Getting Started with DevSecOps
DevSecOps represents the perfect mix of classical and futuristic IT concepts. While software development lifecycle (SDLC) best practices have been around for decades, the shift towards microservices, “everything-as-code” and DevOps has paved the way for enhanced security mechanisms and solution integration, increasing visibility, interoperability, and adding business value.
Whenever a new framework is implemented within an organization, a risk-reward analysis is necessary in deciding whether to adopt it. There is no difference between DevSecOps and other new potential processes, but taking a closer look at the concepts behind the buzzword may surprise you.
Despite your organization already checking marks against the DevSecOps items and maturity models, a lack of an organized way of working may prevent you from fully unlocking its potential.
What value does DevSecOps add?
As a business, it’s challenging to justify security, and we often forget that engineering goals directly impact business results, so embracing the idea of security-first is necessary. The security layer sits outskirt of development and operations as a protective layer, ensuring unified visibility into the entire process. DevSecOps ensures that no component goes without security, which also applies to the organizational culture.
By embedding a security-first culture into critical thinking, DevSecOps builds security and speed into every stage of the delivery process, from code writing to runtime. While the financial value it adds may not be evident at the beginning of the journey, in the end, DevSecOps delivers:
- Improved product quality
- Accelerated feature delivery
- Risk visibility across proprietary code and open source dependencies
- Lower remediation costs
- Minimized OSS-related breaches
- Optimized, effective security testing that is compatible with agile practices and tools
- Faster release of software with fewer rollbacks
Achieving an edge in the era of digital transformation
The increasing digital transformation rate accelerates software delivery, and creates risk, as threats and ransomware are becoming more frequent. Adding security as early as the code building phase reduces the risk of unwanted incidents and decreases the cost of rework. With a growing N-tier cloud architecture, quality software can be developed and deployed faster using the DevSecOps mantra of automating everything.
Essential considerations when adopting DevSecOps
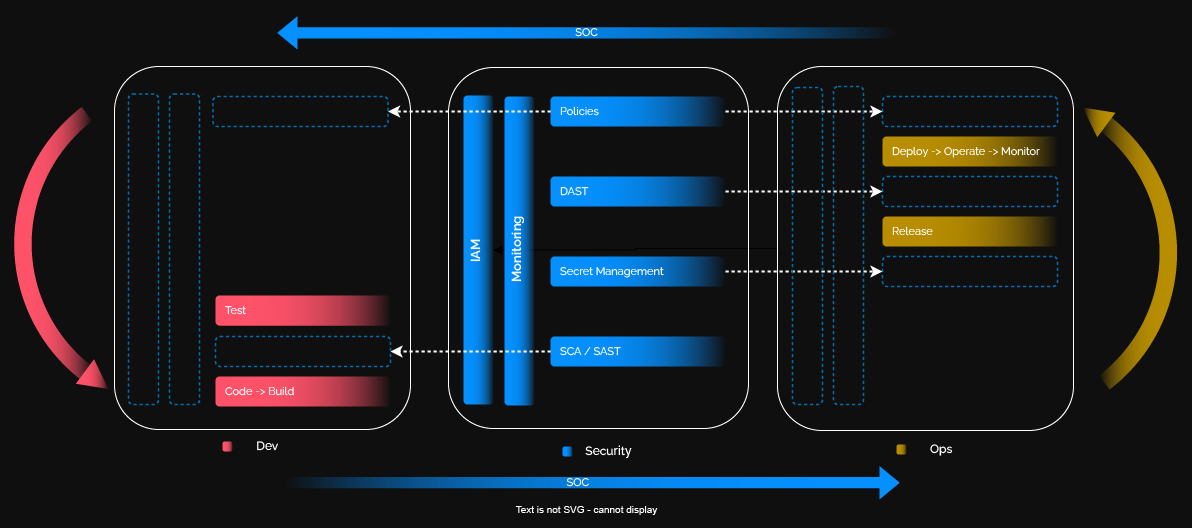
Migrating from DevOps to DevSecOps requires considerable investment, influenced by shifting left in the SDLC, adding tools and controls over the existing business model, and enabling the security team to detect and remediate threats, flaws, and policy disruptions. To do so requires a mesh of people, technologies, and processes.
Unless we automate the application’s upkeep, we run the risk of incurring technical debt. A shift to cloud edge enables transformative processes associated with DevSecOps and ensures a seamless integration. For minimal disruption risk during adoption, we recommend seeking support from an experienced security company.
Integrating security controls, tools, and processes at the beginning of the workflow leads to better deployments and cost reductions — enabling automated security checks and remediations at every stage in the software delivery, including:
- SCA – Dependency check to ensure OSS security compliance
- SAST – Static testing of the application code
- DAST – Dynamic testing of the deployed application during runtime
- IAM – Policy enforcement based on identity
Secret sprawl is one of the most common scenarios in which sensitive data is leaked due to a lack of control. More and more companies are looking for safer vault solutions that don’t just serve as static secret managers but also analyze, identify and react to breaches dynamically.
By involving trained security teams in DevOps, we believe the required capabilities can be created. A DevSecOps team adopts the mindset, tools, and practices, while a security operations center (SOC) team can identify and react to threats. Introducing security right from the start of the SDLC minimizes vulnerabilities in application code and ensures that developers and operations teams share responsibility for following best security practices.
How to measure the success of DevSecOps
DevSecOps success should be measured quantitatively by efficiency, quality, threat detection and release cycles. It is essential to track predefined key metrics, such as:
- Mean Time to Repair
- Mean Time to Recovery
- Frequency of deployment
- Lead time
- Code coverage (at least 80%)
- Detection count for threats, vulnerabilities
The faster a feature can be released and enjoyed safely by users, the sooner the business can generate revenue from that code.
Conclusion
The journey to DevSecOps will be smoother if a mature DevOps-oriented organization adopts a security-first approach in an automation-centric manner — along with strong management support for training and process change. DevSecOps is not a solution to be purchased, implemented, and left alone.
It sits on the shoulders of decades of continuous improvement, adapting to new technologies, and identifying the right skills and tools needed to improve the security posture of our software, infrastructure, and policies.
XaC – Anything as a Code
SDLC – Software Development Lifecycle
SAST – Static Application Security Testing
DAST – Dynamic Application Security Testing
SCA – Software Composition Analysis
SOC – Security Operations Center
SOAR – Security Orchestration, Automation, and Response
78%
of vulnerabilities are in transient dependencies
90%
of applications include open source
x2.5
OSS vulnerabilities have doubled in the past two years
About the authors

Bogdan Balazs
Cybersecurity Products Global Deputy CTO, Atos
As Global Deputy CTO, Bogdan is responsible for leading innovation and overseeing the global strategy within the BDS Cybersecurity Products unit.
As an experienced IT architect, he is actively involved in designing the future of Atos BDS value proposition by working together with customers, internal stakeholders, and partners on established and emerging domains such as IAM, PKI, Digital Identities, or Metaverse security while spearheading BDS cybersecurity vision and objectives in the realm of DevSecOps.
Bogdan is shaping the cybersecurity engineers of tomorrow by closely working with local universities in promoting BDS Digital Vision through teaching, events, and workshops.

Robert Chelu
Cloud Security Architect, Atos
Robert Chelu brings value through a broad experience as a small ex-business owner combined with a demonstrated working history in the computer software industry. As a Cloud Security Architect, he helps shape business delivery, safety, and automation through strategic implementations & integrations of effective Security Mechanisms like IAM, SIEM, Secret Management, SOAR, and Security & Risk Management. Additionally, Robert drives business growth by establishing vendor partnerships and deals while acting as an essential stakeholder in DevSecOps adoption.
