Managing the top security threats to public cloud
Managing the top security threats to public cloud
Migrating to public cloud? Here’s how you should approach the task.
According to the 2022 Thales Cloud Security Report, 45% of businesses have experienced a cloud-based data breach or failed audit involving data and applications in the cloud, up 5% from the previous year. This raises even greater concerns regarding the migration to public cloud and protection of sensitive data from cybercriminals.
Public cloud adoption, however, has been more rapid than ever. Gartner forecasts worldwide end-user spending on public cloud services to grow 20.4% in 2022 due to reduced infrastructure costs, reduced time to market for applications, and new technologies like data lakes, machine learning and AI. But is it OK to relax security measures as a result of these advantages?
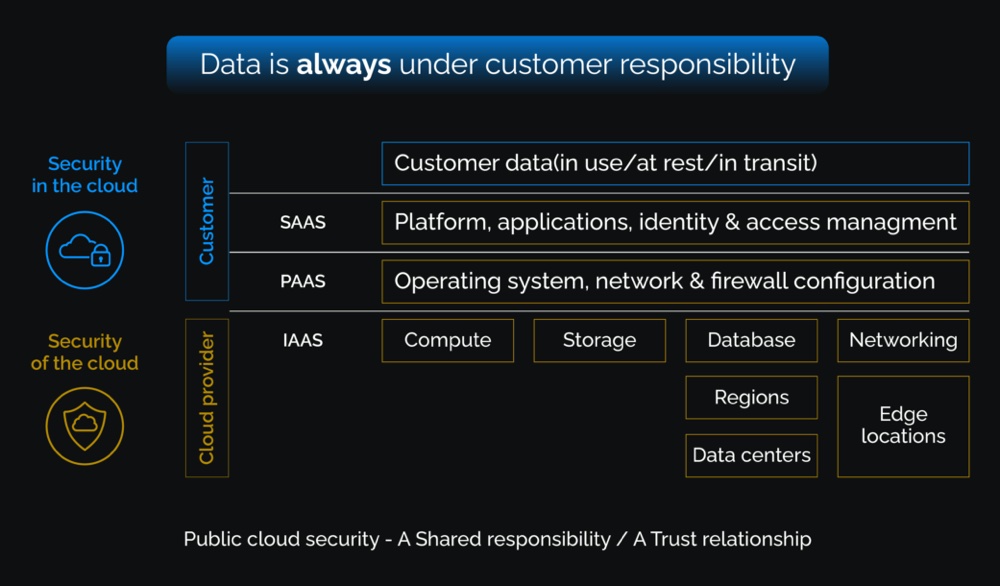
Before deciding what cloud model to use, I would like to draw a simple analogy of a guard and a security practitioner. A guard must know his/her responsibilities, the landscape he/she protects, the threats and the effective countermeasures he/she could use. When an organization decides to migrate to a public cloud, security practitioners must know the shared responsibility matrix between the cloud service provider and the customer.
The risks of cloud breaches vary depending on the environment and the methods used to attack. According to the CSA Cloud and Web Security Challenges 2022 report, IaaS environments (45%) and third-party applications (40%) had the highest breach rate, while SaaS and web applications (32%) had the lowest levels. Hence, depending on the cloud environments you deploy, you will have to manage different risks, not only to your data, but also to your overall infrastructure.
In this blog we will discuss what threats each cloud model faces. To do so, we will outline the landscape or attack surface, threats and possible countermeasures.
Cloud Vendor Vulnerability
Most of the attackers target the customer responsibilities of the shared responsibility model, but often overlooked are the vulnerabilities on the services managed by the cloud provider. A recent vulnerability on Azure AutoWarp Automation Service allowed to obtain authentication tokens of other customers. As in this case, one of the major checkpoints to be done while choosing a service from the cloud vendor is to understand the architecture of the applications and what part of the service is shared between tenants and if the tenants are isolated.
Conclusion
With a multi-cloud strategy, Cloud Access Security Broker (CASB), Cloud Security Posture Management (CSPM) and Cloud Workload Platform Protection (CWPP), organizations can tackle the problem of visibility, threat protection, compliance and data security.
Remember: as a cloud customer, data security is your responsibility and yours alone. Your security practitioners must know where your data resides in the cloud, who consumes the data, how it’s accessed and how to isolate and secure the data using effective countermeasures.
In the cloud, new threats can pop up with the same speed that makes the cloud so attractive in the first place. hence standing up application, services that are only necessary and keeping your attack surface to a minimum can help successfully manage the migration to cloud — safely and securely.
About the author

Srinivasan Gnanapiran
Senior Manager – Cloud Threat Management (CTM)