Misconfigured firebase: A real-time cyber threat
Every day, we hear about customer data being compromised, data posted on the dark web for sale, or a similar cybersecurity breach. Database compromise is the main reason for this. There might be several reasons for database being compromised: “SQL Injection” being the most common reason. In this blog, we will see “How a misconfigured Firebase database” can lead to data compromise of millions of users.
So, what is Firebase Realtime Database?
As per Google, The Firebase Realtime Database is a cloud-hosted NoSQL database that lets us store and sync data between the users in real-time. The real-time data may include live feeds, sign-in logs, customer chats, application logs, user details, and much more. Firebase is widely used by the developers because of user-friendliness and scalability.
Why has it attracted hackers?
Since Google has started giving free credit (up to $300) to the new users, it has given an open platform to all the developers to use Google cloud products in their application. Amongst all the products, Firebase is most widely used. Small scale companies and new start-ups have started using Firebase to reduce cost. Firebase is easy to integrate with Android applications, iOS applications, and web applications. It provides several features like “Cloud Storage,” “Hosting,” “Real-Time Database,” and “Crashlytics.”
There are different settings for different features, but our prime focus is on the “Database” settings. By default, the database settings are private. To use the database in real-time, we need to define the read and write access for the database that we want to use. So, let us first see how a properly configured firebase and a misconfigured firebase database looks like.
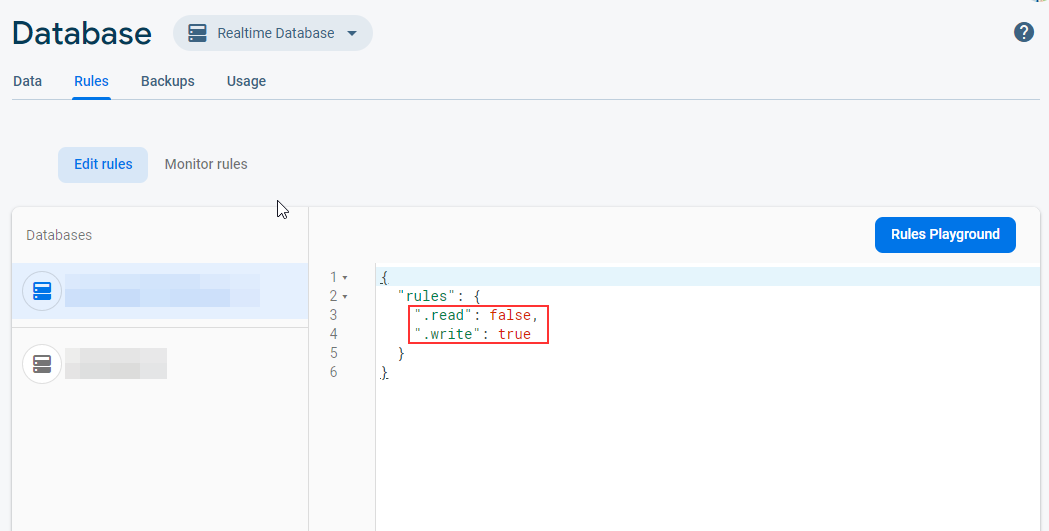
Properly Configured Firebase: By default, the database settings for a database are read and write protected, meaning the read and write access is not allowed. To store real-time data, write access to the database must be enabled by setting the “write” flag to “true.” Remember, that read access is still disabled, and the “read” flag is set to “false,” as shown in the following screenshot.
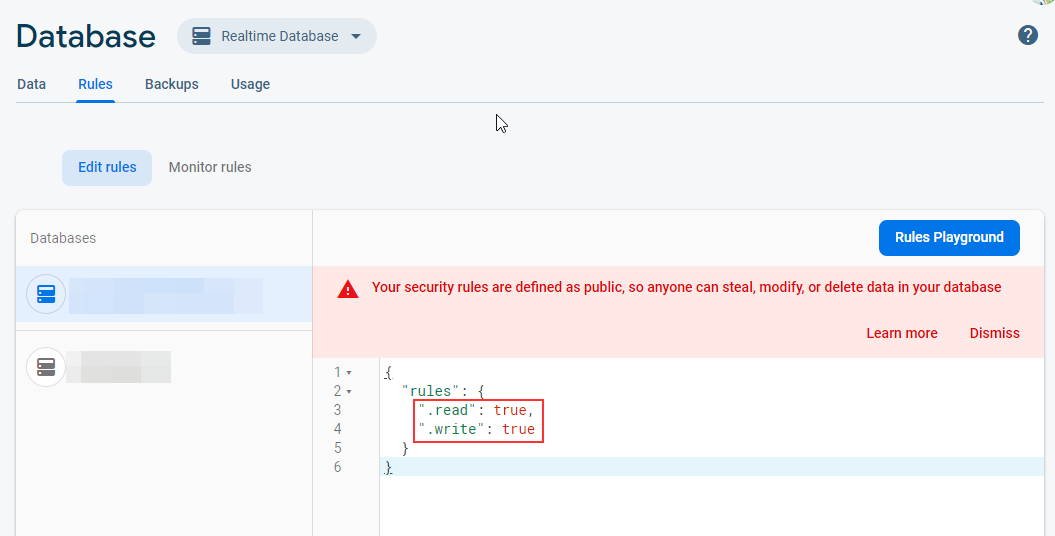
Misconfigured Firebase: While testing the functioning of the database and checking the flow of data, developers often make the database public. They set the value of both “read” and “write” flag to “true.” If the “read” flag is set to “true,” it means that an adversary can read the content of the database without any authentication. This will be demonstrated in the “Exploitation” section. The following screenshot shows the misconfiguration.
How to check if an application uses Firebase?
Before checking for misconfiguration, we should first find out if an application uses Firebase or not. Firebase is used in web, Android, and iOS applications, but the detection mechanism for all three are different.
A typical Firebase database URL looks like https://xyz.firebaseio.com/
where “xyz” is the real-time database name.
For Web applications: We need to search the source code using the keyword “firebaseio,” or we can also spider the complete website using a tool like “Burp Suite Professional” and then do a keyword-based search.
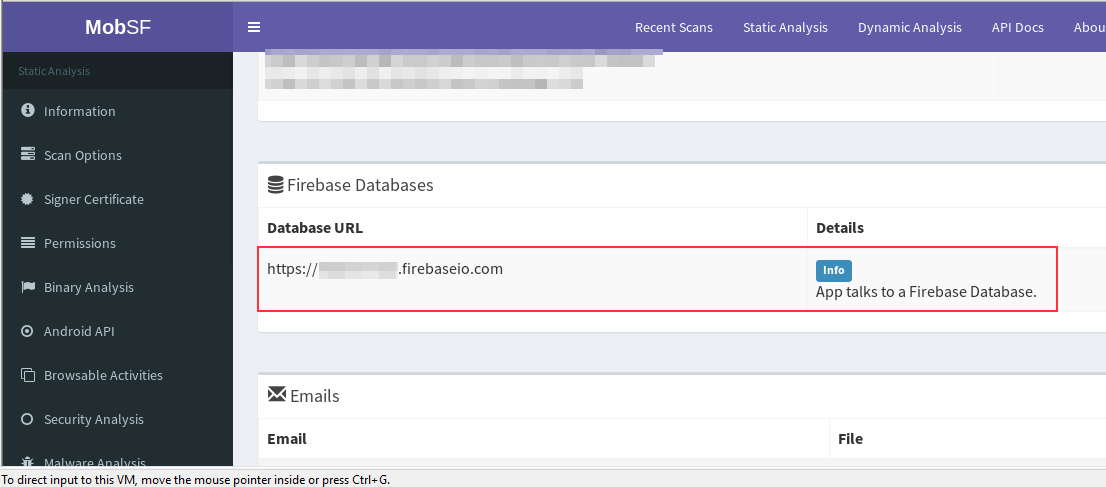
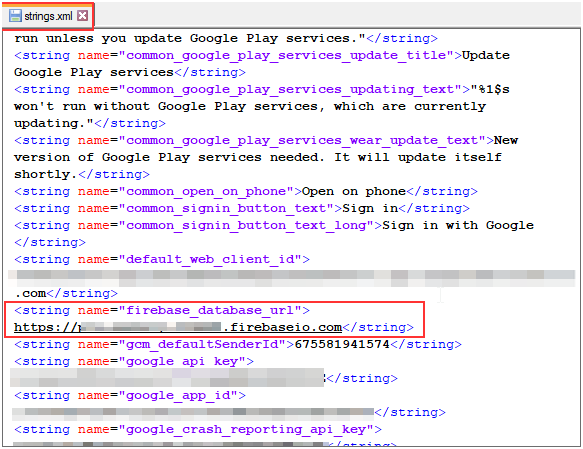
For Android applications: We can do an automated MobSF scan on the “apk,” and this will directly give us the URL in the scan output. Or we can also decompile the apk and navigate to “res -> values -> strings.xml” file and do a keyword search to find the database URL.
For iOS applications: We can do an automated MobSF scan on the “ipa” and this will directly give us the URL in the scan output. Or we will need to look for the URL in the “plist” files.
The following screenshots show the Firebase URL.
Firebase URL in MobSF report
Firebase URL present in the “strings.xml” file
Once we get the real-time database link, we can now check its configuration. Now, we will see how a misconfigured database can end up leaking valuable information.
How to exploit a misconfigured Firebase?
Once we get the Realtime database URL, we can check the configuration by appending .JSON after the URL.
For instance, if the Firebase URL is https://xyz.firebase.com/ , we have to append .JSON after the URL. So the final URL becomes https://xyz.firebaseio.com/.json. Paste this URL in the web browser. If we get an error message stating, “Permission denied,” this means that the database is configured correctly. The following screenshot shows a properly configured database.

But, if we paste the URL and the database contents are displayed, this means that the read access is “Public” on that database, and the data is visible to anyone with the database link. Since the information is stored in “JSON” format, it can be easily copied. The following screenshot shows a misconfigured Firebase database, which is leaking data.
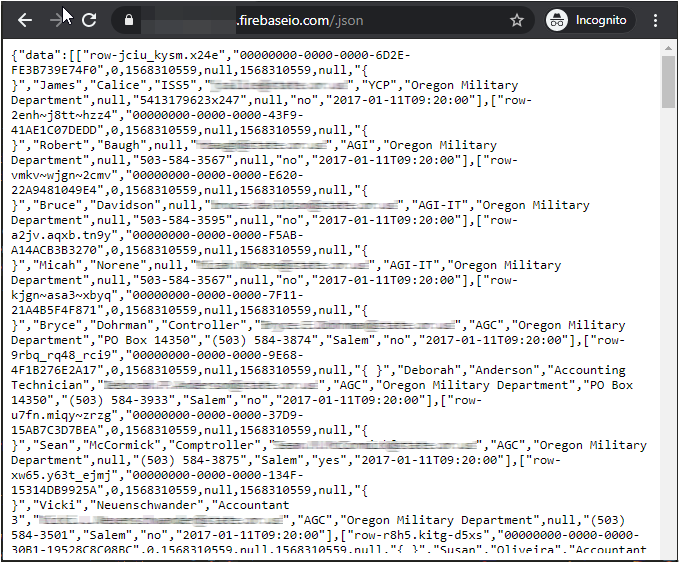
A simple human error might end up leaking data of millions of users.
Recent case studies:
According to the recent case study, the following data was compromised via a misconfigured Firebase.
The full contents of the database, spanning across 4,282 apps, included:
- Email addresses: 7,000,000+
- Usernames: 4,400,000+
- Passwords: 1,000,000+
- Phone numbers: 5,300,000+
- Full names: 18,300,000+
- Chat messages: 6,800,000+
- GPS data: 6,200,000+
- IP addresses: 156,000+
- Street addresses: 560,000+
Source: The Hacker News.
How to secure a Firebase database?
The following points must be kept in mind while setting up the real-time database:
- Authentication: Only authenticated users must be allowed to read/write data in the database. User identity is critical as there could be different types of users holding different kinds of data. A proper authentication policy must be implemented to provide unauthorized access.
- Authorization: Proper “Read” and “Write” access must be configured on all the databases. Configurational errors must be avoided. Documentation must be followed before making any configurational changes.
- Data validation: Validation rules must be defined to avoid junk/garbage data before writing the data in the database.
Source: Firebase Data Security
