Protecting the Internet of Things: what is at stake for network operators?
Today, most European tech buyers see IoT as either a tool for transformation or strategy that comes with security issues and concerns. With this new technological landscape, we are barely beginning to understand the possible repercussions and the security challenges of these millions of connected devices.
End-to-end security is critical as a cyber-attack could bring to a stall a company’s activities.
In terms of security, network operators are the most exposed. When they deploy IoT networks, they need to consider various parameters that can affect data confidentiality. The entire architecture must be secured from the gateways to the user’s platform. Network operators are also expected to deliver secure services to IoT business owners while optimizing operating costs.
That is why the biggest challenges to deploy secure, and scalable IoT networks for their customers are to:
Secure the infrastructure
on which the IoT networks are based in compliance with the current standards (4G/5G/LoRaWAN networks…)
Ensure data trust
by verifying the integrity of the payload
Manage the trusted node’s lifecycle
The challenge
A few years ago, Atos had the opportunity to support a major French Telecom company in their security strategy. Under this umbrella, this company envisioned a platform that could allow them to respond to any security concern with a confident end-to-end approach.
They were also looking for a partner and not only a solution: it was up to the former to analyze security requirements and to ensure that all IoT devices, networks and data would be secured for their customers, as well as maintain and manage security in a continually developing and mutating cybersecurity landscape while delivering insightful analytics.

The solution
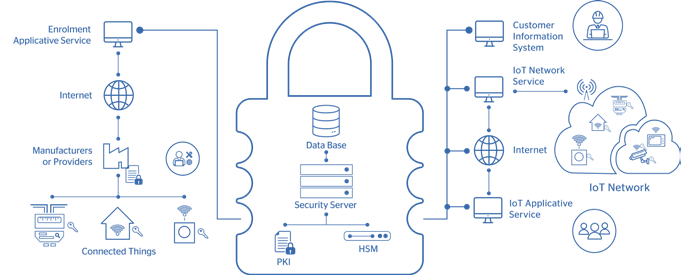
From initial discussions to implementation, the project took an overall twelve months. As a strategic partner for this new IoT business, we helped the client implement LoRa technology, a global standard for secure IoT architecture. Atos showed how the security platform spans the most extensive IoT ecosystems, as it can handle vast quantities of security data generated by millions of IoT devices working at the same time. By also generating and managing real-time security keys, it eliminates the need for stored keys and, therefore, disarms this critical point of attack.
Atos solution is scalable and allows telecom companies to generate trusted identities for IoT devices as fast as they need to be added due to the use of Public Key Infrastructure (PKI). It is also worth highlighting the automated tooling for full lifecycle management. When so many IoT implementations utilize low-cost and often transient devices, such as shipment-specific sensors in logistics, it is essential that the security solution can add, monitor and decommission devices without human intervention.
Enabling security in such complex environments can be challenging. However, the client’s data must stay secure. Offering the peace of mind by providing end-to-end security is now a critical asset to become a global IoT network operator.
Related resources
Interested in next publications?
Register to our newsletter and receive a notification when there are new articles.


