Cl0p Ransomware Group activity related to data leaks from GoAnywhere MFT
The essentials
- The Threat Actor TA505 is deemed as a trendsetter for its ever-changing tactics, techniques, and procedures (TTPs)
- It targets numerous countries, but it omits close allies of Russia.
- Is known to use quadruple extortion techniques – including targeting executives and contacting customers to add pressure to pay the ransom
- Latest campaign saw at least 132 companies breached in some way, with 12 already having their data exposed on the darknet
Recommendations
- Create detection rules based on the groups’ TTPs and IoCs
- Block the infrastructure (C2s, domains, hashes) of the operators.
- Ensure you keep regular backups stored on a remote server
- Make sure system services are kept up to date with patches
- Regarding GoAnywhere MFT service:
- Review all administrator users for attacker accounts
- Update to version 7.1.2 or higher
- Alternatively apply mitigation configuration – details
Introduction
Clop is an example of ransomware as a service (RaaS) that is operated by a Russian-speaking group. It was discovered in 2019 after being used by TA505 in a spear phishing campaign.
Clop (or Cl0p) is one of the most prolific ransomware families in recent years. It’s infamous for compromising high-profile organizations in various industries worldwide using multilevel extortion techniques that resulted in huge payouts estimated at US$500 million as of November 2021. Organized efforts to dismantle ransomware cartels of a global coalition across five continents led to the arrests in Ukraine of six suspected Clop members in June 2021.
Unfortunately the group’s criminal activities have continued. Reports indicate that only parts of the ransomware’s operations were seized and taken down, such as the server infrastructure used by affiliates to disseminate the malware and the channels used to launder cryptocurrency ransom payments.
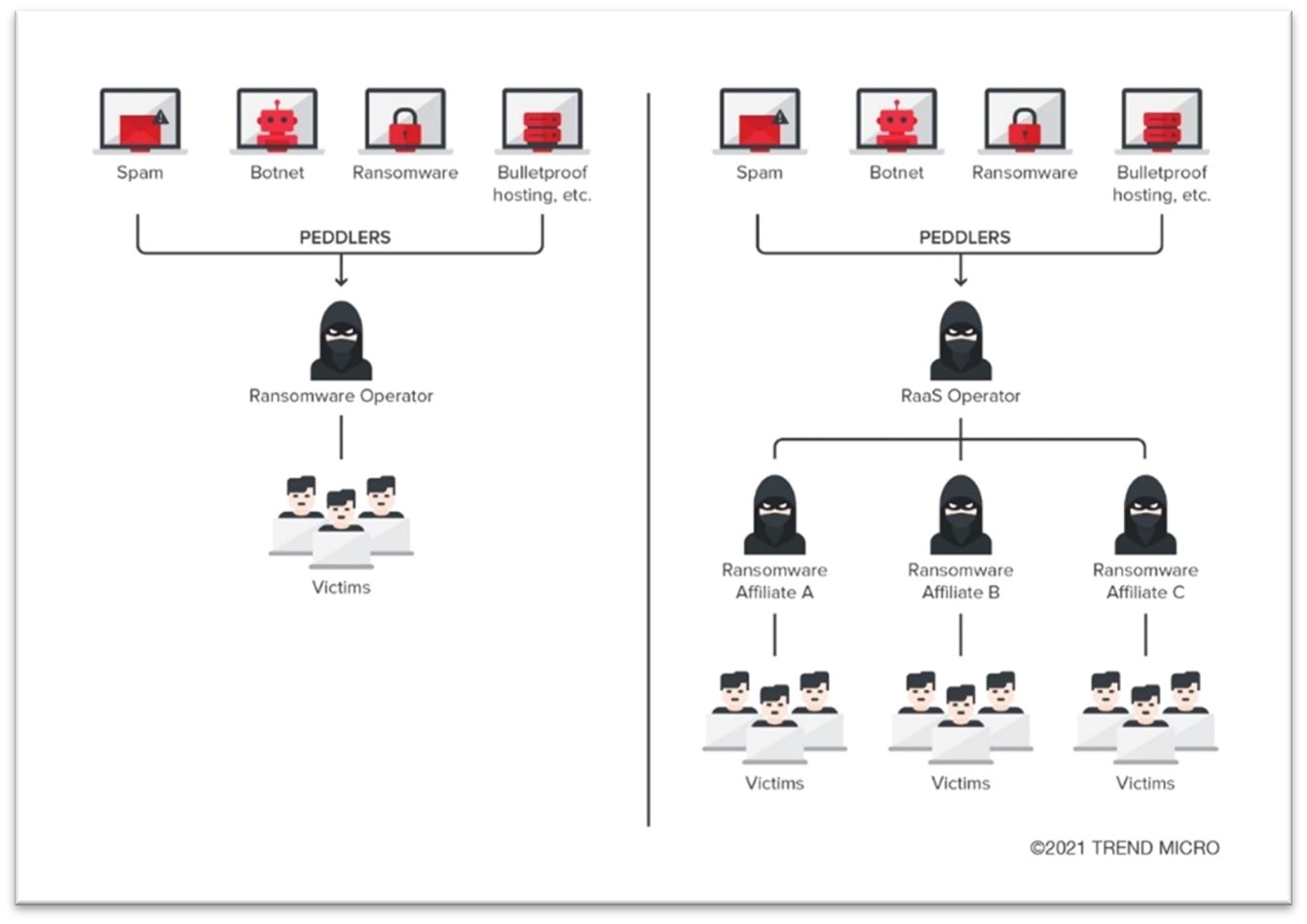
Ransomware operation structure. Source: trendmicro.com
Technical Details of Cl0p ransomware
An established network of initial access brokers provides entry into victims networks. Entry is usually obtained via spear-phishing emails or compromised RDP software, either by brute-forcing passwords or exploiting vulnerabilities (like Kiteworks/Accellion FTA 0-day or the SolarWinds Serv-U CVE-2021-35211).
At this point additional malware is installed to perform C2 and reconnaissance.
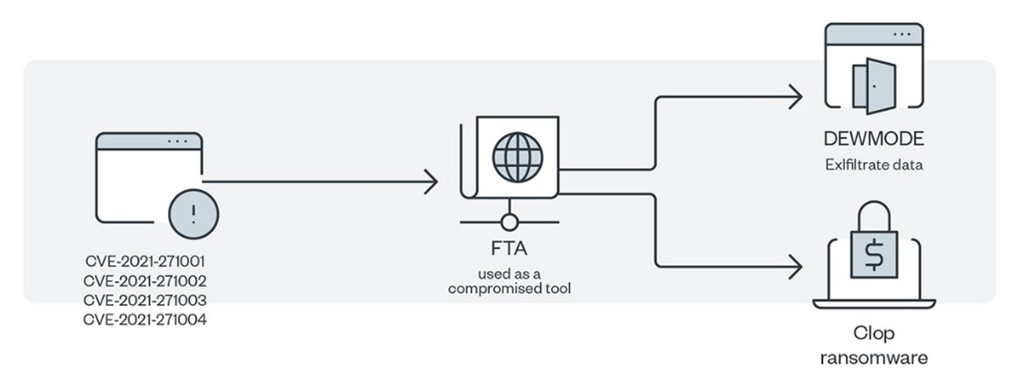
Source: trendmicro.com
Among the tools used are:
- Get2 Loader for downloading SDBOT and FlawedAmmyy
- SDBOT RAT for propagation via USB drives, P2P and network shares, and C2
- FlawedAmmyy RAT for information gathering and downloading other malware
- Cobalt Strike
- TinyMet for reverse shell to C2 server
- DEWMODE webshell for data exfiltration
If the affected machine is not found to be a part of corporate AD environment the malware deletes itself.
Similarly if the current keyboard layout is Georgian, Russian or Azerbaijan and the current charset used in the system is RUSSIAN_CHARSET then the malware will terminate.
Otherwise it’ll try to hack the AD server using SMB vulnerabilities and Cobalt Strike. If this is successful then it’ll use the AD server admin account to propagate to other internal network machines.
Various Windows processes and services are terminated to prevent detection, e.g. Windows Defender, Microsoft Security Essentials and Malwarebytes Anti-Ransomware Protection.
Once data is exfiltrated it encrypts all the files matching the extension list with .Cl0p(some variants use .ClOP or .CLOP) and send the victim to a ransom note website hosted via a Tor hidden service.
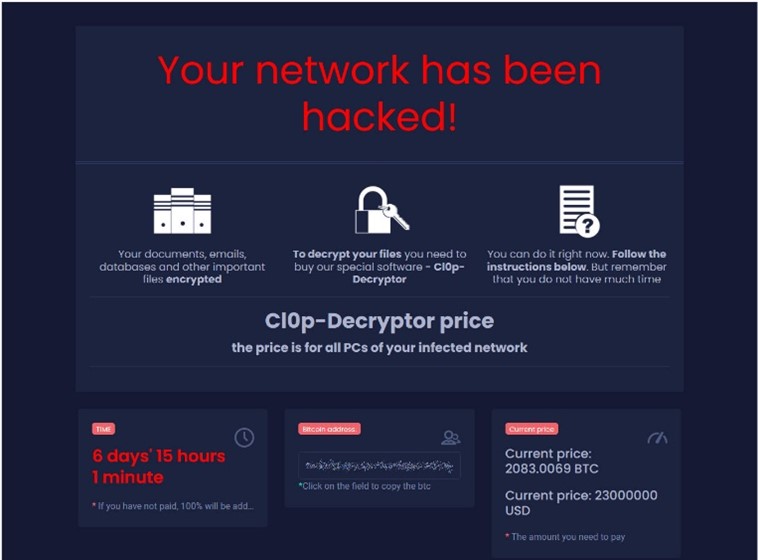
Software AG was presented with this ransom note for $23million. Source: bleepingcomputer.com
Extortion
The ransom note website hosts a ‘support’ chat with the gang, which allows to negotiate the ransom payments and deadline extensions.
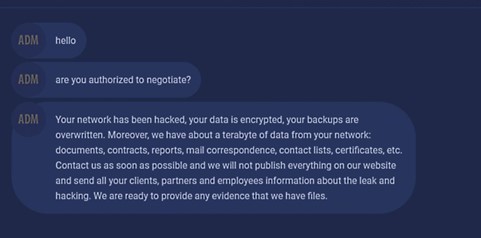
Chatting with the ransomware gang. Source: bleepingcomputer.com
If the company is refusing to pay, they’ll start emailing the partners and/or customers of the affected company with emails titled “Your personal data has been stolen and will be published.” or similar.
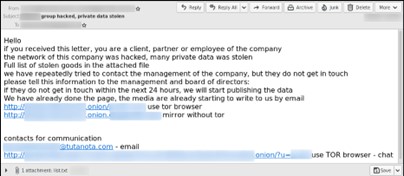
Source: hornetsecurity.com
The linked darknet site used to exert additional pressure on affected companies is called „CL0P^_-LEAKS”. It may eventually contain the published data, but for now it very often simply says „COMING SOON …”.
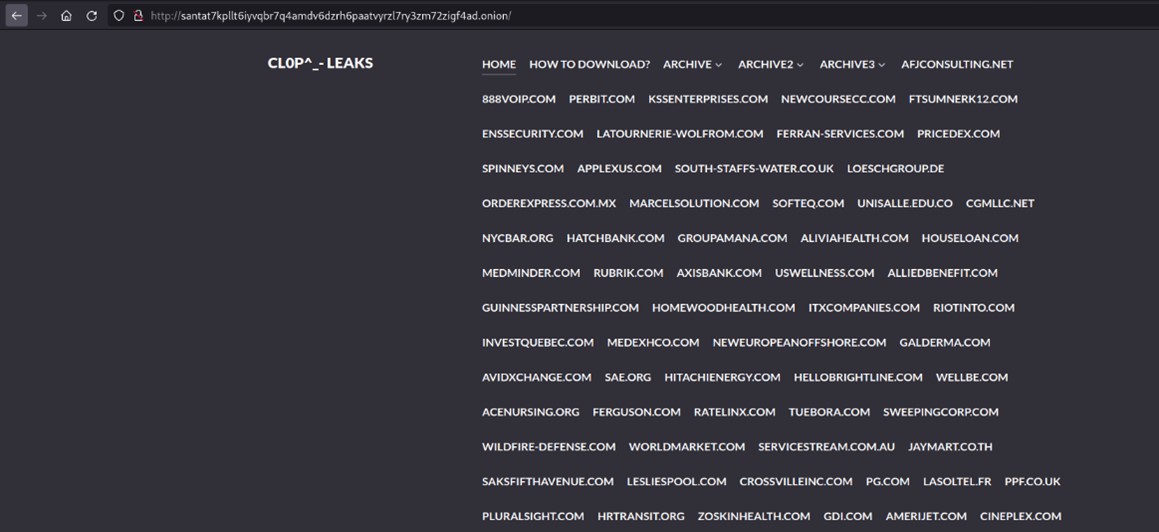
The website starts off presenting a sizeable list of allegedly compromised companies. Source: CL0P^_-LEAKS darkweb site
GoAnywhere MFT vulnerability
Fortra notified it’s customers about the vulnerability on 1st of January with the first public report about the flaw posted by Brian Krebs on infosec.exchange Mastodon instance on 2nd of February.
“A Zero-Day Remote Code Injection exploit was identified in GoAnywhere MFT. The attack vector of this exploit requires access to the administrative console of the application, which in most cases is accessible only from within a private company network, through VPN, or by allow-listed IP addresses (when running in cloud environments, such as Azure or AWS).
If the administrative console is exposed to the public internet, it is highly recommended partnering with our customer support team to put in place appropriate access controls to limit trusted sources.”
Essentially it’s an unauthenticated RCE vulnerability (CVE-2023-0669) affecting the administrative console.
It didn’t take long for the first PoC exploit to be released on 6th of February and even less for first attacks to start with one reportedly starting as early as 2nd of February or even 30th of January.
Reportedly a total of 132 companies were compromised in some way this year, but so far only 12 saw any files published on the darkweb site. Most probably because the gang still expects to receive the payment.
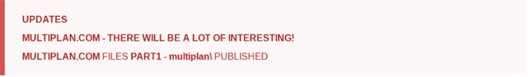
Newest breach announcement from the group. Source: CL0P^_-LEAKS darkweb site
Companies which saw their files published on the site this year, along with when they were added to the site:
· multiplan.com – 30.03.2023
· groupamana.com – 18/03/2023
· hatchbank.com – 16/03/2023
· hitachienergy.com – 18/03/2023
· itxcompanies.com – 18/03/2023
· onex.com – 18/03/2023
· rubrik.com – 16/03/2023
· saksfifthavenue.com – 20/03/2023
· verramobility.com – 23/03/2023
· wellbe.com – 18/03/2023
· nycbar.org – 17/01/2023
· unisalle.edu.co – 28/01/2023
Publication dates based on ransomwatch website which lists ransomware groups along with the companies they allegedly breached.
TTPs
Note that the group is known for frequently evolving TTPs. Additionally since they are running a RaaS their initial access brokers may be using their own TTP’s to gain the initial foothold.
MITRE ATT&CK TTPs
Initial Access
- T1566.001 – Phishing: Spear-phishing attachment
- T1190 – Exploit public-facing application
- T1078 – Valid accounts
Execution
- T1106 – Native API
- T1059 – Command and scripting interpreter
- T1204 – User execution
Persistence
- T1547 – Boot or logon autostart execution
- T1543.003 – Create or modify system process: Windows service
Privilege Escalation
- T1484.001 – Domain Policy modification: Group Policy modification
- T1068 – Exploitation for privilege escalation
- T1574 – Hijack execution flow
Defense Evasion
- T1036.001 – Masquerading: invalid code signature (DVERI, FADO, TOV)
- T1562.001 – Impair defenses: disable or modify tools
- T1140 – Deobfuscate/Decode files or information
- T1070.004 – Indicator removal on host: file deletion
- T1055.001 – Process injection: DLL injection
- T1202 – Indirect command execution
- T1070.001 – Indicator removal on host: clear Windows event logs
Discovery
- T1083 – File and directory discovery
- T1018 – Remote system discovery
- T1057 – Process discovery
- T1082 – System information discovery
- T1012 – Query registry
- T1063 – Security software discovery
Lateral Movement
- T1570 – Lateral tool transfer
- T1021.002 – Remote services: SMB/Windows admin shares
Collection
- T1005 – Data from local system
Command and Control
- T1071 – Application Layer Protocol
Exfiltration
- T1567 – Exfiltration over web service
Impact
- T1486 – Data encrypted for impact
- T1490 – Inhibit system recovery
IoCs
SHA256s – Detection name
e8d98621b4cb45e027785d89770b25be0c323df553274238810872164187a45f – Ransom.Win32.CLOP.NV
8e91f3294883fbdc31ff17c3075f252cbfdc1fc9145c6238468847f86d590418 – Ransom.Win32.CLOP.D
d1c04608546caf39761a0e390d8f240faa4fc821eea279f688b15d0b2cfc9729 – Ransom.Win32.CLOP.E
3320f11728458d01eef62e10e48897ec1c2277c1fe1aa2d471a16b4dccfc1207 – Ransom.Win32.CLOP.THBABAI
eba8a0fe7b3724c4332fa126ef27daeca32e1dc9265c8bc5ae015b439744e989 – Ransom.Win32.CLOP.K
cf0a24f1cdf5258c132102841d5b13e1c6978d9316ba4005076606dc60ec761b – Ransom.Win32.CLOP.L
389e03b1a1fd1c527d48df74d3c26a0483a5b105f36841193172f1ee80e62c1b – Ransom.Win32.CLOP.NU
85c42e1504bdce63c59361fb9b721a15a80234e0272248f9ed7eb5f9ba7b3203 – Trojan.Win32.FLAWEDAMMY.ISO
cb36503c08506fca731f0624fda1f7462b7f0f025a408596db1207d82174796a – Trojan.Win32.FLAWEDAMMY.DLDR
af1d155a0b36c14626b2bf9394c1b460d198c9dd96eb57fac06d38e36b805460 – Backdoor.Win32.FLAWEDAMMY.AB
ad320839e01df160c5feb0e89131521719a65ab11c952f33e03d802ecee3f51f – Backdoor.Win32.FLAWEDAMMY.AQ
c042ad2947caf4449295a51f9d640d722b5a6ec6957523ebf68cddb87ef3545c – gamft.dll
0e3a14638456f4451fe8d76fdc04e591fba942c2f16da31857ca66293a58a4c3 – larabqFa.exe
c9b874d54c18e895face055eeb6faa2da7965a336d70303d0bd6047bec27a29d – Pxaz.dll
URL – Detection name
hxxp://91[.]38[.]135[.]67/km1 – Downloads malicious file detected as Trojan.Win32.FLAWEDAMMY.DLDR
5.188.206[.]76 – Hosting location for Truebot
qweastradoc[.]com – C2 domain for Truebot
92.118.36[.]213 – Hosting IP for Truebot C2 domain
References
https://www.trendmicro.com/vinfo/nz/security/news/ransomware-spotlight/ransomware-spotlight-clop
https://securityaffairs.co/116029/cyber-crime/clop-ransomware-extortion.html
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/clop-ransomware/
https://www.hornetsecurity.com/en/security-informationen-en/leakware-ransomware-hybrid-attacks/
https://infosec.exchange/@briankrebs/109795710941843934
https://frycos.github.io/vulns4free/2023/02/06/goanywhere-forgotten.html
https://www.darkreading.com/endpoint/massive-goanywhere-rce-exploit
https://www.huntress.com/blog/investigating-intrusions-from-intriguing-exploits
https://ransomwatch.telemetry.ltd/#/profiles
Glossary of terms
TA – Threat Actor
TI – Threat Intelligence
TLP – Traffic Light Protocol
TTPs – Tactics Techniques and Procedures
RCE – Remote Code Execution


