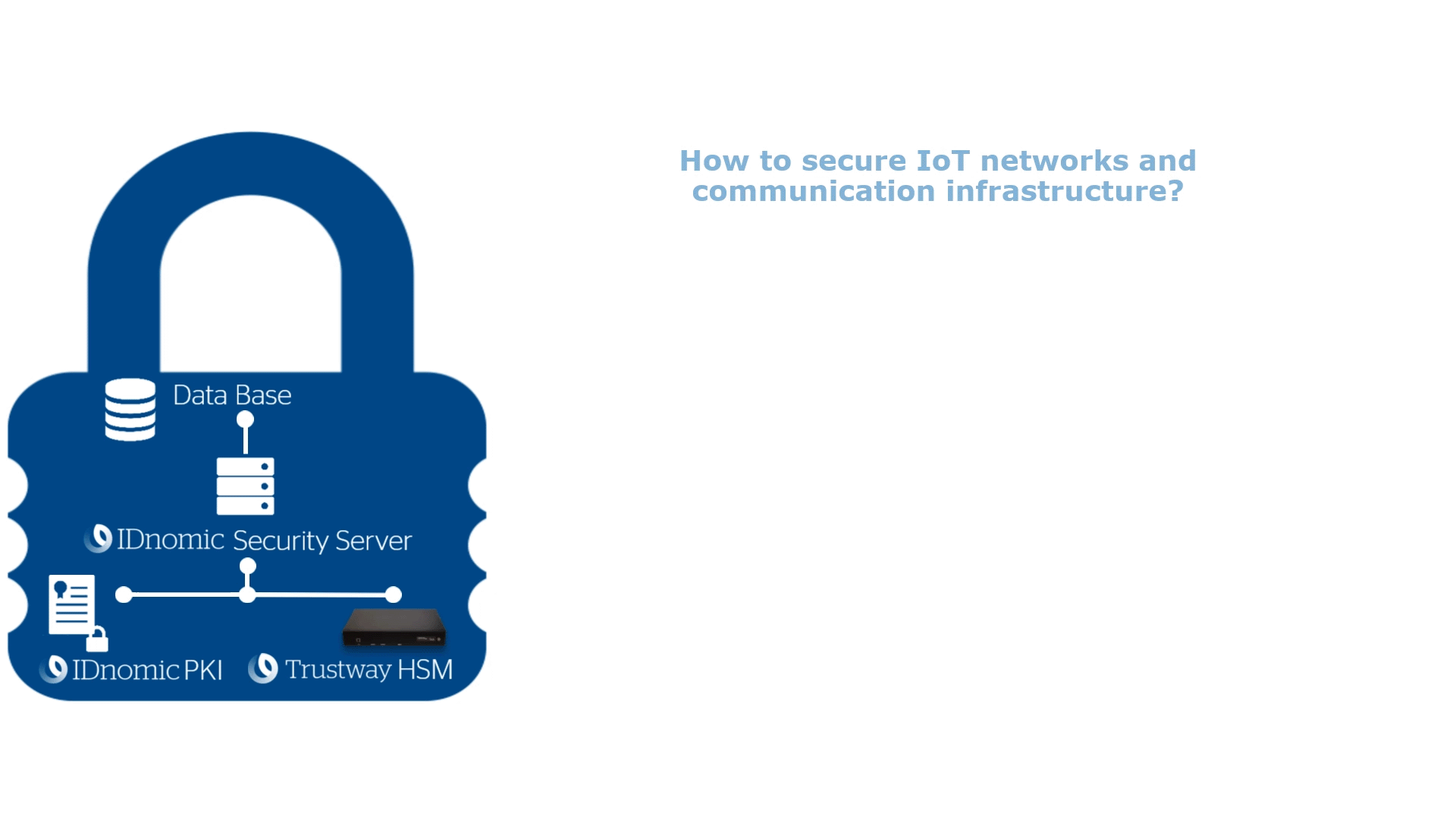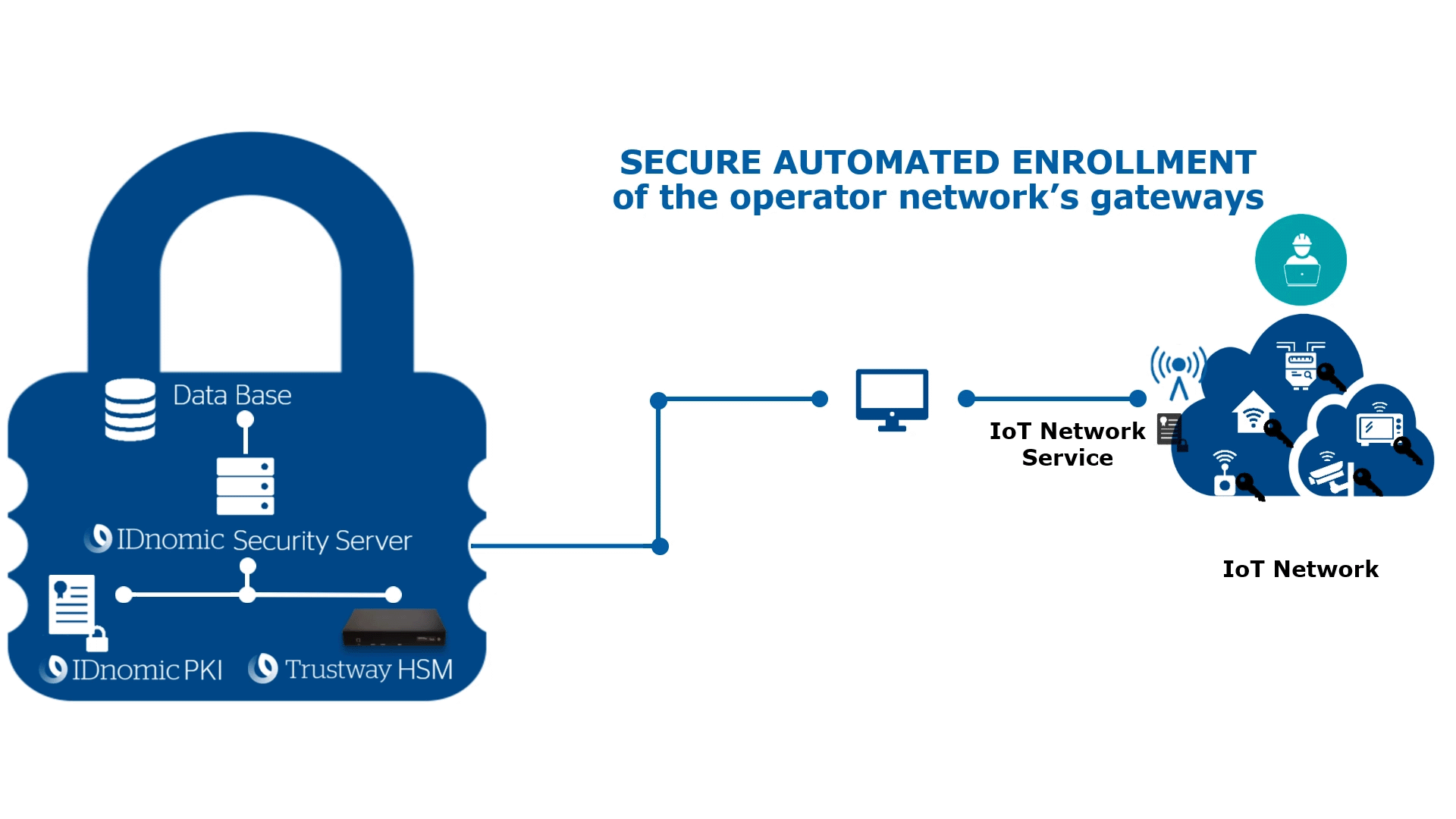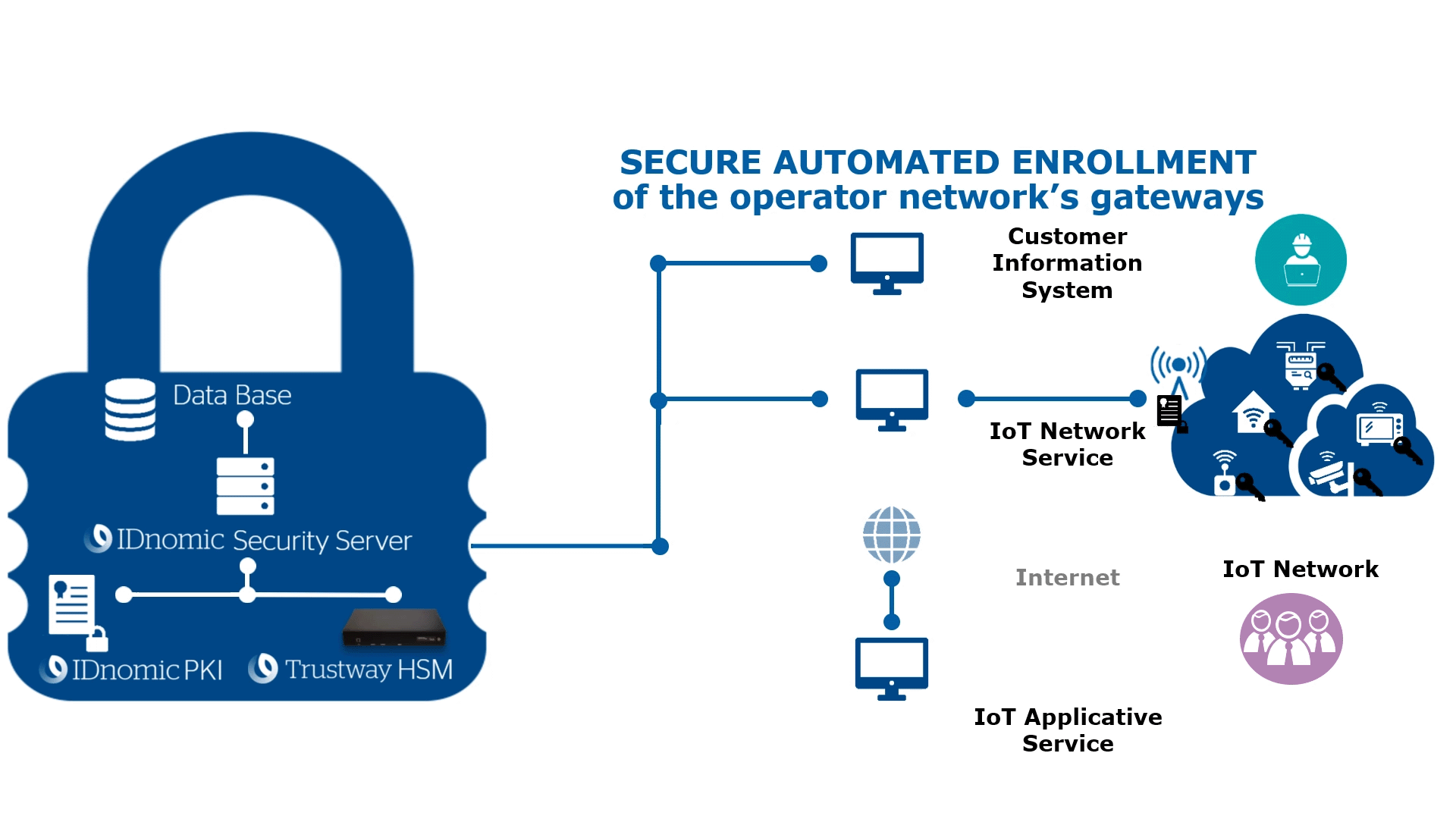
Create your own Certificate Authority to generate electronic certificates.
Follow or contact us:
![]()
4G and 5G: Prepare for the next security and scalability challenges

Mobile networks have evolved considerably in recent years. The evolution from 4G to 5G will improve the power and capacity provided to support the growing IoT ecosystem. Along with high user mobility and reliable communication, 4G and 5G network infrastructure security must evolve to meet new challenges and standards. For operators, implementing a PKI solution can be the key to success for:
- Authenticating connected devices to ensure organizations are only working with trusted identities for message integrity
- Enabling scalable certificate management to support the networking power of 5G and meet growing number of IoT requests
- Supporting advanced cryptographic operations for encrypted communication protocols in real time
Atos secures end-to-end IoT communication for Bouygues Telecom
“By partnering with Atos, Bouygues Telecom has been able to design and implement France’s first highly-secure LoRa network. This means our IoT solutions deliver both top-performance and exceptional security.” – Philippe Cola, Core Network Senior Architect, Bouygues Telecom
PKI Technical Certificate Authority: A main component of your IoT security

Strong privacy controls
Ensure the confidentiality of your customer data in compliance with regulations through a solution based on a Common Criteria EAL4+ certified hardware security module (HSM).

User friendly PKI appliance
Easily integrate digital certificates and support different configurations (SCEP, CMP) in a few weeks with the IDnomic PKI appliance’s SaaS model.

Maintain control
Network operators can manage the enrollment of delegated certificate authorities (CAs) and have exclusive subordinate CAs to enforce access policies and issue certificates as needed.
Discover our PKI Technical CA appliance in more detail
Get a demo of PKI
Meet with one of our security experts to see how our product works and how we can help you.
Discover our other solutions for telecom security
Understand how Atos enables data integrity and facilitates smoother telecom operations.


