Distributed Denial of 2023?
Introduction
Geopolitical events often trigger cyberattacks by state-sponsored Advanced Persistent Threat (APT) groups and hacktivist organizations. Hacktivists usually resort to Distributed Denial of Service (DDoS) attacks worldwide. Therefore, it is essential to analyze the European cyber environment to gain insights into the following information:
- The number of cyberattacks that have been executed,
- The countries that have been targeted the most,
- The groups responsible for the majority of these attacks.
This summary is based on data due to December 13, 2023
Anonymous Sudan (Storm-1359) campaign against Microsoft
In the year 2023, one of the most significant and widely recognized Distributed Denial of Service (DDoS) attacks was orchestrated by the Anonymous Sudan group against the United States.
The primary target of the attack was Microsoft, which was attacked multiple times during the campaign that spanned from June to July. The DDoS attacks carried out by Anonymous Sudan in 2023 resulted in significant disruptions and downtime for services, which could lead to financial losses and reputational damage for the affected companies. The attacks targeted several high-profile US companies, including Microsoft, and were carried out using a range of techniques, including HTTP(S) flood attacks, cache bypass, and Slowloris. Microsoft suffered multiple attacks on its various subdomains, including signup.live.com, onedrive.live.com, and portal.azure.com, causing service outages and disruptions.
Between June 2, 2023, and June 9, 2023, the Anonymous Sudan group claimed responsibility for several DDoS attacks targeting several US companies. They launched the #FUCK_AnthonyBlinken and #FUCK_USA campaigns, which resulted in several entities being targeted on specific dates.
On June 7, 2023, the single-sign-on portal for Microsoft, signup.live.com, was targeted. On June 8, 2023, Microsoft OneDrive, onedrive.live.com, was the victim of the attack, and on June 9, 2023, Microsoft Azure, portal.azure.com, was targeted.
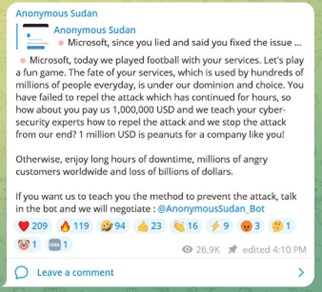 Figure 1 Anonymous Sudan post about attacks on Microsoft
Figure 1 Anonymous Sudan post about attacks on Microsoft
Between the 14th and 21st of July in the year 2023, Anonymous Sudan claimed responsibility for targeting several entities located in the United States, Israel, and the United Arab Emirates. This was done in conjunction with their #FUCK_AnthonyBlinken, #FUCKUAE, #FUCKISRAEL, and #FUCK_USA campaigns, which were aimed at these entities.
On the 21st of July 2023, Anonymous Sudan targeted Microsoft Azure and several of its subdomains, portal.azure.com, in the United States.
Between the 7th and 14th of July in the year 2023, Anonymous Sudan claimed responsibility for targeting several prominent social networking and fanfiction entities in the United States, as well as Dutch entities. This was carried out in conjunction with their #FUCK_AnthonyBlinken, #FUCKNATO, and #FUCK_USA campaigns. Anonymous Sudan stated that their primary motivation was to target any American company regardless of their identity.
On the 14th of July, 2023, Anonymous Sudan, in collaboration with SkyNet, allegedly carried out a DDoS attack on Microsoft OneDrive, onedrive.live.com. This was a repeat of a previous attempt on June 8th, 2023.
It is worth noting that during the DDoS attacks that occurred between the 14th and 21st of July, 2023, Anonymous Sudan claimed to have access to the credentials of 30 million Microsoft users. However, Microsoft has not confirmed this breach.
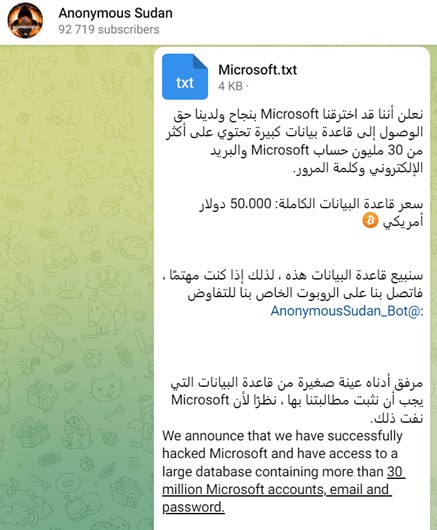
Figure 2 Anonymous Sudan post on Telegram channel related to stealing Microsoft users accounts
Methodology
Possibilities for gathering the statistics
There are various ways to collect information about potential victims of DDoS attacks. However, relying on an announcement from the victim might not be the best option since DDoS attacks often lead to financial and reputation losses, and victims may not want to announce their situation. Our team at Eviden TI noticed that many victims do not report attacks on their infrastructure or claim that they are internal issues to avoid embarrassment.
One effective way to gather information is by joining Telegram DDoS groups and collecting victims by top-level domain (TLD). This method may not work for every group, as some use the check-host.net website to verify their victims. Another way is to collect mentions of the country name in Telegram DDoS groups, as this has proven to be an effective solution to get statistics of attacked countries. We can count the mentions of the country name and get a fairly accurate estimate of the number of DDoS attacks on victims in that country. However, this method may not work when the group only posts links of victims or check-host.net without any context.
In conclusion, while there are some limitations to each method, we can gather useful information by using a combination of these methods. By doing so, we can get a clearer picture of DDoS attacks and take necessary actions to prevent them.
Counting the mentions
In the context of detecting Distributed Denial of Service (DDoS) attacks, this article presents a comprehensive solution efficiently and effectively. The solution involves a combination of the second and third options, which includes scanning group content and counting mentions of the country with additional keywords that are tailored to every group based on extensive research. This process is highly targeted and efficient, as it enables the detection of DDoS attacks based on specific keywords that are relevant to the channel being scanned.
The use of additional keywords in detecting DDoS attacks ensures that the scanning process is more accurate and effective. For example, the presence of URL links (such as check-host.net) can be used as a keyword in some channels, while the name of a group or project (such as DDosia, or DDoS) can be used in others. The selection of these keywords is dependent on the channel being scanned, as it provides a more tailored approach to the scanning process.
Overall, our solution provides a highly effective means of detecting DDoS attacks and by using a tailored approach that combines the second and third options, we can confidently say that our scanning process is accurate, efficient, and effective in detecting DDoS attacks.
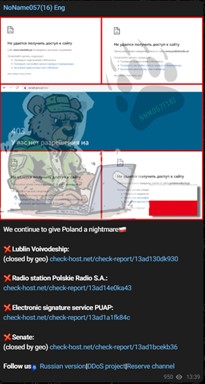 Figure 3 Example announcement from NoName057(16) on English channel about attack on Polish entities
Figure 3 Example announcement from NoName057(16) on English channel about attack on Polish entities
Telegram has emerged as a popular platform for group marketing
DDoS groups utilize Telegram extensively as their primary platform of activity. Attackers leverage Telegram to post detailed information related to their latest victims, including the reasons behind their attacks. This platform is also extensively used as a place to issue threats and announce larger campaigns, some of which include #OP_FRANCE and #FUCKNATO.
The widespread usage of Telegram by attackers makes it a rich source of information about threat actors. This article is based on information sourced from Telegram, which was scraped and then extensively reworked to analyze and understand the activities of these threat actors. The statistics presented in this article are based solely on the information gathered from Telegram and analyzed for the purpose of this report.
Python vs DDoS
The process of analyzing raw data that has been scraped from Telegram involves various steps. Using Python notebooks is a useful approach, which can be run either in Visual Studio or Jupyter Notebook. The primary container for the data is the Pandas DataFrames, which can be used to filter and process the collected data. In this article, we will see the final result of processing the data which is the data in chart form.
To begin, we need to extract the text content of the channels, which can be achieved via scripting in Python. Once we have the text content, we can analyze the desired messages by filtering (e.g. only the ones from 2023) and counting them. The entire process is carried out using Python notebooks, which offer more flexibility and possibilities for testing and working with the results until we get the desired output.
With this approach, we can easily manipulate and analyze the data to obtain valuable insights. By using Python notebooks, we can quickly identify any problems and results and easily solve them. Overall, this approach helps to streamline the data analysis process, making it more efficient and effective.
 Figure 4 Piece of the keyword list that has been used
Figure 4 Piece of the keyword list that has been used
Analysis of DDoS attacks
Quick Glance
An evaluation of the data has provided a comprehensive overview of the DDoS attacks that transpired during 2023. As per the presentation in Table 1, the group NoName057(16) conducted the most significant number of attacks (1158), while the second-highest number of attacks was carried out by Mysterious Team Bangladesh, an Indian-based group. It is worth noting that the table only accounts for those attacks that impacted victims associated with European countries.
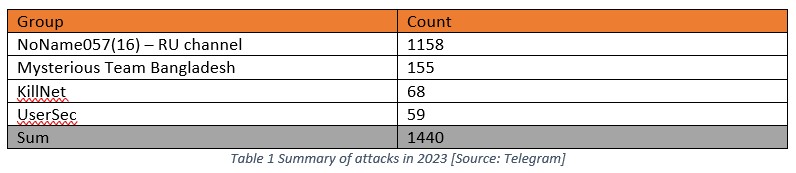
Table 2 provides a summary of the Top 7 countries that were targeted by DDoS groups in 2023. It is noteworthy that the NoName057(16) group was responsible for a significant proportion of these attacks, as highlighted in Table 1. This group has conducted the highest number of attacks in 2023, making it a key contributor to the overall count. Given these findings, it is important to acknowledge the impact of the NoName057(16) group in this summary.
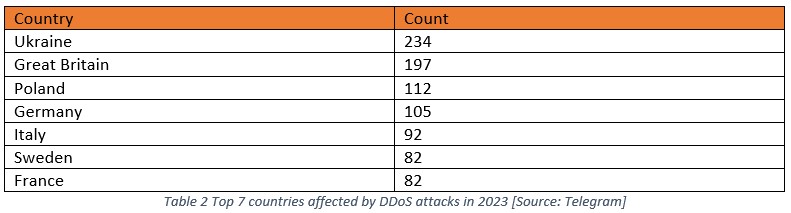
In the upcoming section, a comprehensive summary of the attacks carried out by each group will be presented. It should be noted that the distribution of attacks across different countries varies based on the origin of the group. This information is pertinent and may be of interest to an external audience seeking to understand the nature and extent of DDoS attacks in 2023.
UserSec
 Figure 5 UserSec Telegram channel information pane
Figure 5 UserSec Telegram channel information pane
The hacktivist group known as UserSec, began its operations in 2022, according to Malpedia. However, the group’s first post on the channel dates back to January 2023. UserSec is primarily involved in conducting DDoS attacks and in 2023, it joined forces with KillNet in a campaign aimed at targeting NATO member countries. These facts are also mentioned on the group channel’s information pane on Telegram [Figure 3].
On May 17th, 2023, UserSec’s founder, user1 (hidden account), posted a brief description of the group on their Telegram channel. He shared the group’s origin and goals and stated that the group was created in January 2023 by a lone hacker. As per his statement, UserSec is a group working for the good of Russia, and it conducts attacks on Europe, the West, and all NATO countries. These attacks can range from hacks to DDoS attacks and deface.
The UserSec group channel contains 59 posts mentioning attacks on European entities [Figure 4]. These attacks are highly correlated with information about countries supporting Ukraine in the war with Russia. Furthermore, most of the attacks are targeted at NATO member countries. As mentioned earlier, UserSec joined a campaign whose primary objective is to attack NATO members. Notably, only two countries in the given data are not members of NATO (Sweden and Ukraine).
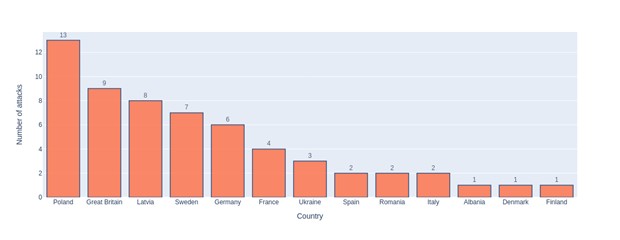 Figure 6 UserSec attacks on European countries in 2023
Figure 6 UserSec attacks on European countries in 2023
The Insikt Notes released by Recorded Future about DDoS groups’ activity suggest that the #FUCKNATO hashtag can be used to identification of a specific campaign in which the UserSec group takes a part. It is worth mentioning that some of the attacks are conducted with other groups, which can suggest that UserSec may not be capable of conducting large-scale DDoS attacks. Alternatively, it may indicate that they have a loose organizational structure and consist of other groups.
 Figure 7 UserSec in cooperation with other groups carried attacks on Italian, Ukrainian, and Swedish entities in July 2023
Figure 7 UserSec in cooperation with other groups carried attacks on Italian, Ukrainian, and Swedish entities in July 2023
UserSec is interested in collaborating with others to conduct large-scale attacks, which may be indicative of their limited capabilities to strike alone. During 2023, they combined forces with AnonymousSudan and KillNet, and as a result of this cooperation, many smaller groups have been encouraged to join the ranks of UserSec. On October 30th, 2023, the UserSec group announced the launch of their DDoS-for-hire service. They are among the few groups that offer such a service, including NoName057(16). This may suggest that UserSec has collected sufficient resources by the end of the year to work more independently.
NoName057(16)
NoName057(16) began its activity in 2022. Their first post on Telegram was made on March 11th, 2022, and it provided a short explanation of their objectives, targets, and motives. They also stated that the channel will be used to share information about their activities. Throughout their entire operation, NoName057(16) frequently changed their targets. However, their primary focus has been on attacking Ukraine and NATO members. They usually target critical sectors like transportation or banking.
The group uses Telegram daily to announce their attacks, make threats, and share information. They have two primary channels: one for Russian-speaking users and another for English speakers. The content of these channels is somewhat different. The English channel includes only information related to attacks, while the Russian channel also includes some news updates. Furthermore, the English channel lacks an “Introduction” message, and the first post was made on March 11th, 2022.
Figure 8 NoName057(16)eng and NoName057(16) Telegram channels information panes
This group is known for its support of Russia. They target Russia’s enemies and react to any news related to the war in Ukraine. The group first came into the spotlight at the start of the war and has conducted many operations since then.
During the year 2023, there were 1158 reported attacks on European entities, and the Russian channel was the primary source of information for these attacks. The channel was chosen because the English channel failed to translate and share some crucial information about these attacks. This discrepancy is evident when comparing the statistics provided by Telegram and the check-host[.]net link shared by the group for every domain they attack.
The NoName057(16) group uses the check-host[.]net domain to prove their actions, as it allows anyone to check the connection from anywhere in the world. The English and Russian channels show a significant imbalance in the number of attacks reported, indicating that the Russian channel was the preferred source for sharing this information. This raises concerns about the reliability and accuracy of the information shared by the channels and their sources.
Based on the gathered data, it appears that the majority of attacks have been carried out against Ukraine. Great Britain (mostly assumed to mean England) comes in second place, and Poland, which is Ukraine’s neighbor and first supporter since the start of the war, comes in third place [Figure 7]. Additionally, many of the victims are members of NATO, which, according to information from Recorded Future, may be related to the fact that the group has joined the campaign #FUCKNATO.
It seems that NoName057(16) does not collaborate extensively with other groups. This could indicate that the group is confident enough to operate independently. Additionally, they have been working on improving their tools for carrying out more effective DDoS attacks as a part of the DDosia project.
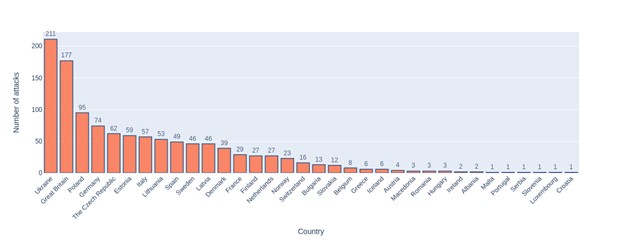
Figure 9 NoName057(16) attacks statistics on European countries in 2023
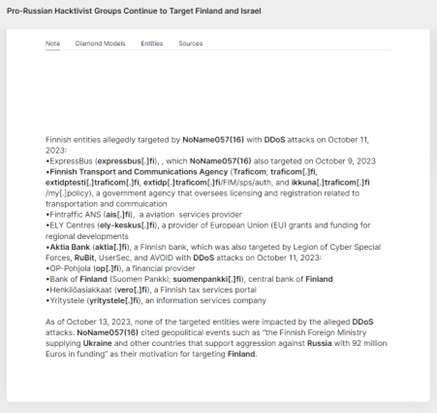 Figure 10 NoName057(16) notes about attacks on Finnish entities in October 2023
Figure 10 NoName057(16) notes about attacks on Finnish entities in October 2023
KillNet
In February 2022, a Russian hacktivist group called KillNet became operational. Although it has not been confirmed that they have links to Russian government organizations like FSB or SVR, KillNet is known for conducting DDoS attacks. The group initially mocked Anonymous, a famous hacktivist group, by calling them a USA-linked group. KillNet’s primary target is Ukraine, as well as its supporters and NATO members. They often collaborate with other DDoS groups to conduct more destructive attacks. After the group conducted attacks on Latvian Parliament Web Services, they were labeled as a terrorist organization by Latvia.
 Figure 11 KillNet Telegram channel information pane
Figure 11 KillNet Telegram channel information pane
They commonly target government organizations, military agencies, healthcare institutions, and financial institutions.
KillNet has a strong presence on Telegram and DarkWeb. They use multiple channels on various social media platforms not only to share information about DDoS attacks but also to spread Russian propaganda. The group is led by a Russian citizen named Nikolai Nikolaevich Serafimov, also known as KillMilk, who is 30 years old. However, it is suspected that the group has more than one leader to coordinate their activities.
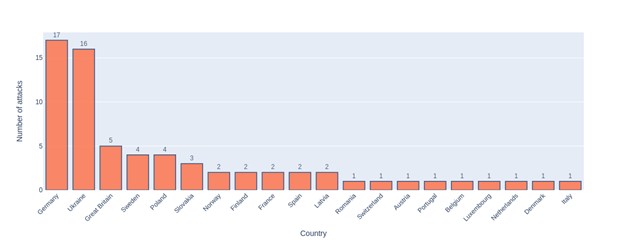 Figure 12 KillNet attacks statistics on European countries in 2023
Figure 12 KillNet attacks statistics on European countries in 2023
In 2023, KillNet, a notorious cybercriminal organization, carried out a relatively low number of attacks. However, the targets of these attacks were of particular significance. KillNet’s attacks were primarily aimed at NATO members and countries that supported Ukraine in their war with Russia. This suggests that KillNet may have been working in service of a larger political agenda.
It’s worth noting that KillNet’s activities were not limited to direct attacks. The organization also conducted various disinformation campaigns across social media platforms about the DDoS attacks that never took place. These campaigns were designed to spread false information, sow discord, and manipulate public opinion. While these campaigns did not involve any real-world actions, they were still a significant threat. Furthermore, KillNet’s attacks were not limited to targeting country entities. The organization also carried out attacks against specific companies and brands.
Overall, KillNet’s activities in 2023 paint a complex picture of a cybercriminal organization with multiple motives and methods.
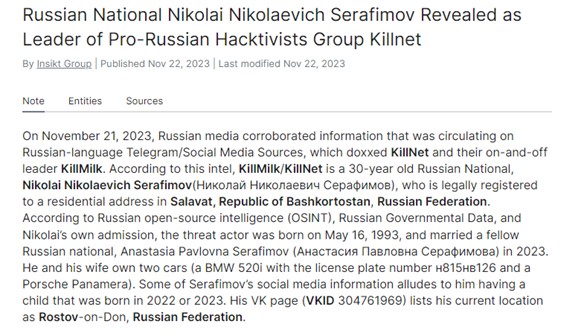 Figure 13 Snippet from Recorded Future Analyst Note about revealing the identity of KillNet leader
Figure 13 Snippet from Recorded Future Analyst Note about revealing the identity of KillNet leader
Mysterious Team Bangladesh
According to intelligence reports, Mysterious Team Bangladesh is a cybercriminal group that is believed to be based in Bangladesh and has launched several attacks on European countries. Although their motives are not entirely clear, it is believed that the group’s actions are mostly driven by geopolitical tensions and a desire to react to political situations. As a hacktivist group, they appear to be driven by ideological motives and may be driven to action by any attacks on the Islamic population. It is worth noting that the group has been involved in several campaigns, and their targets are not limited to Europe.
 Figure 14 Mysterious Team Bangladesh Telegram channel information pane
Figure 14 Mysterious Team Bangladesh Telegram channel information pane
In June of 2022, a Telegram group was created that has since engaged in various hacking activities. The group began by sharing posts about their activities, and it was not long before they started conducting DDoS attacks. Although the group has targeted entities located in different parts of the world, most of their victims are based in India.
In addition to their activities in India, the group has also taken part in several campaigns outside the country. For instance, they launched OpSweden/FckSweden in response to the burning of the Quran, which they viewed as a disrespectful act against Muslims. They also conducted OpAustralia, which aimed to draw attention to a fashion show that was deemed offensive to Muslims. Additionally, the group launched OpFrance in response to political tensions in Niger, which they believed was a result of French interference.
According to a recent group post, there is currently a highly relevant campaign focused on Israel and its allies. The post suggests that all of Israel’s allies are offering their support in military intervention in Gaza called by Mysterious Team Bangladesh as genocide.
As can be confirmed in Figure 13 group does not conduct many operations against European entities and can be classified as an opportunistic group that only temporarily focuses on Europe as its target.
 Figure 15 Mysterious Team Bangladesh attacks statistics on European countries in 2023
Figure 15 Mysterious Team Bangladesh attacks statistics on European countries in 2023
The Mysterious Team Bangladesh is primarily focused on preparing and conducting DDoS attacks. However, in some cases, they also carry out data exfiltration. Even though the group performs data exfiltration, their main activity should be recognized as DDoS attacks. The impact of DDoS attacks can be severe, as they can disrupt the operations of an entire organization, causing financial losses and reputational damage.
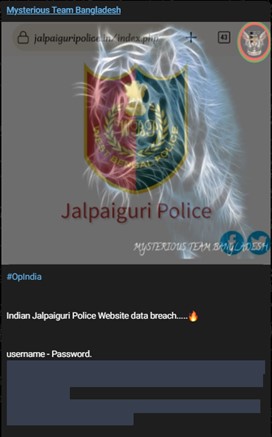 Figure 16 Mysterious Team Bangladesh breached Indian Police Website
Figure 16 Mysterious Team Bangladesh breached Indian Police Website
Summary
In the year 2023, Distributed Denial of Service (DDoS) attacks continued to pose a significant threat to European countries. These attacks were carried out mainly by Russian-linked groups, which targeted entities supporting NATO or Ukraine. It is worth noting that some opportunistic actors also carried out attacks in response to political tensions.
The groups that conducted these attacks relied on both individual and cooperative efforts. The campaigns against pro-Ukrainian countries were particularly noteworthy, as they involved merging groups into the same enemy, allowing for more destructive attacks. These attacks were conducted with a high level of sophistication.
It is important to understand the consequences of a DDoS attack. Every such attack causes financial and reputational losses to the affected company. This is likely one of the reasons why victims tend to provide limited information about being targeted by such attacks. In addition, the attacks can cause significant disruptions to the normal functioning of the targeted system.
In conclusion, the threat of DDoS attacks should not be taken lightly. As technology continues to evolve, attackers will likely find new and more sophisticated ways to carry out these attacks. Therefore, it is important to remain vigilant and take proactive measures to ensure the security of our systems.
Sources:
Table 1: Telegram
Table2: Telegram
Figure 1: https://www.bleepingcomputer.com/news/microsoft/microsoft-confirms-azure-outlook-outages-caused-by-ddos-attacks
Figure 2: https://securityaffairs.com/148119/hacktivism/anonymous-sudan-claims-stolen-microsoft-data.html
Figure 3: English channel
Figure 4: Own source
Figure 5: Telegram
Figure 6: Telegram
Figure 7: https://app.recordedfuture.com/portal/analyst-note/shared/true/doc:r6dz86
Figure 8: Telegram
Figure 9: Telegram
Figure 10: https://app.recordedfuture.com/portal/analyst-note/shared/true/doc:s_2JCQ
Figure 11: Telegram
Figure 12: Telegram
Figure 13: https://app.recordedfuture.com/portal/analyst-note/shared/true/doc:tgqG7k
Figure 14: Telegram
Figure 15: Telegram
Figure 16: Telegram


