IoT security with managed detection and response
IoT devices and technologies are being rapidly adopted in the consumer, enterprise and industrial worlds. Their use cases are growing in number by the day, increasing their possibility of influencing our lives in the years to come. As with every technology, it should be no surprise that there are risks with IoT. However, the level of concern is much higher in IoT as they have the power to cause physical destruction, harm lives and cause systemic failures.
Today, managed detection and response (MDR) service, with its emphasis on large scale cyber data analytics and fast machine-driven containment, is playing an essential role in securing IoT infrastructure. MDR is the evolution of traditional managed security service with a focus on deep detection and rapid response.
How MDR provides deep detection for IoT infrastructure
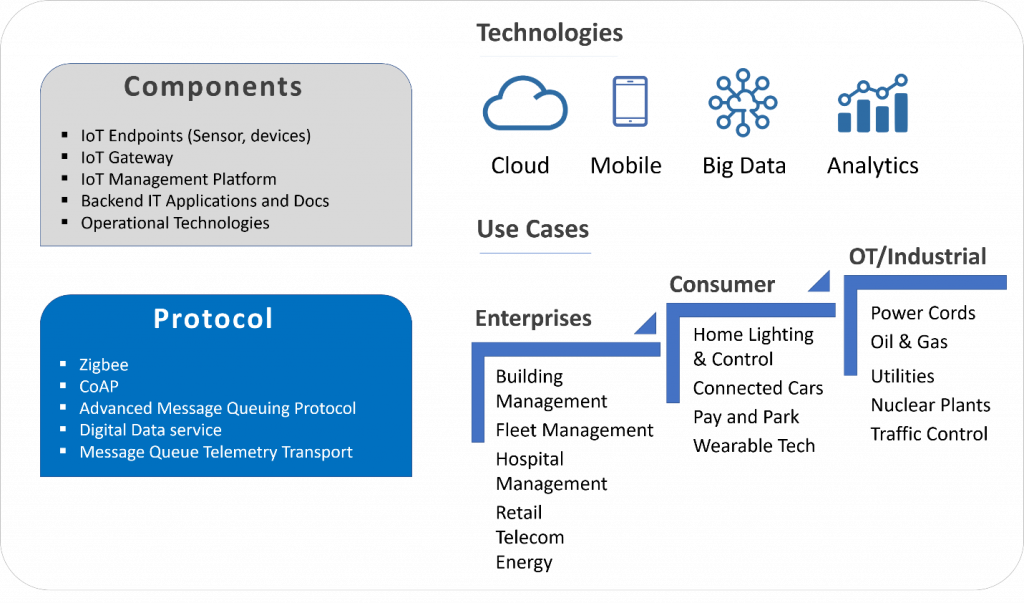
IoT technology stack has many new components, including IoT sensors, protocols, gateways, and management platforms. In addition to this, IoT infrastructure also uses traditional web applications and cloud technologies in backend services. Detecting threats across these components have three challenges:
1
IoT devices are deployed in thousands at distributed locations and these devices can not be monitored individually with security agents. That means we need to monitor traffic at gateways or network level, which involves large scale data analytics.
2
There are many IoT protocols in the market today including Zigbee, CoAP, Advanced Message Queuing Protocol (AMQP), Digital Data Service (DDS), and Message Queue Telemetry Transport (MQTT). These protocols are either new or derived for IoT from an earlier version used for general purposes. There are limited known rules or signatures to detect threats in these. Hence, we need more of abnormality detection, pattern recognition, outlier and anomaly detection technologies instead of a rule-based monitoring system.
3
IoT management platforms, on the other hand, have web interfaces and are cloud deployed. They are exposed to common web application and cloud infra threats. So, we need a system which can perform detection across a hybrid environment, crossing over from IoT to web platforms.
A typical SIEM, which is mostly a rule-based system for limited protocols, will fail in such a scenario. Traditional security monitoring built around SIEM is no longer sufficient when it comes to IoT. They were good for compliance use cases and visibility into common attacks, but not against today’s newer forms of attacks.
MDR technology, such as AIsaac from Atos, has capabilities to address these challenges. It’s a big data platform on high-performance computing that provides power for large scale data analytics across diverse data set of IoT infrastructure. And it has built-in machine learning models to detect unknown threats- for those threats where rules cannot be written. The platform supports several native IoT protocols along with cloud and more traditional network protocols.
MDR service complements the AIsaac platform with expert analysts and threat hunters reviewing the data and alerts from the system. This helps in providing 24×7 in-depth coverage for your IoT infrastructure.
Time to Detect
Early
Late
Apply global threat intel to proactively fix gaps before threats reach you
 Threat Anticipation
Threat AnticipationDiscover evasive threats using Machine Learning and experienced threat hunters
 Threat Hunting
Threat HuntingDetect known threats in near real-time using sophisticated rules & correlations
![]() Security Monitoring
Security Monitoring
for known attackers, known attacks and unknown attacks and attackers
Detecting potential threats at speed is only one part of cybersecurity. How you handle these threats and respond to them determines whether they remain a minor incident or become a headline-grabbing breach.
How MDR provides rapid response for IoT infrastructure
MDR platform such as AIsaac offers three critical capabilities for rapid response for your IoT setup:
1
Investigating the threats and quickly assessing the extent of impact: Modern attacks are rarely a one-off event, especially so in IoT where such threats are likely long-drawn-targeted-attacks. Traditional SOC services lack the speed to link past events and create a complete story on the attack campaign. MDR service can uncover the attack campaign quickly and assess the full impact as the platform provides analytics on historical events.
2
Contain threats at machine speed: MDR platform connects to various network elements, security products and gateways to quickly push rules for containment. These can include: quarantining a device, blocking a connection, reconfiguring system parameters, etc.
3
Reduce mitigation time from days to hours: Once the full impact is known, the next stages of incident management needs to be activated- namely eradication and recovery. Today these stages are extremely slow. MDR service brings speed to the incident management process by providing incident playbooks and automating the workflows for execution.
Time to Respond
Immediate
Deliberate
Get swift analysis on threats, impact on assets, blast radius, and more
–
 Incident Analysis
Incident AnalysisContain and recover swiftly with agile response from machine learning
–
 Auto Containment
Auto ContainmentEvict attackers, eradicate threats, & advance your defenses from the learning
–
![]() Response Orchestration
Response Orchestration
know the impact, quickly block threats and mitigate and recover
Securing the IoT environment requires speed and scale for detection and response. MDR technology and services, combines high-performance computing, machine learning and cyber experts to provide valuable defense for IoT infrastructure.
Related articles
Interested in next publications?
Register to our newsletter and receive a notification when there are new articles.

