What is prescriptive security from a technical perspective?
Prescriptive security is, at its heart, a fusion of technologies and processes designed to reduce the time and effort needed to detect and respond effectively to cyber security threats and incidents.
A critical aspect of prescriptive security is its use of automation and artificial intelligence technologies. It is vital that the exact combination of technologies and processes – including where and at what level automation is used – is based on a thorough understanding of the organization’s specific risk profile and level of risk appetite. Usually, prescriptive security solutions are based on selected types of security ‘use case’: a use case is a repeatable way of applying the technologies and processes; these evolve as new threats and challenges emerge.
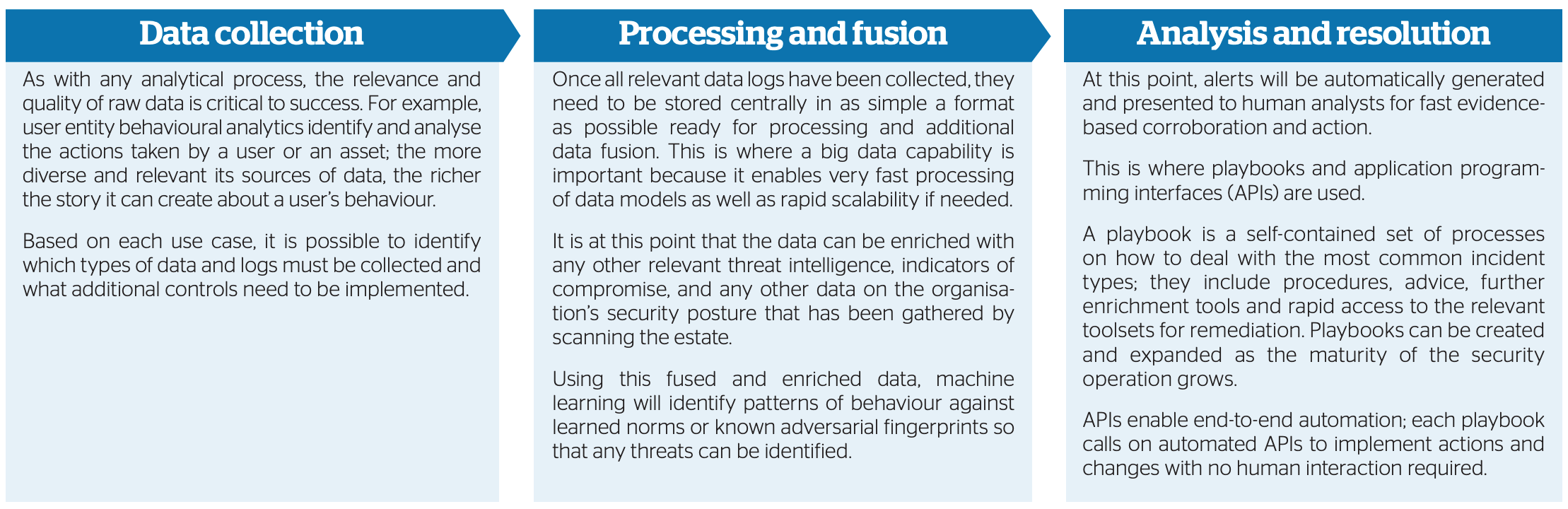
Prescriptive security phases
Critical resources
By implementing prescriptive security, the ever more precious human resource of analysts is freed up to focus on higher-priority, actionable scenarios. At the same time, the organization gets better not only at detecting and responding to security incidents but also at predicting, preventing and pre-empting risks and incidents.
Against a backdrop of increasingly sophisticated and diverse cyber security threats, prescriptive security is becoming business-critical for public and private sector organizations to protect their people, customers, systems, networks and data from any kind of harmful breach or attack.
Digital Vision for Cyber Security 2
Atos’ Digital Vision for Cyber Security 2 brings you insights into the latest challenges and opportunities for business leaders and influencers – and the critical role of cyber security to underpin transformation and vital trust in our digital society.