2023 top trends for Identity and Access Management (IAM)
Cloud transformation is no longer an option for companies — it is a requirement, and most enterprises are already headed in that direction. Even if a company has not undergone an application migration or modernization within their data centers, there is a high probability that they are utilizing cloud-native applications. If they use Microsoft Teams, Google Meet or Amazon Chime for video conferencing meetings, they are consuming cloud applications. If they are sharing files via OneDrive, Google Drive, Box or DropBox, they are utilizing cloud-native Software-as-a-Service (SaaS) applications.
Although you may believe that your company is operating within a private infrastructure, it is very likely that you are also using a SaaS application somewhere within the company. This immediately turns your model from a private cloud to a hybrid model, or even a multi-cloud model, and creates security vulnerabilities in identity and access management (IAM). User identities are no longer confined to the four walls of the company; they are now sprawling across the Internet. These identities must be protected against malicious threats attempting to gain access to resources or steal identities.
Assessing a growing threat
According to the Identity Defined Security Alliance (IDSA), 84% of organizations were hit with an identity-related breach within the last year. Most were related to the increased number of identities and their use for access to SaaS and other cloud applications. Additionally, they were linked to using these identities for third-party partner access or guest access for collaboration.
The push for companies to move towards a robust cloud adoption strategy has contributed to an accelerated growth in the global IAM market. The unprecedented increase in remote business operations now demands that companies address IAM head-on and devise cybersecurity strategies to protect users, devices and resources.
2023: Threats and trends on the horizon
As we move into 2023, the trend toward cloud adoption will only increase the need to develop a strong IAM security plan. But where should you start?
Here are three key IAM trends, tactics and their underlying technology for protecting identities and decreasing the likelihood of a breach:
![]()
Zero-friction security
![]()
Decentralized

Non-human identities
Creating zero-friction security for a positive user experience
IAM is a key security concern for companies, both within private data centers and cloud infrastructures, within an in-depth defense strategy and a zero-trust methodology. The critical challenge is to secure identities without creating a negative experience for users.
If a user finds IAM processes too complex or cumbersome, they may attempt to find workarounds or utilize unauthorized applications, creating shadow IT. Exceptions allowing users to bypass existing controls may be granted if the controls add too much friction to critical business processes. This creates additional security concerns for the company and its users by exposing identities and data to unauthorized applications.
In an effort to provide a secure, positive and seamless user experience, companies should go beyond multi-factor authentication (MFA) and password complexity. They should look for advanced IAM techniques to protect identities within IAM without introducing additional complexity to the user. These methods should focus on simplicity while providing business enablement across all applications.
The goal of any company should be to decrease its reliance on passwords. Passwords are easily compromised and, in most cases, are weak when not generated randomly. Recently, MFA techniques have proven vulnerable to social engineering techniques used to phish the authentication code from an unsuspecting user.
Companies should evaluate the use of passwordless IAM solutions, leveraging biometric techniques for enforcing MFA and authenticating users. Fast Identity Online (FIDO) version 2 integrates the “something that you have” of MFA utilizing a USB token device, with the biometric “something you are” integrated on the device to enable a full passwordless experience that is resistant to phishing attacks. Implementing a public key infrastructure (PKI) enforces MFA utilizing the PKI card with an 8 to 12-digit pin code. Both methods provide a strong level of IAM security without introducing complexity to the user. In many ways, this implementation is less complex than the utilization of passwords, enabling strong security controls with a positive user experience.

Figure 1: The evolving approach to passwordless IAM
These methods for IAM accomplish another important goal: protecting identities and data, and providing phishing-resistant authentication. MFA fatigue makes a company vulnerable to users potentially exposing a one-time passcode used for verification to someone impersonating company IT personnel. The utilization of passwordless solutions along with behavioral user analysis can protect against these man-in-the-middle phishing attacks.
Just-in-time access is a helpful strategy to avoid identity exposure and inhibit an attacker’s ability to laterally move through a company’s systems. Administrative and elevated privileges for infrastructure, applications, data and management functions should be limited to the time that is necessary to perform job tasks. This access should have an approval and justification process that can be logged for auditability. There should be a session expiration time for all user access to applications that require re-authentication and authorization, and session expiration can be adjusted based on behavioral analytics to avoid user frustration.
Zero-friction security is meant to provide flexibility in meeting the business’ security goals while reducing complexity for users. It continues to expand within the cloud identity provider capabilities. The rising number of legacy enterprise applications makes this strategy difficult across companies. As a higher percentage of applications begin to modernize their IAM capabilities, this strategy will continue to trend in 2023.
Amplifying the need for decentralized identities
The expansive nature of cloud identities has accelerated the adoption of decentralized identities. Decentralized identities give identity ownership back to the users, allowing them to generate a credential to share only the necessary information with a recipient organization. For example, a user may generate a credential that verifies membership in an organization but does not contain other information that is unnecessary for the activity the credential will be used for.
Decentralized identities are a way to break down the barriers of IAM when accessing resources within multiple organizations. Similarities can be drawn between decentralized identities and federated services. Federated services are used to create a B2B trust relationship, while decentralized identities are necessary for a B2C relationship across many companies.
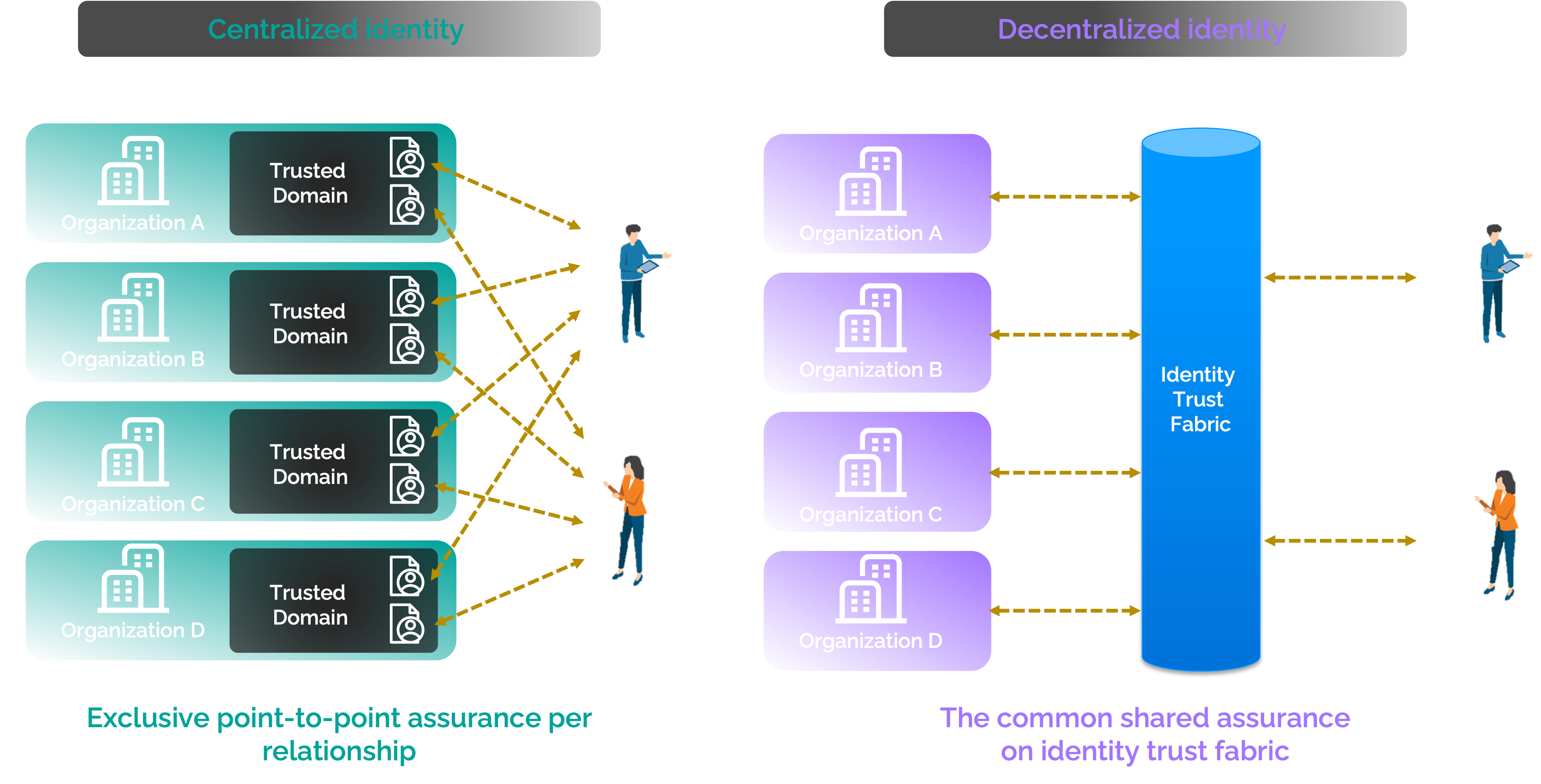
Figure 2: Comparison between centralized identities and decentralized identities
Identities are created and used across social platforms every day, especially for access to various sites and applications. The ability to self-register with these applications creates the decentralized identity that allows the user to register and de-register themselves from these applications. An IAM solution that provides modern authentication capabilities across multiple applications with a single sign-on (SSO) experience gives users autonomy with their identities through an as-a-service delivery. Users replicate the sign-in experience across applications and sites, utilizing one security platform that defines their security controls and posture.
The ability to secure IAM when a user is present across many applications and services will be a continual challenge within a decentralized identity. Utilizing blockchain-based decentralized identity protects user identities within a decentralized identity architecture through encrypted public keys. These keys within the blockchain provide an added layer of security and verification. Blockchain-based decentralized identity can then be used to provide evidence of identity while protecting the personal identifiable information (PII) of the user. Interoperability via a cybersecurity mesh architecture (CSMA) identity fabric can integrate SIEM and SOAR tools into the security mesh to analyze and identify threats. This will help users stay ahead of potential identity breaches and attacks.
Figure 3 is a depiction of the CSMA identity fabric.
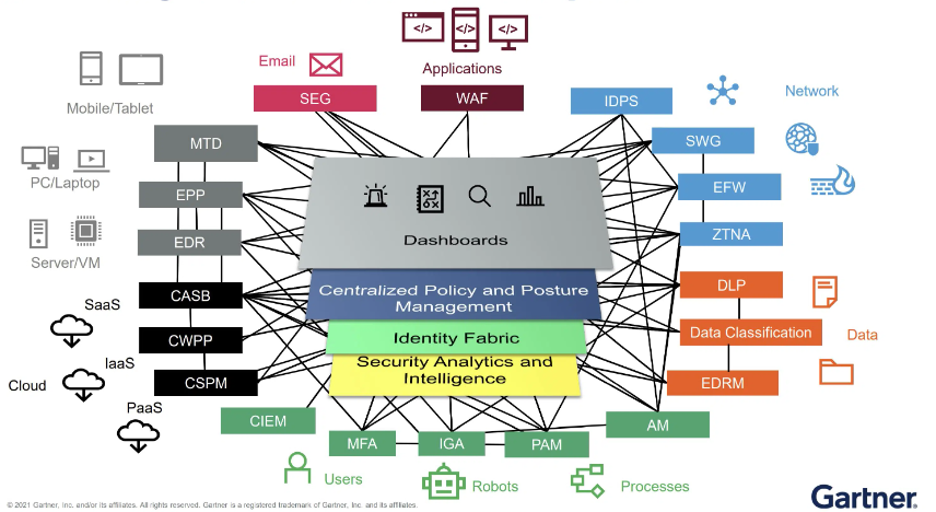
Figure 3: CSMA
Look for a continued trend towards blockchain-based decentralized identity as the developing Web3 standard continues to gain traction.
Up to this point, we have been discussing user access but before we close, let’s address IAM from a non-human perspective.
Handle with care: Non-human identities
IAM is not just limited to users and groups. Non-human identities outnumber human identities by a factor of 45x. These non-human identities are devices that are connected to the public or private infrastructure — primarily robots, storage accounts, databases, virtual machines and applications. In addition, personal assistants, smart watches, surveillance cameras, thermostats and RFID devices are all connected to the internet too. They collect data and send it to storage accounts and databases using an identity and the ability to authenticate to the data repositories.
Enforcing IAM for these identities requires proper planning and implementation to protect them from exposure and elevated privileges. The secrets and keys used to authorize any non-human device require protection and security controls. Key and secret management solutions provide the ability to store and rotate a company’s keys and secrets separately from the device management location. When an authentication is initiated, they can be called from the management solution to authorize the non-human identity. This method provides IAM capabilities without exposing the keys and secrets publicly.
Non-human identities will continue to increase within the cloud infrastructure, due to the growing need to collect, access and analyze more data across the services that a company provides and make accurate, behavior-based predictions.
Gearing up for IAM in 2023
The cloud IAM market size is projected to reach $20.72 billion by 2030 at a CAGR of 21.1%. The accelerated growth predictions underscore the need for organizations to plan, educate and implement secure IAM architecture in the coming year.
About the authors

Dwayne Natwick
Dwayne is the Global Principal Cloud Security Tech Lead at Atos. He supports the cloud security portfolio for the technical capabilities, solution business plans and strategy for Atos, and leads cloud education for Microsoft and AWS.
He has served in many roles over a 30-year career in IT, including as a solution engineer and product manager. Dwayne is a Microsoft MVP, an ISC2 CISSP and 18x certified in multiple Azure and M365 security, data engineering, architecture, and administrator roles. He is the author of multiple books on security and is a Security Professional Community Manager for Packt publishing.
Follow or contact Dwayne

Allen Moffett
Global IAM Practice Lead & CTO
Allen Moffett is Global IAM Practice lead and CTO at ATOS. He is also the global lead for the IAM and Biometrics sub-domain of the ATOS expert community, helping to steer business strategy and building the technology roadmap by anticipating the products and services that will be needed by the market. He also is member of the Executive Advisory board of the Identity Defined Security alliance.
