Introduction:
Templates are pre-formatted documents, which contain specified information. A template engine is a specific kind of template processing module that exhibits all essential features of a modern programming language. Template engines are used by the developers to create web applications that display dynamic data. Embedding the malicious user input in templates, results in Server-Side Template Injection, a vulnerability that leads to Cross Site Scripting (XSS), Remote Code Execution (RCE) and many more.
If the application does not sanitize the user input, the application will be vulnerable to “Server-Side Template Injection” and give remote code execution (RCE) capability to the attackers. Sometimes, the full remote code execution is not possible but can result in other attacks, gaining read/write access to sensitive data and arbitrary files on the server.
Hence when the user input is embedded directly into the template, it may cause SSTI.
The following are the various templates used by different languages:
- PHP: Twig, Mustache, Blade, Volt, Dwoo, Smarty, VlibTemplate
- Java: Velocity, WebMacros, FreeMarker, Thymeleaf
- Python: Jinja2, Django, Genshi, Mako
Identifying SSTI Vulnerability
The first step is to identify if the template engine is vulnerable, and which template is in use.
Identifying a template engine can sometimes be easy/difficult by submitting payloads or invalid syntax in the user input, and the response or error message from the server would help in detecting the template engine used by the application. If the input concatenates with a server-side variable and renders it on the template, it’s an indication that the template is vulnerable to SSTI.
For example:
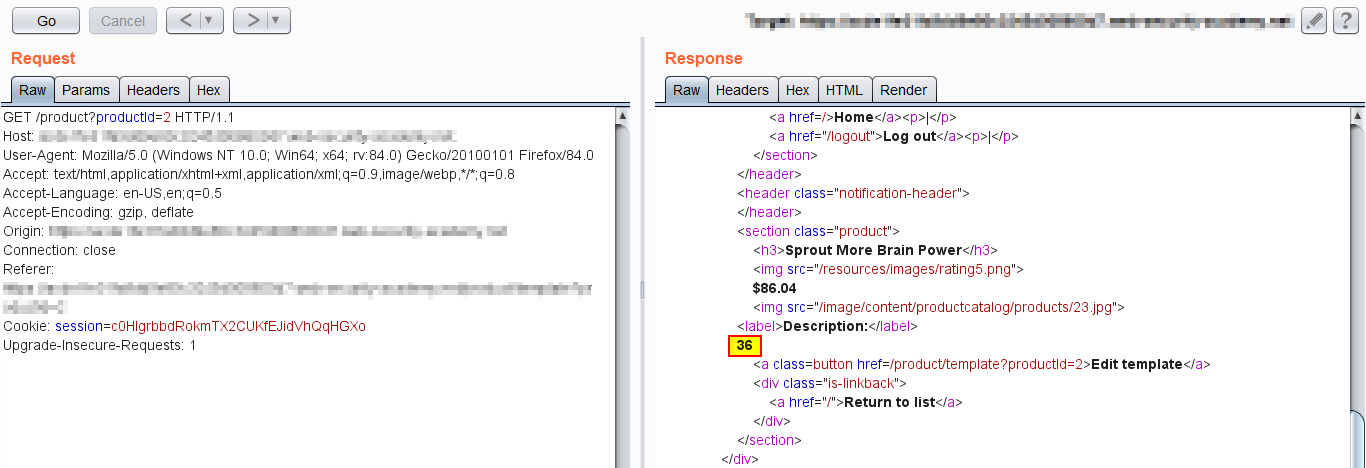
Step 1: Enter “${6*6}” as the value of the “template” parameter and click the “Go” button, as shown in the screenshot below.
 Step 2: The payload gets executed and the result is seen in the response as “36”, which shows that the template used is “Freemarker” and it is vulnerable on the server-side. This is shown in the following screenshot.
Step 2: The payload gets executed and the result is seen in the response as “36”, which shows that the template used is “Freemarker” and it is vulnerable on the server-side. This is shown in the following screenshot.
Exploiting the SSTI
There are multiple ways to exploit an SSTI vulnerability depending on the template engine in place. Once you know which template is in use and if it is vulnerable, then it is sometimes easy to exploit.
From the above example, it is identified that the template engine used by the application is “Freemarker”. According to the Freemarker documentation, there is a class, which executes arbitrary shell commands.
For example:
Step 1: Enter the payload shown in the following screenshot as the value of “template” parameter.
 Step 2: The following screenshot shows that the command was successfully executed and results with the file present in the path.
Step 2: The following screenshot shows that the command was successfully executed and results with the file present in the path.

XSS via CSTI
In CSTI attacks, special commands are enclosed between double brackets. Instead of HTML tags, use the following payload to perform XSS attacks:

Step 1: Enter the above payload as the value of “Username” parameter, as shown in the screenshot below.
 Step 2: The screenshots below show that it is possible to execute the JavaScript code without using html tags whenever the application is vulnerable to SSTI.
Step 2: The screenshots below show that it is possible to execute the JavaScript code without using html tags whenever the application is vulnerable to SSTI.


Mitigation:
- Input Sanitization and Output Encoding.
- Avoid using server-side codes.
- Filter the template expression syntax from user inputs before embedding it within server-side templates.
- HTML- encoding is not sufficient to prevent the attack because the frameworks perform HTML-decode.

By Shilpa N,
Associate Engineer and works on web application, thick client and API security.