The challenges of homomorphic encryption
Computation on encrypted data: the next step for security
Data privacy has increasingly become an important need for both consumers and enterprises. Industries in the information technology sector have no choice but to consider it, if only for liability and regulatory concerns.
Today, our world runs on codes and ciphers, from digital payments to online shopping. Cryptography plays a prominent role in ensuring data confidentiality, whether it is stored or in transit. While classical cryptography focused on merely guarding static data, modern cryptography must handle additional aspects like authentication and integrity. However, in today’s world these alone aren’t enough.
Let’s consider a case where an enterprise stores its data on a central server or cloud. If a data computation must be performed, we are faced with two options:
Transfer the data back to its owner, or
Allow the server to gain access to the unencrypted data
Both these options have obvious drawbacks, leading us to search for a better solution. Fortunately, homomorphic encryption (HE) enables us to preserve privacy while providing computational flexibility.
What is homomorphic encryption?
The concept of “privacy morphisms” was first proposed in 1978[1] and for a long time, HE has been seen as the ‘holy grail’ of cryptography. It was only in 2008 that the first construction of a ‘fully’ homomorphic encryption scheme was given.
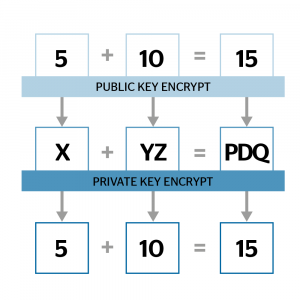 Using an HE scheme, an enterprise can encrypt its data and send it to the server, allowing computation to be done directly on the encrypted data.
Using an HE scheme, an enterprise can encrypt its data and send it to the server, allowing computation to be done directly on the encrypted data.
The final ciphertext is sent back and decrypted to obtain the result, which yields the same output that would have been obtained if the computation were done on the unencrypted data. Since the encryption preserves the validity of the computation throughout, we call it “homomorphic.” A simplified version of this scheme is shown at right:
Since multiple technologies may be applicable to the same problem, it is important to pick the right technology for a given scenario. In most cases, HE can offer at least semantic security. This is not just a theoretical issue, since there have been high-profile cases where data that was thought to have been sufficiently anonymized was de-anonymized.
For example, in 2006 Netflix published viewer rankings as part of a public challenge to develop a better recommendation system for its platform. Personal details were supposedly anonymized and replaced with random numbers to protect user privacy. However, two researchers at the University of Texas at Austin, Arvind Narayanan and Vitaly Shmatikov, demonstrated how easy it was to de-anonymize the data by comparing subscriber records to the Internet Movie Database (IMDb) dataset. This shows that a motivated adversary can identify and de-anonymize records with little information.
Homomorphic encryption: the future of cloud security?
There are two large classes of applications of HE:
Database applications:
Consider a server that holds an encrypted database, to which users send encrypted queries. The objective is to keep both the database and the queries private (to the extent possible), and HE provides a viable solution. Thus, we can imagine search engines and spam filters using HE for this purpose.
Secure computation
In this scenario, data is kept encrypted and a specific computation can be given to the server in the form a circuit. The server performs the computation and sends the result back to the owner of the data. It can also be used for applications.
For cloud security, customers are increasingly choosing not to use cloud native encryption solutions for sovereignty purposes, instead employing their own encryption. In a mid and long-term perspective, fully homomorphic encryption could allow applications and systems to perform operations on encrypted data without decrypting them for analytics.
The way forward
Homomorphic encryption is a topic that Atos believes holds a great deal of promise. As such, we are working actively on the future of homomorphic encryption — focusing our HE research in a few key areas.
Through its Trustway cryptographic products, Atos is focused on developing advanced cryptographic products and their associated management infrastructures. Atos is part of several joint research projects and alliances that have the goal of bringing homomorphic encryption solutions to market.
Atos is also developing a hardware accelerator for client-side computations of the FV (for Fan-Vercauteren, its authors) cryptosystem. FV is a second generation cryptosystem that we believe combines all the best elements of that generation.
In the future, as individual and data privacy issues remain at the forefront of public consciousness, homomorphic encryption has the potential to deliver the right balance of security and agility that tomorrow’s applications require.
References:
Ronald L Rivest, Len Adleman, Michael L Dertouzos, et al. On data banks and privacy homomorphisms.
Foundations of secure computation, 4(11):169-180, 1978
About the author

Nagarjun Dwarakanath
Interested in next publications?
Register to our newsletter and receive a notification when there are new articles.
