Surge in malware loaders activity
A dangerous trend before the Christmas Holidays
The Christmas Holidays are almost upon as. We all can’t wait for joyful carols, streets adorned with charming ornaments, feel of crunchy snow under our boots, smell of the Christmas tree and taste of our favorite Christmas pie. After a long and gruel year we finally get a well-deserved break…
Until we get the message that our organization has been hit by ransomware requiring our immediate response, which means leaving our idyllic world once and for all.
That is the most unpleasant scenario for security professionals around the world, and unfortunately, it’s also a very likely scenario. Threat actors love attacking their targets when their defenses are down, and Christmas Holidays are a great opportunity for them.
To prevent them from spoiling our restful days we need to be well prepared and minimize the number of available options for an attack.
For ransomware to be delivered, one needs to get the initial access to the victim’s environment first. That itself is not an easy task and not every group is able to get the access to their targets. This is where Malware-as-a-Service comes into play. A service provided by cybercriminals, that, among other things, can install a second-stage malware on infected machines. Ransomware operators can choose from cybercriminal’s portfolio of already compromised organizations and buy their service. What is left for them is to exfiltrate and encrypt.
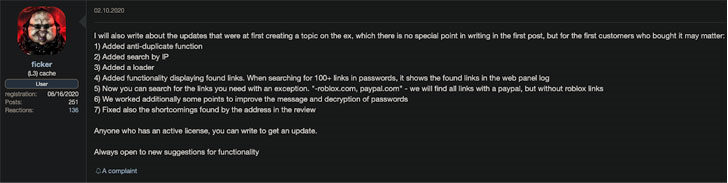
An example of ‘ficker’ MaaS. Source: Cybersecurity.re.kr
The last few months have seen a sharp increase in the activity of malware that specializes in loading/dropping second-stage malware: Emotet, Bazar Loader, IcedID, TrickBot, QakBot/SquirrelWaffle. A demand for such services is always high, especially before the holidays. With such worrying trends, it’s necessary for the defenders to focus on that specific threat, so that the following, more lethal, malware is not installed.
Arrival mechanisms and malware distribution channels
Most of the loaders employ very similar techniques of distribution. Namely, they are being spread via spam campaigns. The extent of the campaigns and sophistication of social engineering, on the other hand, differs.
Majority of malware operators leverage stolen email threads, so the messages themselves appear to be replies to existing email threads. They have been recently exploiting Microsoft Exchange servers using the ProxyShell and ProxyLogon vulnerabilities on a massive scale to do so.
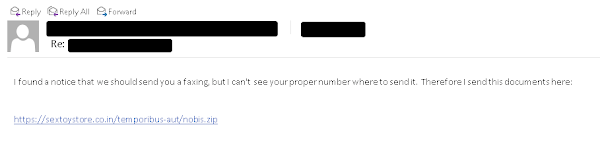
SquirrelWaffle phishing email example. Source: Cisco Talos Intelligence
These emails typically contain hyperlinks to malicious ZIP archives being hosted on attacker-controlled web servers. These consist of either malicious MS Word or Excel files that are embedded with VBS macros which execute PowerShell to retrieve and launch the loader.
Other exploitation vectors include running an obfuscated Microsoft HTML Application, which can execute VBScript and JScript, links to website contact forms or even using compromised software installers bundled with legitimate programs. In that regard, Bazar Loader is quite unique, they even used criminal call center (BazaCall) to deliver droppers that can bypass email security.
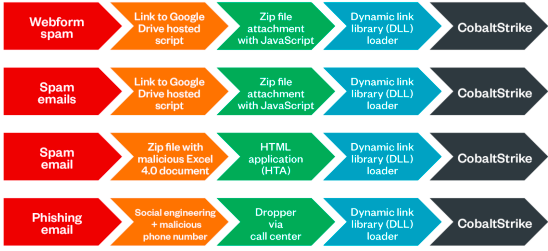
Some of the Bazar Loader’s known techniques. Source: trendmicro
These threat actors are constantly changing and improving their techniques making it harder for us to recognize their lure. However, almost every technique’s success is reliant on victim’s decision to click the link, ‘Enable the content’, download the file, etc.
Organizations must educate their employees about social engineering, and doing regular phishing simulations based on recent schemes used by threat actors.
Infection and Post-Infection – possibilities for detection
There is a myriad of infection methods for the attackers and it’s hard to list them all, but there are few that are quite common.
More often than not, maldocs use VBS macros which execute PowerShell to retrieve and launch the loader. The payload that is dropped on infected systems is often a PE DLL that is executed using either rundll32.exe or regsvr32.exe. Emotet, SquirrelWaffle/QakBot were observed performing such action.

SquirrelWaffle infection following the launch of malicious Excel file. Source: Sentinel Labs
To detect the infection using behavioral analysis, one might look for winword.exe or excel.exe spawning regsvr32.exe or rundll32.exe, which is abnormal.
Bazar Loader and IcedID operators often use MSHTA files. Given that there are very few cases in which MS Word should be spawning mshta, it makes sense to alert when winword.exe spawns mshta.exe.
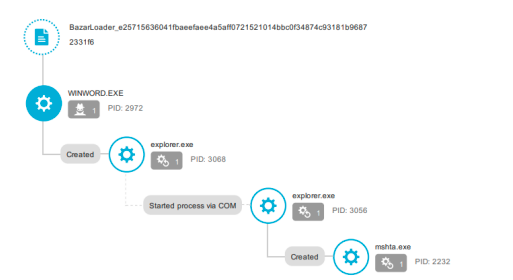
Bazar Loader malicious winword.exe spawning mshta.exe. Source: trendmicro
Process injection being a go-to technique for some operators, one should try to monitor for suspicious behavior of processes like lsass.exe and svchost.exe. These are common processes in general, therefore baselining normal against abnormal will be an important factor in fighting false positives.
For persistence, QakBot uses a scheduled task. The process it executes is regsvr32.exe, which is unusual. It presents another detection opportunity.

In the post-infection phase, attackers open connections to its C2s, that usually creates a lot of noisy, unnecessary traffic. Loader operators include several reconnaissance routines to profile victim’s environment for their ransomware affiliates. It helps malware operators filter out targets, which yield them no financial return. Blue Teamers could find suspicious behavior of msedge.exe that during the reconnaissance phase is very active. Additionally, looking for unexpected behavior of PowerShell commands running in the context of a browser process could be helpful.
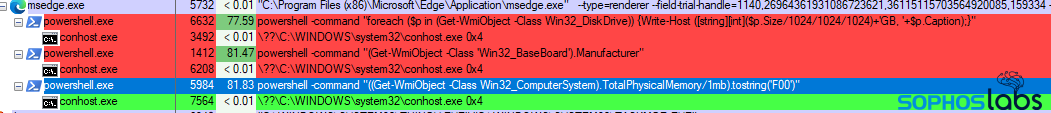
There is also a possibility for static detection, but it’s much harder to detect any new campaigns with already known indicators. Threat actors tend to change them often. Nevertheless, having a good feed with Indicators of Compromise (IoCs), which is updated daily, can prevent some of the attacks or detect some of the past compromises in the organization’s environment.
Abuse.ch is a research project that tracks and monitors malware and botnets (Bazar Loader, Dridex, Emotet, QakBot, TrickBot). Their platforms, such as FeodoTracker or ThreatFox, are reliable sources for receiving curated threat intelligence feeds that can be easily integrated with intrusion prevention/detection systems.
This is by no means an exhaustive list of detection techniques or recommendations. It is supposed to just give an idea on how to approach the issue. If the attackers constantly update their Tactics, Techniques and Procedures (TTPs) we, too, need to adapt.
Final steps of the droppers – an exemplar of cybercrime interconnectedness
Bazar Loader, QakBot, TrickBot, IcedID and even Emotet are not only loaders/droppers, but also very capable banking trojans or information stealers. At the beginning of their existence, they were usually used for stealing credentials and sensitive information, but recently they have started acting as a delivery mechanism for other malware, specifically ransomware. That might indicate how lucrative this business is.
Bazar Loader has been attributed by CrowdStrike to group Wizard Spider known for TrickBot, Ryuk and Conti ransomware. Bazar generally drops Cobalt Strike on the victim’s machine and gives access to second stage malware: Conti, Yanluowang, IcedID, TrickBot.
Emotet, before being taken down by law enforcement in January 2021, was dropping TrickBot and QakBot, which led to Ryuk or Conti. Few weeks ago, TrickBot was spotted dropping a loader for Emotet on infected devices, thus rebuilding its botnet and is now dropping Cobalt Strike immediately after the infection.
QakBot is a key enabler for ransomware attacks. Since 2019, infections have led to the eventual deployment of human-operated ransomware families (MegaCortex and PwndLocker in 2019, Egregor, and ProLock in 2020, and Sodinokibi/REvil in 2021, Lockean 2021).
IcedID was linked to Egregor deployments and RansomEXX.
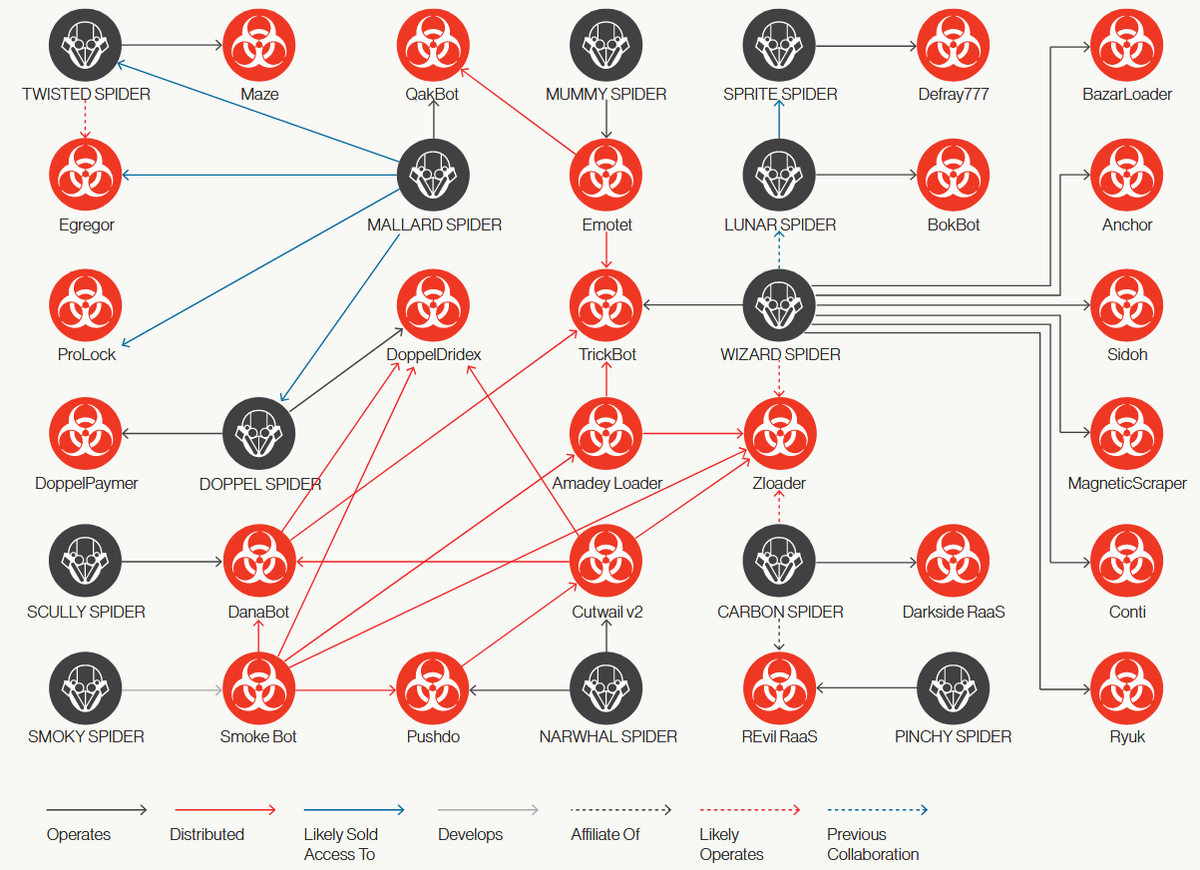
A net of cybercrime groups connections from February 2021. Source: CrowdStrike
By comparing the chart of cybercrime connections presented by CrowdStrike from February 2021, and the latest activity of malware operators, we see that it is constantly fluctuating. Nonetheless, we know for sure that their relationships with one another, as well as with other operators, are expanding. They enable each other in their campaigns, which makes sense from a business perspective – it increases the scope of possible victims. As demand outgrows the supply, we will likely see the trend continue.
Conclusions
Threat actors intensify their activity before Christmas, and it is most apparent on the Loader/Dropper scene. Malware operators increase volume of malspam campaigns in hope of getting access to valuable victims. If they are successful, it’s just one step before ransomware operators get access to the environment.
Organizations should increase their vigilance by anticipating phishing campaigns, learning about new techniques of malware delivery, and raising awareness among their employees.
Creation of detection rules based on threat actors’ TTPs increases organizational defensive capabilities as well. For preventive measure, organizations could integrate their solutions with timely and regularly updated intelligence feeds.
Maybe, with some more effort in preventing that type of malware we will be able to enjoy the holidays in peace.
Resources:
- https://www.bleepingcomputer.com/news/security/microsoft-exchange-servers-hacked-in-internal-reply-chain-attacks/
- https://www.bleepingcomputer.com/news/security/emotet-malware-is-back-and-rebuilding-its-botnet-via-trickbot/
- https://www.bleepingcomputer.com/news/security/qbot-returns-for-a-new-wave-of-infections-using-squirrelwaffle/
- https://www.bleepingcomputer.com/news/security/here-are-the-new-emotet-spam-campaigns-hitting-mailboxes-worldwide/
- https://www.bleepingcomputer.com/news/security/emotet-now-drops-cobalt-strike-fast-forwards-ransomware-attacks/
- https://blog.minerva-labs.com/a-new-datoploader-delivers-qakbot-trojan
- https://blogs.vmware.com/security/2021/07/icedid-analysis-and-detection.html#:~:text=IcedID%20is%20a%20three%20stages,foothold%20for%20further%20lateral%20propagation.
- https://www.crowdstrike.com/blog/wizard-spider-adversary-update/
- https://cybersecurity.re.kr/experts-shed-light-on-new-russian-malware-as-a-service-written-in-rust/#
- https://feodotracker.abuse.ch/browse/
- https://www.mandiant.com/resources/melting-unc2198-icedid-to-ransomware-operations
- https://www.microsoft.com/security/blog/2021/07/29/bazacall-phony-call-centers-lead-to-exfiltration-and-ransomware/
- https://news.sophos.com/en-us/2021/11/11/bazarloader-call-me-back-attack-abuses-windows-10-apps-mechanism/
- https://www.recordedfuture.com/business-fraud-laundering-fund-criminal-underground/
- https://redcanary.com/threat-detection-report/threats/dridex/
- https://redcanary.com/threat-detection-report/threats/emotet/
- https://redcanary.com/threat-detection-report/techniques/process-injection/
- https://securelist.com/trickbot-module-descriptions/104603/
- https://www.sentinelone.com/blog/is-squirrelwaffle-the-new-emotet-how-to-detect-the-latest-malspam-loader/
- https://www.splunk.com/en_us/blog/security/detecting-icedid-could-it-be-a-trickbot-copycat.html
- https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/yanluowang-ransomware-attacks-continue
- https://success.trendmicro.com/solution/1118391-malware-awareness-emotet-resurgence
- https://www.trendmicro.com/en_us/research/21/a/expanding-range-and-improving-speed-a-ransomexx-approach.html
- https://www.trendmicro.com/en_us/research/21/k/bazarloader-adds-compromised-installers-iso-to-arrival-delivery-vectors.html
- https://www.trendmicro.com/content/dam/trendmicro/global/en/research/21/k/bazarloader-adds-compromised-installers-iso-to-arrival-delivery-vectors/tb-bazarloader-looking-in-analyzing-the-infection-chains-stages-and-campaigns.pdf
- https://www.trendmicro.com/en_us/research/21/k/qakbot-loader-returns-with-new-techniques-and-tools.html
- https://thedfirreport.com/2021/11/29/continuing-the-bazar-ransomware-story/
- https://www.truesec.com/hub/blog/proxyshell-qbot-and-conti-ransomware-combined-in-a-series-of-cyber-attacks
- https://www.upguard.com/blog/what-is-egregor-ransomware
