Poorly configured S3 Buckets
A hacker’s delight
In today’s technological climate, finding the best way to store, share, and manage ever-increasing data sets is a huge challenge. As a result, storage requirements are growing every day. But establishing and managing your own data center is both costly and time-consuming. The process involves investing in extensive hardware and software resources, employing staff, and making your repository operational among other critical tasks. All of this is necessary to ensure data is securely backed up and your facilities are up to standard.
In addition to this, trying to determine the capacity that’ll be required in the future isn’t straightforward. Scaling means more time and monetary investments in extra resources. And it comes with no assurance of whether you have enough storage to meet your needs or whether you have excess capacity, meaning you’ll be overpaying.
As a solution for this, companies have been turning to cloud storage services, such as Amazon S3 buckets, to store and retrieve data. But the buckets need the correct configuration to prevent data breaches and any form of unauthorized access.
The following article explains what an S3 bucket is and the impacts of a poorly configured one.
1) What are S3 Buckets?
An S3 bucket is a public cloud storage resource available in Amazon Web Services (AWS) that offers scalability, data availability, security, and performance.
2) What type of data and how much of it can be stored on AWS S3?
Virtually any type of data, in any format, can be stored in S3. In terms of capacity, the volume and number of objects that can be stored in S3 are unlimited. An object is the fundamental entity in S3. It consists of data, keys, and metadata.
There are two types of data:
- Data, which will be accessed frequently
- Data, which will not be accessed frequently.
3) What are the different types of S3 buckets and why do companies use them?
There are two types of S3 buckets:
- Public – There are no access restrictions so the bucket can be accessed by anyone
- Private – Only permitted users can access the bucket.
Companies mainly use S3 bucket to store their backups, confidential files, source codes and so on. Due to its user-friendly interface, it can also be used for application hosting, fileserver and media hosting, and software delivery as well.
4) What does a bucket look like and where can it be found?
Below are examples of what a typical bucket would look like.
- http://<bucketname>.s3.amazonaws.com
-or-
- http://s3.amazonaws.com/<bucketname>
A bucket can be found in the source code as well.
There are many tools available to find such buckets and they mostly use the brute force approach to predict the name of the buckets. One of the tools that provide the bucket name is “AWS Extender”, which is used in conjunction with “Burp-Suite”.
Upon receiving the bucket name, it is possible to exploit it if it’s not correctly configured. “AWS CLI” further facilitates this exploitation process.
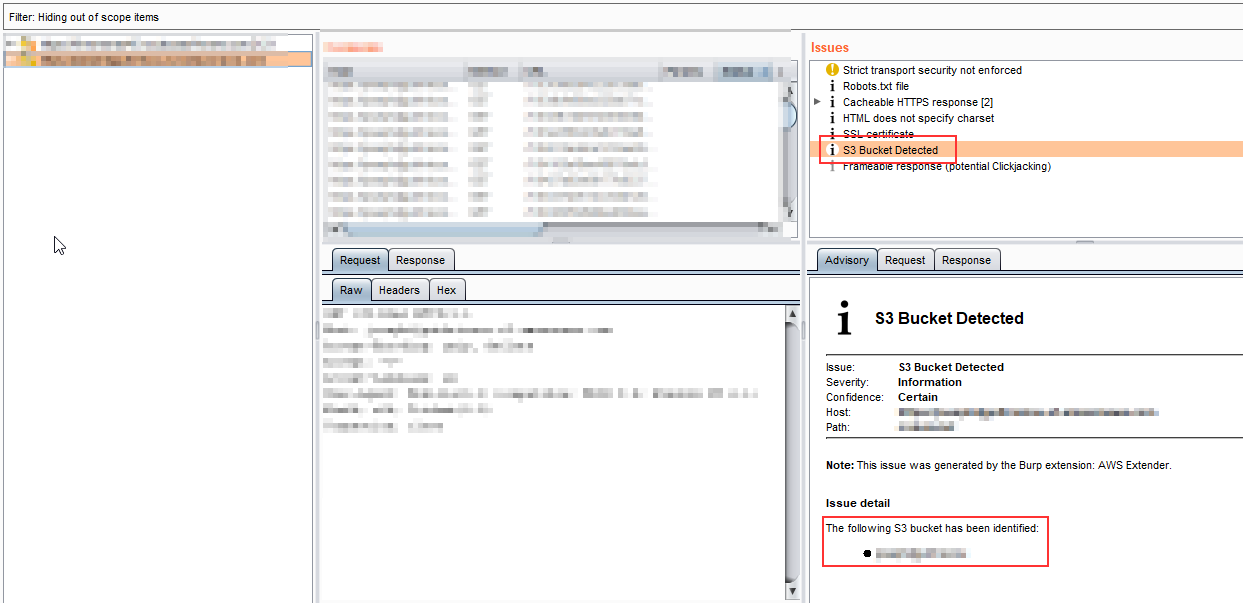
There are many tools available to find such buckets and theymostly use the brute force approach to predict the name of the buckets. One of the toolsthat provide the bucket name is “AWS Extender”, which is used in conjunction with “Burp-Suite”.
Upon receiving the bucket name it is possible to exploit it if it’s not correctly configured. “AWS CLI” further facilitates this exploitation process.
5) The impact of a poorly configured bucket
The impact of misconfiguration depends on the bucket’s contents. If the bucket has sensitive data, the attacker can:
- Dump the data of the Bucket (Data Breaches)
- Compromise the Integrity of files
- Remove files from the Bucket
- Upload Malicious files into the bucket.
6) What does a poorly and a correctly configured bucket look like?
Poorly Configured bucket
Correctly Configured Bucket
Recent Case Studies
In the past year, there have been a number of data breach reports about Amazon S3 in particular. Servers were illegally accessed online, which exposed confidential corporate and customer information. The cause of data breaches mostly came down to human error. In nearly all cases, S3 buckets had been mistakenly configured to allow “public” access. In effect, this meant that anyone with a link to the S3 server could access, view, or download its content.
The most recent data breaches that occurred via S3 Buckets were Capital One and Netflix data breach.

7) How can you secure your S3 bucket?
To secure your S3 bucket you can do any of the following:
- Apply whitelisting rather than blacklisting (list a few people who should have access): only give access permissions to the processes or individuals who absolutely need them
- Limit those with write permissions. Never give write permissions to everyone
- Block Access. Account administrators can also block public access to prevent anyone in their account from opening a bucket to the public, regardless of the S3 bucket policy
- Implement the correct ACL list
- Implement the Bucket Policy correctly.
