Atos presented during the European Cyber Week its unique approach to ensure platform firmware resilience in a consistent way from Edge to HPC.
Introduction
The security of platforms is of utmost importance for the business with all critical infrastructure suppliers, including cloud service providers, and telco operators. For decades, Trusted Computing has tried to anchor trust in the hardware, and the existence of Trusted Platform Modules (TPM) in most modern design is evidence that this approach is now well understood. The default behavior of recent Operating Systems like Windows 11 is even to deny booting if this piece of hardware is absent. But this approach is not sufficient in a modern world where one needs to trust remote platforms. To preserve confidence in security, one needs to limit the Trusted Computing Base (TCB) of a system to a level where an assessment can make sense.
During the European Cyber Week in Rennes, Atos has detailed its Trusted Execution Architecture (TEA), the result of a partnership with ProvenRun. This new TEA will bring enhanced security and trust in using well-known hardware mechanisms coupled with a technology previously certified at the highest level of security. It will progressively appear in BullSequana new servers to ensure consistent security from Edge to HPC and Cloud. This allows to envision security features based on some common Root-of-Trust (RoT) known to different platforms, at different scales and levels of interaction. Besides the cybersecurity aspect, the use of known technologies preserves the sovereignty of our platforms for some of our key customers.
A short history of trust in hardware
 In 1993, the NSA tried to introduce the Clipper Chip to promote Key Escrowed Encryption [1]. Even if this attempt failed [2] and backfired in promoting open-source encryption [3], it showed the importance of hardware in computer security, and paved the way to trusted computing. Soon, the Trusted Computing Platform Alliance, renamed as Trusted Computing Group [4], will emerge and promote another piece of hardware, the Trusted Platform Module (TPM), now standardized [5] and embedded in most platforms. Even if adding security hardware can make sense, it is always raising the question of how this new hardwa
In 1993, the NSA tried to introduce the Clipper Chip to promote Key Escrowed Encryption [1]. Even if this attempt failed [2] and backfired in promoting open-source encryption [3], it showed the importance of hardware in computer security, and paved the way to trusted computing. Soon, the Trusted Computing Platform Alliance, renamed as Trusted Computing Group [4], will emerge and promote another piece of hardware, the Trusted Platform Module (TPM), now standardized [5] and embedded in most platforms. Even if adding security hardware can make sense, it is always raising the question of how this new hardwa
re can be trusted. Understanding the alleged improvement in terms of security is also important to assess the security benefit ratio, and in the end other options can be envisioned.

A concept also raised together with hardware security: the Root-of-Trust. It can be seen as the generalization of the second principle of Kerckhoffs: a secure cryptosystem must remain safe when its design is known to the opponent. The need for data protection should be concentrated on keys, which minimizes the data to protect from threats. Auguste Kerckhoffs could not imagine the public-key cryptography [6]. But the Root-of-Trust concept is a consequence of his approach. One can build the security of a system on a small number of private, public, and secret keys. Everything can be public but secret and private keys . And the public keys must be protected in integrity. For this objective, hardware makes sense to protect confidentiality and integrity, because these Root-of-Trust keys cannot be protected by cryptography. This is the classical chicken-and-eggs situation.
Long before NSA tried to promote its Clipper Chip, the ideas of using small pieces of hardware to secure secrets arose in several places. Several patents were filed around this invention, but the seminal industrialization patent was the creation of the first portable support with both a processor and a memory, allowing the small piece of plastic to cryptographically interact with its environment in an active way. Embedding the processor and the memory in the same single ship came rapidly after this, innovating the reign of smart cards. It is worth recalling that Michel Ugon, a French engineer of the Bull company later acquired by Atos was at the core of these inventions [7][8][9].
The HPC challenge
 A typical host architecture will see some buses interconnecting devices, and high-speed interconnection between the memory and the Central Processor Units (CPU). Memory can usually be accessed in at least two ways: indirectly through interaction with the CPU, or directly through Direct Memory Access (DMA). This direct access may circumvent the security features of the operating system running on the CPU if the Memory Management Unit (MMU) is not properly configured. Consequently, any piece of firmware is a potential threat to the operating system, and the integrity of this firmware should be protected. This has been well described in the NIST Platform Firmware Resilience Guidelines [10].
A typical host architecture will see some buses interconnecting devices, and high-speed interconnection between the memory and the Central Processor Units (CPU). Memory can usually be accessed in at least two ways: indirectly through interaction with the CPU, or directly through Direct Memory Access (DMA). This direct access may circumvent the security features of the operating system running on the CPU if the Memory Management Unit (MMU) is not properly configured. Consequently, any piece of firmware is a potential threat to the operating system, and the integrity of this firmware should be protected. This has been well described in the NIST Platform Firmware Resilience Guidelines [10].
 The first challenge is that any platform from Edge to Cloud, has a huge number of firmware which are handled on different buses and devices. Besides the UEFI BIOS and the Operating System, a modern platform needs a lot of different pieces of hardware and corresponding firmware. For instance, a server board is managed by a Baseboard Management Controller (BMC) which is embedded on the platform and deals with the platform maintenance. This BMC runs a whole Linux operating system on a dedicated Application Processing Unit (APU) in a System-on-Chip (SoC). The BMC has its own boot sequence, called U-boot. And it powers on the CPU on the platform, kicking-off the CPU boot sequence. The CPU has also its own firmware, as well as all the other devices on the platform (network cards, disks, etc.). And the baseboard has also a set of programmable hardware (FPGA, CPLD).
The first challenge is that any platform from Edge to Cloud, has a huge number of firmware which are handled on different buses and devices. Besides the UEFI BIOS and the Operating System, a modern platform needs a lot of different pieces of hardware and corresponding firmware. For instance, a server board is managed by a Baseboard Management Controller (BMC) which is embedded on the platform and deals with the platform maintenance. This BMC runs a whole Linux operating system on a dedicated Application Processing Unit (APU) in a System-on-Chip (SoC). The BMC has its own boot sequence, called U-boot. And it powers on the CPU on the platform, kicking-off the CPU boot sequence. The CPU has also its own firmware, as well as all the other devices on the platform (network cards, disks, etc.). And the baseboard has also a set of programmable hardware (FPGA, CPLD).
Ensuring security and trust in all this hardware and firmware can be envisioned with additional hardware which would protect the integrity of the platform. This approach is for instance promoted by the Open Computing Project [11]. But the HPC faces a specific challenge in that the density of a computing board makes difficult to add a new hardware. This would impact the buses and the cooling which are the two main artefacts which make an HPC efficient. Therefore, we had to imagine another approach.
Atos’ Approach for RoT
Since all our servers are embedding a BMC, which is already trusted to manage the board and its firmware, it appeared as a good candidate for Root-of-Trust promotion. Yet, hardening the BMC is mandatory to achieve such objective.
Atos uses OpenBMC [12] as a basis for its BMC software.
This is a well-designed open source, but it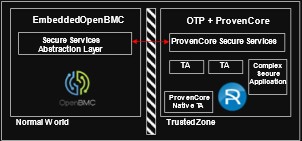 doesn’t seem sufficient to achieve a true hardware security level. We leveraged an alternative solution provided by ProvenRun, one of the partners involved in Atos Scaler, the startup acceleration program [13].
doesn’t seem sufficient to achieve a true hardware security level. We leveraged an alternative solution provided by ProvenRun, one of the partners involved in Atos Scaler, the startup acceleration program [13].
The System-on-Chip (SoC) used in the BMC embeds the TrustZone technology which is part of its ARM Core [14]. This is used to host a hardened Operating System TeaCore provided by ProvenRun to implement a Trusted Execution Environment (TEE). The TEE is then used to secure the two chains-of-trust related to secure boot and firmware upgrade.
 TeaCore is based on the use of a proven operating system ProvenCore which has been certified by ANSSI at EAL7 level in a different context [15]. This ensures a better flexibility to later add new security features such as cryptographic keys secure storage, firmware TPM, and/or flash runtime monitoring.
TeaCore is based on the use of a proven operating system ProvenCore which has been certified by ANSSI at EAL7 level in a different context [15]. This ensures a better flexibility to later add new security features such as cryptographic keys secure storage, firmware TPM, and/or flash runtime monitoring.
Last but not least, the cryptographic keys that are used to sign the firmware are processed in a certified Hardware Security Module (HSM) developed by Atos, the Trustway Proteccio [16].
 Together with the Hardware RoT key anchored in the silicon of the BMC, the TeaCore provides the architecture to implement a full Platform Active Root-of-Trust as proposed by Open Compute Project (OCP). As of today, the chains of trust for development and upgrade are implemented. Next steps could introduce attestation mechanisms.
Together with the Hardware RoT key anchored in the silicon of the BMC, the TeaCore provides the architecture to implement a full Platform Active Root-of-Trust as proposed by Open Compute Project (OCP). As of today, the chains of trust for development and upgrade are implemented. Next steps could introduce attestation mechanisms.
Conclusion and next steps
Based on well-known concepts of Product Security, Atos has implemented a Trusted Execution Architecture (TEA), common to all its servers. The trust in this implementation is founded on:
- Public cryptographic root-of-trust keys anchored in silicon.
- Private keys protected by a certified Atos Trustway Proteccio HSM.
- The well-known ARM TrustZone technology embedded in the existing BMC component of our platforms.
- The hardened operating system TeaCore developed by ProvenRun on Atos specification and based on their formally proven and EAL7-certified operating system ProvenCore.
This TEA is first used to ensure some Platform Firmware Resiliency through firmware signatures verified at boot time and before any upgrade. Its generalization to all Atos-made platforms makes possible some innovative security features.
To read more about this security feature:
- Technical Paper presented at C&ESAR 2022 Conference during European Cyber Week
- The audio presentation and its slides.
References
- Howard S. Dakoff, The Clipper Chip Proposal: Deciphering the Unfounded Fears That Are Wrongfully Derailing Its Implementation, 29 J. Marshall L. Rev. 475 (1996).
- Frankel and M. Yung. Escrow Encryption Systems Visited: Attacks, Analysis and Designs. Crypto 95 Proceedings, August 1995.
- Philip Zimmermann – Why I Wrote PGP (June 1991 – updated 1999)
URL: http://www.philzimmermann.com/EN/essays/WhyIWrotePGP.html - Trusted Computing Group. URL: https://trustedcomputinggroup.org/
- Information technology — Trusted Platform Module, International Standards Organization ISO/IEC 11889 series (2009-2015).
- -C. Caraco, R. Géraud-Stewart, and D. Naccache. Kerckhoffs’ Legacy. Cryptology ePrint Archive, Paper 2020/556. URL: https://eprint.iacr.org/2020/556
- Michel Ugon. Support d’information portatif muni d’un microprocesseur et d’une mémoire morte programmable, CII-Honeywell-Bull patent FR77.26107. 26/8/1977.
- Michel Ugon. Portable data carrier including a microprocessor. CII-Honeywell-Bull patent US4.211.919A. 26/8/1977. https://patents.google.com/patent/US4211919A
- Michel Ugon. Single chip microprocessor with on-chip modifiable memory, Bull CP8 patent US4.382.279. 25/4/1978. https://patents.google.com/patent/US4382279A/en?oq=4.382.279
- Special Publication 800-193 Platform Firmware Resiliency Guidelines, National Institute of Standards and Technology, May 2018. URL: https://doi.org/10.6028/NIST.SP.800-193
- Open Compute Project. Platform Security Overview.
URL: https://docs.google.com/document/d/1-bfAF86cEKcn1guF-Qj2C2HhMM2oJ2njNGdHxZeetR0/edit# - Open BMC: Defining a Standard Baseboard Management Controller Firmware Stack. https://www.openbmc.org/
- Atos Scaler, The value of indusry-centric open innovation. URL: https://atos.net/en/atos-scaler
- ARMLtd, “Arm security technology – building a secure system using trustzone technology,” Rev. C, April 2009. https://developer.arm.com/documentation/PRD29-GENC-009492/c
- ProvenCore secure OS achieves EAL7 Common Criteria certification, 13 September 2019. https://provenrun.com/provencore-secure-os-achieves-eal7-common-criteria-certification/
- Atos Trustway Proteccio netHSM
https://atos.net/en/solutions/cyber-security/data-protection-and-governance/hardware-security-module-trustway-proteccio-nethsm

