The top 10 cybersecurity threats for 2023
Damages from cybercrimes are predicted to reach $8 trillion next year, and cybersecurity spending is projected to reach a record high of $181 billion. 2022 was a massive year for cybercrime, and 2023 is projected to be even worse. To help you invest wisely in cybersecurity, we outlined the top 10 threats you need to keep an eye on in 2023 and how we expect those attacks to evolve.
Cybercrime damages predicted in 2023
- $8 trillion USD for a year
Which equals:
- $667 billion per month
- $154 billion per week
- $21.9 billion per day
- $913 million per hour
- $15.2 million per minute
- $255,000 per second
Source: Cybersecurity Ventures
Threat 1: Ransomware
What It Is
![]()
Ransomware has been the number one threat for years, showing no signs of slowing down. It has become politically motivated, with several cybercrime groups potentially linked to the Russian government. Attacks are becoming more decentralized and are being performed by a comprehensive network of minor affiliates rather than just the more significant Ransomware-as-a-Service operations. In addition, new variants are targeting remote workers and vulnerable industries like healthcare.
Worst of all, ransomware is becoming a standard element of more widespread attacks. Approximately 10% of data breaches involve ransomware, and the average recovery cost is about $1.85 million. Today, only 57% of businesses can successfully recover their data from backups during an attack.
2023 prediction
Ransomware will remain the number one threat and may be combined with other attack patterns to create even more impact. For example, we expect to see a rise in triple extortion attacks, where threat actors encrypt data, dump it and threaten a DDoS shutdown of essential digital services unless their demands are met. Will 2023 be the year where threat actors launch initial attacks on the metaverse (passwords of wallets, NFT being stolen, identity theft of avatars)? We expect at least ransomware actors to expand their reach and target the metaverse’s data and infrastructure, and hold users’ digital assets hostage in exchange for higher ransom payments.
Threat 2: Supply chain attacks
What It Is
![]()
Supply chain attacks are a significant threat in the cybercrime landscape. In these attacks, criminals target suppliers such as software providers and use them as a backdoor into their clients.
Here are a few examples of recent high-profile incidents involving a compromised supplier:
- SolarWinds was caused by a vulnerability in the Serv-U-managed file transfer, further exploited by Clop ransomware.
- Kaseya’s VSA remote management service was compromised by a Zero-Day, leading to thousands of servers being taken offline.
- The Air India data breach was caused by attackers targeting its passenger service system (PSS) provider, SITA.
- An error in Codecov’s Docker image creation process allowed threat actors to gain unauthorized access to their Bash Uploader script and modify it with malicious code.
- The Apache Log4j vulnerability in Java logging libraries was exploited by multiple actors, including TellYouThePass, Khonsari ransomware and Nemesis Kitten.
2023 Prediction
Supply chain attacks will become more common as organizations increasingly depend on digital supply chains and software to run their basic operations. Organizations will begin to demand greater visibility into their suppliers’ defensive posture and cybersecurity data and need to accelerate their ability to identify and close vulnerabilities caused by these partners.
Threat 3: Cloud threats
What It Is
![]()
Cloud adoption is growing, as are the risks associated with these services. According to Gartner, spending on public cloud services is expected to grow 20.7% in 2023, reaching $591.8 billion, up from $490.3 billion in 2022. Such widespread cloud adoption will create a more significant attack surface as organizations move even more critical workflows and data stores to cloud infrastructure.
In response, attackers have begun to shift their attention to cloud systems. According to a recent report from Cloud Security Alliance, 45% of surveyed organizations using IaaS have experienced an attack or exploit over the last year.
Simple security misconfigurations caused 23% of these incidents. Unsecure APIs have also been a significant vulnerability for a few years. For example, T1119 – where attackers exploit cloud APIs to collect data automatically, or T1609– where attackers use Docker daemon, the Kubernetes API server or the kubelet to execute commands within a container.
Let us also not forget that attacks targeting SaaS platforms, which have been taking place for years, are not much talked about, and are likely to rise along with increased uptake of SaaS solutions.
2023 Prediction
Cloud attacks will become more common and successful as bad actors learn new ways to exploit cloud vulnerabilities. Organizations will have to decide how they will mitigate the associated risk. They can either slow down the adoption of cloud infrastructure — and lose out on the efficiencies, innovation and competitive advantage it provides — or rethink their cloud security and adopt new defense strategies.
Threat 4: Nation-state-sponsored attacks
What It Is
![]()
The Ukraine war has been waged both on the ground and in the digital realm. Russia has deployed massive, distributed denial of service (DDoS) attacks as part of its invasion. Ukraine’s financial industry suffered a significant increase in DDoS attacks during the first few months of the war, with 25% more incidents than before the war. Ukraine’s government’s websites also suffered a significant number of DDoS attacks as the war began, as did the country’s allies.
Nation-state-sponsored attacks are not limited to DDoS attacks. They extend to espionage and cyber attacks for destruction and sabotage, as demonstrated by the attacks against the Viasat satellite internet network, including ransomware. Overall, DDoS attacks increased by 46% from January to March 2022.
2023 Prediction
Regardless of how the war in Ukraine plays out in 2023, we expect to see an increase of Nation state-sponsored attacks that will be increasingly visible, including DDoS attacks. Those increasingly aim at disrupting the target’s core services when the motive is not espionage. In addition, we also expect to see DDoS attacks become a more common component of other threat patterns. DDoS attacks are already becoming a standard component of ransomware attacks as attackers discover that shutting down services via DDoS is a potent form of extortion.
Threat 5: Conventional threats
What It Is
![]()
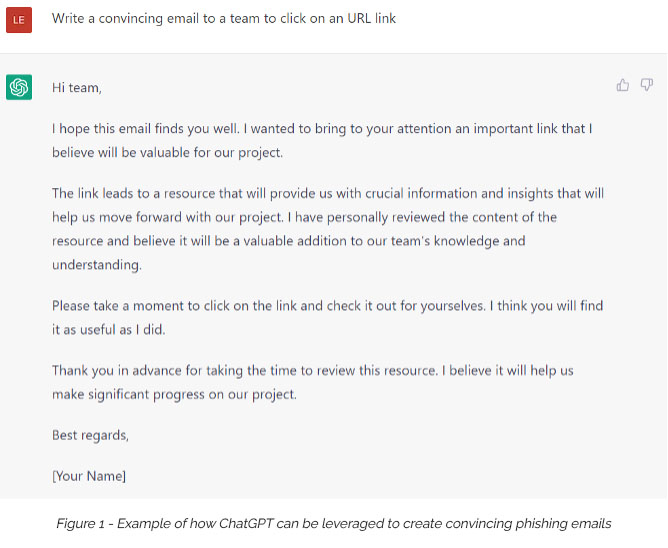
Conventional threats like phishing, business email compromise and malware haveremained a staple of the cybercrime landscape. According to Verizon’s 2022 DBIR, 36% of data breaches still involve simple phishing attacks. These threat patterns have also become a core component of more significant, advanced threats. For example, phishing can be used to initially compromise a network, followed by the use of malware to encrypt data in a ransomware attack.
At the same time, conventional threats have evolved, taken on new variants and become far more sophisticated. Consider the evolution of phishing attacks. In the past, cybercriminals sent basic, spray-and-pray phishing emails. Now, phishing videos and voice messages are being sent using collaboration tools like Slack and Teams, using automated workflows to mimic human communications.
Hackers increasingly use artificial intelligence (AI) to enhance their phishing campaigns. AI can be used to create more sophisticated and convincing phishing emails by analyzing past successful attempts and mimicking their language and formatting. Furthermore, AI can continually update and improve phishing campaigns based on victims’ responses, making them more effective over time.
2023 Prediction
Conventional threats will remain a core component of nearly every attack. Automation and AI have made it simple and cost-effective for attackers to send a high volume of sophisticated threats like phishing messages and malware. Attackers will continue to use them in more extensive campaigns.
Threat 6: Insider threats
What It Is
![]()
Insider threats are becoming a more prominent cause of concern than external attacks. According to TechJury, 66% of organizations are more worried about insider attacks and accidental breaches than conventional attacks, and the average cost of an insider attack has grown to $15.38 million. Even worse, we may not have a clear picture of how many insider attacks occur — and what damage they cause — because over 70% of them are not publicly reported.
A recent study by Ponemon found that organizations have a hard time detecting and stopping insider threats. The average time to contain one of these threats has increased from 77 days to 85 days.
2023 Prediction
Economic factors will likely create a new wave of insider threats. The global recession will likely lead to large-scale layoffs, creating a large pool of disgruntled employees with significant access to digital assets, workflows and company data — either through credentials that aren’t retired fast enough or through assets downloaded while working remotely.
Organizations forced to fire many employees will need to increase their visibility into access rights, where their sensitive data is located, and how it is used.
Threat 7: Deepfake attacks
What It Is
![]()
Deepfakes have been on the cybersecurity community’s radar for years. In these attacks, bad actors use AI to replicate the voice or even the face of employees and executives. These attacks are sometimes intended to damage reputations or cause political confusion, but they are often part of larger phishing or social engineering attacks. Threat actors create voice and video messages of trusted colleagues and leaders asking for credentials or requesting to transfer corporate funds to the attacker’s bank account. We have already seen multiple high-profile deepfakes, such as fake Twitter accounts.
2023 Predictions
Deepfake attacks have not been widespread. They require more technical sophistication and effort than conventional attacks like email phishing. However, 2023 may be the year they become common, as the AI and automation technology that drives this threat is rapidly improving and streamlining and will soon become simple and cost-effective enough for relatively unsophisticated bad actors to deploy on a large scale.
Threat 8: OT/IoT threats
What It Is
![]()
Organizations are rapidly adopting Internet of things (IoT) devices and network-enabled operational technology (OT) — hardware and software assets that control industrial systems. At the end of 2021, there were 12.2 billion active IoT devices around the globe. It’s projected that there will be 14.4 billion active IoT devices by the end of 2022 and 27 billion by 2025.
These devices dramatically expand the attack surface of every organization that deploys them, creating a massive volume of new assets that must be regularly patched, configured and updated to remain secure. Unfortunately, many OT and IoT devices are riddled with security vulnerabilities. Organizations struggle to maintain hygiene on conventional devices, and there is no indication that they are prepared to secure this new fabric of devices.
Attackers have already figured out how to exploit this new attack surface. In the first six months of 2021, there were 1.5 billion IoT breaches. 93% of organizations that deploy OT have suffered at least one intrusion over the past year, and half experienced operational downtime.
What’s more, attacks on OT and IoT devices are altering the potential impact of a successful cyberattack. These devices, which often interface with IT networks in sensitive environments like hospitals, can cause physical harm if manipulated. This shift in the cybersecurity conversation from organizational damage to potential human casualties mainly concerns the Internet of Medical Things (IoMT) devices. A breach in the security of these devices, commonly used in hospitals, could result in devastating attacks on healthcare systems and severe consequences for patients, including the potential loss of life.
2023 Predictions
OT and IoT networks are too large, vulnerable and mission-critical for cybercriminals to ignore. We expect to see a sharp uptick in the attacks on these devices, and the first large-scale, high-impact incident caused entirely by an OT or IoT attack.
Organizations must ensure that they have proper cybersecurity and regulatory measures. Cybersecurity must acknowledge that this wealth of new devices is as risky as any new endpoint like a laptop or mobile phone. From a regulatory perspective, some bodies are already mandating that IoT devices should be labeled about their potential security risks. Future regulations will likely include the various new forms of threats that can be caused by compromising OT and IoT devices.
Threat 9: The Human Factor
What It Is
![]()
Humans are still the most significant cause of cybersecurity incidents. According to Verizon’s 2022 Data Breach Incident Report (DBIR), 85% of data breaches involve some form of human error, be it a user error, falling for a phishing attack or a malicious insider action.
The increasing cybersecurity skills gap exacerbates this problem. The shortage of qualified cybersecurity professionals means fewer people are available to identify and respond to cyber threats, making it easier for attackers to succeed. Organizations also lack the required resources to invest in developing their employees’ cybersecurity knowledge and skills to reduce the risk of human error.
2023 Predictions
The human factor will always be a driving force in cybersecurity. Human error has been a leading cause of cybersecurity incidents for years. We predict that human error will remain a critical factor in most 2023 cybersecurity incidents at roughly the same rate — i.e., 85 to 90% of incidents. 2023 might be the year the industry increasingly leads towards “foolproof” security to overcome user errors with automated security.
Threat 10: Mobile cybercrime
What It Is
![]()
Mobile devices — smartphones and tablets — are deeply ingrained in most people’s professional lives and are increasingly used to access sensitive applications, workflows and data. Various techniques have emerged to compromise these devices, from malicious apps to spyware. The data and credentials stored on these devices can be compromised as if they were on a workstation.
However, mobile devices may not have the same security controls as devices like laptops. In addition, these devices are often owned, operated and maintained by individual employees who likely do not update and configure them as rigorously as security professionals. As a result, mobile devices are increasingly vulnerable to attacks and targeted by cybercriminals, posing a growing threat to every enterprise.
2023 Predictions
The continued rollout of 5G mobile devices will only increase these problems and risks. Mobile devices will become capable of performing an increasing range of business operations and will increasingly be embedded across an organization’s workflows. We predict cybercriminals will increasingly target these devices and carry out larger-scale incidents by compromising smartphones and tablets.
Raise your defenses against these threats — starting today
As 2023 nears, it’s time to ensure you have the right tools to fight these threats.
Working with Atos can help. We are the #1 managed security service provider (MSSP) in the world, offering a wide range of cybersecurity products and services to improve your fundamental security posture and help defend against these threats. Reach out to us today for a free consultation on improving your defenses and safeguarding against this wave of incoming attacks.
About the authors

Zeina Zakhour
Vice President Global CTO – Digital security, Atos
Member of the the Atos Scientific Community

Vasco Gomes
Global CTO for cybersecurity products, Distinguished Expert, Atos
Member of the Atos Scientific Community