Data breaches occur when unauthorized individuals gain access to sensitive information kept by organizations. This information can be viewed in real time or exfiltrated for later use.
The stolen data can be used for various malicious purposes, causing disruptions far and wide.
According to IBM’s Data Breach Report 2022, the cost of a data breach has reached an all-time high, averaged USD 4.35 million, a 2.6% increase from USD 4.24 million in 2021.
The use of stolen or compromised identity credentials is the most common cause of a data breach. They were the primary attack vector in 19% of breaches stated in the report. The study also found that breaches caused by identity theft had the longest lifecycle, taking 243 days to identify and another 84 days to contain.
This article will compare the cyber threats relating to human and machine identities, discussing their similarities and differences before recommending a set of mitigation strategies based on digital identity technologies and prevention techniques.
Identity threats
A typical identity-driven cyberattack campaign begins with credential theft through a phishing email or other forms of social engineering, which trick individuals into providing sensitive information, such as usernames, passwords, or credit card details, by posing as a credible entity through emails, text messages or fake websites.
When attackers gain unauthorized access to a victim’s online account, they look for more information for exploitation or plan further infiltrations across the infrastructure.
Human identity threats and prevention
Computer systems are primarily designed to help humans to carry out specific tasks and goals. Although non-human entities like devices and programming functions are being used in automation, their configurations and maintenance are managed by people. This is why attackers prioritize human identities and behaviour.
The attack on human identities mainly focuses on the social aspects of their work and personal lives. Attackers conduct research on a target group or an individual using single or multiple infiltration techniques to increase their success rate. Common human identities’ breaching techniques are:
| Social engineering | Manipulating individuals via psychological tactics to obtain confidential information. This can involve impersonating a trusted individual or using deception to trick people into revealing sensitive information.
|
| Shoulder surfing | Covertly observing someone’s personal information, such as passwords or PIN, either by looking over their shoulder or spying on their electronic devices in public places.
|
| Public Wi-Fi eavesdropping | Intercepting sensitive information transmitted over public and unsecured Wi-Fi networks to gain unauthorized access to online accounts.
|
| Synthetic identity fraud | Creating synthetic information by mixing real and fabricated information. Fraudsters use this information to open accounts, obtain loans, or engage in fraudulent transactions, making detection and recovery challenging.
|
| SIM card swapping | SIM card swapping occurs when attackers convince a mobile service provider to transfer a victim’s phone number to a SIM card controlled by the attacker. This allows them to intercept calls and messages, gain unauthorized access to accounts tied to the phone number, or bypass two-factor authentication.
|
| Dumpster diving | Dumpster diving involves searching through trash or recycling bins to find discarded documents containing personal information, such as bank statements, credit card bills, or medical records. This information can be used for identity theft or other fraudulent activities.
|
Detecting human identity threats can be tricky, but there are several signs and practices that can help in identifying potential threats. The mitigation for reducing the human identity-driven cyberattack starts with basic security hygiene at a personal level.
Regular reminders and education programs for recognizing and avoiding phishing attempts are the best defence mechanisms against social engineering approaches for identity theft or account takeover. Here are few things to keep in mind:
| Recognizing social engineering techniques | Be cautious of individuals who try to manipulate or trick you into revealing sensitive information, such as passwords or account details. They may pretend to be someone you trust or use psychological tactics to deceive you.
|
| Spotting phishing attempts | Be wary of phishing emails or websites that mimic legitimate institutions, such as banks or government agencies. They often ask for personal information and may contain spelling or grammatical mistakes.
|
| Unexpected communication | Be cautious of unsolicited phone calls, emails, social media or text messages asking for personal or financial information. Legitimate organizations usually do not request sensitive data through these channels.
|
| Unusual account activity | Keep an eye on any suspicious activity in your system/financial accounts, such as unauthorized transactions, changes in account information, or new account openings that you did not initiate.
|
| Unauthorized access | Regularly review your login history and access logs for online accounts. If you notice unfamiliar IP addresses or login locations, it could indicate unauthorized access.
|
| Keeping up with data breach notifications | Stay informed about data breaches and security incidents that may expose your personal information. Monitor news and announcements from companies in which you have accounts.
|
| Apply strong passwords and multi-factor authentication (MFA) | Use unique, complex passwords for each online account and enable MFA whenever possible. It adds an extra layer of security by requiring a verification code in addition to your password.
|
| Secure Wi-Fi and devices | Protect your Wi-Fi network with a strong password and encryption. Ensure your devices have up-to-date security softwares and operating systems.
|
| Shredding sensitive documents | Shred financial statements, bills, or any documents containing personal information to prevent dumpster diving.
|
Machine identity threats and prevention
Machine identity threats are the risks associated with the breach or misuse of digital identities assigned to machines, devices, or software applications.
These threats can have significant consequences, ranging from data breaches and unauthorized access to system malfunctions and cyberattacks. The common security incidents related to machine identities are:
| Data breaches | Machine identities are often used to secure data transfers between machines and authenticate machine-to-machine communications. If these identities are compromised, it can result in data breaches, exposing sensitive information to unauthorized individuals.
|
| Unauthorized access | Compromised machine identities can grant unauthorized access to critical systems, networks, or data. Attackers may exploit weak or stolen machine identities to impersonate trusted machines and gain entry to sensitive resources.
|
| System malfunctions | Compromised machine identities can disrupt critical systems and services. By misusing or manipulating machine identities, attackers can cause system failures, interrupt business operations, or manipulate machine behavior for malicious purposes.
|
| Cyberattacks | Machine identities can be targeted to distribute malware or ransomware. Attackers may tamper with machine identities to spread malicious software, enabling them to infect other machines or hold organizations hostage for ransom.
|
Machine identities are used to uniquely identify non-human providers or consumers of physical devices and data services.
These identities are often found in operational technology (OT), Internet of things (IoT), automation programs and system integration softwares. The common infiltration strategies targeting machine identities are:
| Supply chain attacks | Attackers may compromise machine identities at various device lifecycle stages by gaining control over machines or introducing backdoors during manufacturing, shipping, or installation of devices. |
| Insider threats | Machine identity threats can arise within an organization. Malicious insiders can abuse machine identities to carry out unauthorized actions, bypass security controls, or steal sensitive information. |
| Digital certificates and SSL/TLS | Machine identities are commonly managed using digital certificates, particularly for securing communication over the internet. If these certificates are mismanaged or stolen, it can lead to security vulnerabilities and enable attackers to intercept or manipulate data. |
| IoT/OT Security | Weakly secure machine identities in IoT/OT devices can allow attackers to gain control over connected devices, leading to privacy breaches, data manipulations, or disruptions in IoT/OT ecosystems. |
When mitigating the risks of a machine identity attack, it is vital to have rigorous control over how machine identities are created, updated and removed throughout their lifecycles.
Examples of best practices for protecting machine identity are:
- Implementing robust identity and access management (IAM) practices.
- For example, enabling MFA for all access credentials, applying principle of least privilege access to reduce attack surface, regularly monitoring IAM configurations and auditing how the assigned access is being used. To learn more about the role of cybersecurity hygiene, click here >>.
- Regularly updating and rotating machine identities
- Enforcing strong encryption and authentication mechanisms
- Monitoring and analyzing machine identity activities
- Raising awareness among employees about the importance of securing machine identities
Preparing digital identities for zero trust implementation
The rise of cloud computing, mobile devices, and IoT/OT devices has made securing corporate data more difficult. The traditional approach to network perimeter security is no longer effective. As a result, the zero trust security model has gained popularity.
Zero trust scrutinizes every access request by evaluating the requester’s identity, context, and situational information. It follows the principle of “never trust, always verify,” granting access based on verified identities and minimal privileges. It provides granular control over data access, reducing the risk of unauthorized access or breaches. It focuses on continuous verification regardless of the request’s origin. Adopting zero trust enhances data security in the evolving digital landscape.
The main benefit of adopting a zero trust approach is reducing the risk and impact of a security breach by limiting lateral movement of an attacker. Our interpretation of zero trust is creating an easy-to-use, dynamic and context-based access control mechanism in real-time, which will protect your information assets no matter where they reside. The illustration below describes our zero trust framework from left to right.
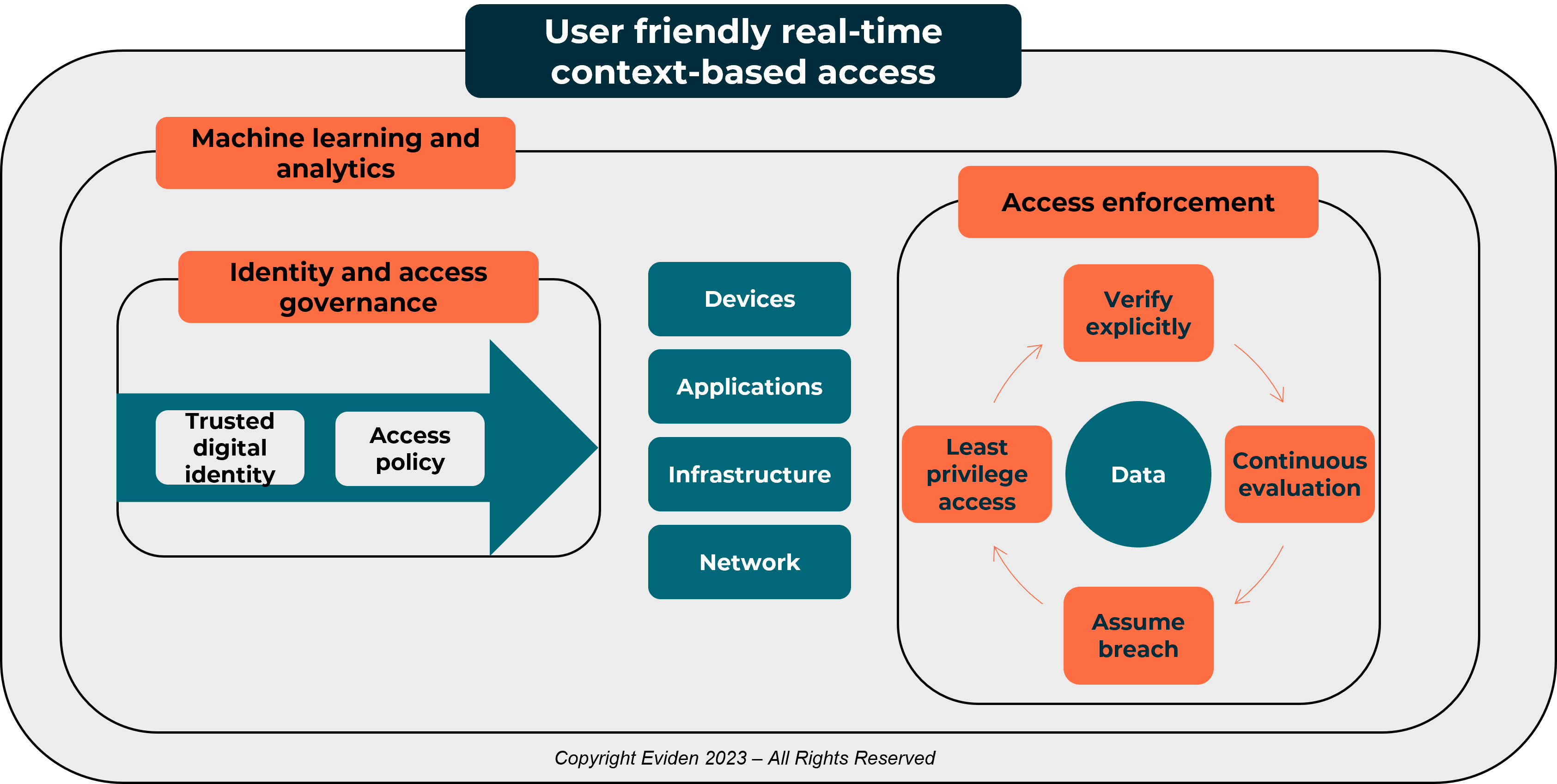
Figure 1 – Eviden’s context-based access control using zero trust principles
All domain access to the right, including devices, applications, infrastructure, network and data, are controlled by the following:
- A verified digital identity
- A policy defining what the identity can access
- A governance and control mechanism to ensure least privilege access.
This is called identity and access governance. There is no distinction between human or machine identities when it comes to zero trust implementation. In addition to people, any important information (data) and resources (device, applications, infrastructure, network) will get a unique digital identity. The lifecycle of each unique digital identity and access privilege will be explicitly manged and monitored based on a pre-defined access policies.
To the far right, we have access enforcement to the data domain that determines whether the identity in question can access the protected information. To deal with the complexity and volume of requests, machine learning and analytics technologies are needed to ensure dynamic access control and safeguard corporate data by scrutinising every single access request.
There is no single product that can deliver this kind of control today. To achieve the desired outcomes, it will take a series of continuous integrations across multiple technical security controls, such as identity and access management, data loss protection, application security, workload protection and network security.
Important takeaways

The most common cause of data breaches is the use of stolen or compromised identity credentials.

To protect against cyber threats, it is crucial to have effective lifecycle management of identity and access to valuable data.

Mitigating human identity-driven cyberattacks begins with practicing basic security hygiene at a personal level.

Regular reminders and education are crucial in helping individuals identify and tackle phishing and unexpected communications. They also enable them to fight against social engineering tactics used for identity theft and account takeover.

To mitigate machine identity attack risks, implement robust IAM practices with regularly updated machine identities and enable strong encryption across all interactions with the machine.

Continuously monitoring machine identity activities will help you identify any sign of intrusion and increase employee awareness on securing machine identities.

Apply a holistic data protection using the zero trust approach. Prepare machine and human identities in the same way. Enable rigorous identity and access governance mechanisms with continuous monitoring of activities. This will significantly mitigate the risks and minimize the impact of cyberattacks.
References
Cost of a Data Breach Report 2022, IBM Security
About the author
Aaron Chu
Advisory Practice Director, Enterprise Architecture and Identity

Aaron Chu is Advisory Practice Director, Enterprise Architecture and Identity, Eviden Northern Europe
Aaron joined Atos in 2006 and successfully delivered several large-scale cybersecurity transformation programmes for Media, Finance and Public Sector industries. He is also a Senior Atos Expert specialises in Identity and Access Management and being a vocal advocate of “identity is the core foundation of building trusted business”.
His current focus is helping customers achieving a trusted business and operating environment by applying an end-to-end business centric and risk driven cybersecurity approach. Aaron is currently leading several enterprise security architecture and zero trust advisory projects for Insurance, Health and Manufacturing customers in Europe.