Indisputably, connected devices have been a milestone in general technological development. Both small devices like smartphones, wearable IoT (Internet of Things) and the bigger ones, like connected cars, facilitated the life of millions of users so far.
The fourth industrial revolution has also relied a lot more on the IoT devices than ever before, coining the term of “industrial IoT” – and this is just the beginning. Visionaries tell us stories about the future where all aspects of our life will be steered by “intelligent” machines connected into one global network.
But, before the future from “the Jetsons” fully materializes, we should already now consider and address the risks related to this technological revolution.
What risks will connected devices bring and how will the security landscape evolve to prepare to these threats?

EU sets the baseline for securing connected devices
Let’s start with the view on how governments are preparing to secure their citizens against risks and vulnerabilities coming from connected devices.
The EU is already adjusting the law to the ever-changing landscape of connected devices: Cyber Resilience Act, proposed by the EU on 15th of September of 2022, recognized the increasing number of threats coming from lack of proper control and security testing of the devices produced by the manufacturers.
Therefore, it imposes defined security baselines on the hardware and software manufacturing companies that need to be complied with. The aim of the Act is, on one hand to ensure that manufacturers will release their products with as little vulnerabilities as possible, and on the other hand, to share awareness between millions of users, who, whenever buying a new connected device, will be aware of the risks it may bring and make informed decisions.
As July 27, 2023 amendments, the law will set grace period:
- 18 months for reporting of vulnerabilities and incidents
- Three years to adapt to the new requirements.
According to the Act, the EU manufacturers will be obliged to timely report any detected vulnerabilities and incidents to respective authorities. Moreover, the reporting obligation applies penalties on the companies that will fail to comply.
According to the Act, the member states need to define the appropriate authority and channel; however, ENISA (The European Union Agency for Cybersecurity) plans to establish one common platform that will enhance the communication and information exchange between national CERT organizations of the member states. In this way, the reporting and reaction will be streamlined as part of international cooperation on preventing security attacks.

Mobile security is more comprehensive than ever
What initially intended to be just a mobile version of the ordinary, corded phone, became a computer and powerful tool in itself. It can be used for work, taking and editing photos, communicating with the others, or even as personal ID; however, what seems to be a great facilitation in daily life, brings also huge risk.
Apart from mobile phones, there are also tablets that also work as small computers. The amount of personal data stored in their applications is tremendous, and very often not proportional to security measures applied and, once the mobile phone is lost or stolen, one realizes that the real value lost was not the mobile device itself, but all the information that it stored.
Another risk related to extensive use of mobile phone in business is that, in case it gets infected, it can become a new channel to get into the corporate environment. And, let’s admit, users rarely think about security when they, for example, connect with their mobiles to a public, unsecured network. That is why it is important to not only secure mobile devices from physical perspective (logging in or anti-theft measures), but also their applications, connectivity etc.
How does the security landscape adapt to secure mobiles? The truth is, although the mobile security is extensively developed, due to OS limitations it is not yet the same as for the workstations or servers. Nevertheless, they can be very useful in securing the precious data stored inside the mobile device.
Current solutions enable security of mobile devices from various dimensions:
- Application security posture – mobile security solutions can give you the scoring of applications that you have on your mobile and inform you about the reason for that scoring; this allows the user to make an informed decision about applications installed on their mobile device and, if needed, take appropriate actions;
- Part of the overall end-to-end security – logs gathered from mobile devices feed modern MDR, SIEM and XDR solutions to provide full picture of enterprise’s security and helps recognize IoAs (Indicators of Attack) and IoCs (Indicators of Compromise) in time;
(If you would like to find out more about differences between MDR, SIEM and XDR, this is well explained by Eviden Global CTO Digital Security, Zeina Zakhour, in the following article: https://atos.net/en/lp/digital-security-magazine/demystifying-the-detection-and-response-industry-a-tongue-twister-of-acronyms )
- Response, forensics and SOAR (Security Orchestration, Automation and Response) – modern solutions can support automatic response to particular actions, notifying the user of the situation and imposing actions that need to be done to secure the device;
- Access management – multi factor authentication before accessing applications located in the mobile devices , as well as using biometry/gestures/strong passwords to unlock the device itself is simply a must;
- Data protection – by separating business from private profile (applicable for COPE – Company Owned, Privacy Enabled) helps to keep the data within the corporate profile. In this example, data from corporate profile cannot be copied into the private profile.
Modern ways to secure personal and industrial IoT
Smart homes, cities, factories opened a completely new dimension for security. Recent attacks on public infrastructure have raised the awareness that even traffic signals can be hacked, significantly impacting the life of ordinary people. It’s been already five years since Ken Munro in his TEDx Talk “Internet of Things Security”, showed how dangerous a wi-fi kettle or a doll can be to the safety of a household. That leads to challenging security vendors to adapt their measures and products to various kinds of devices, with their communication protocols, operating systems and standard differing a lot from the traditional kinds of endpoints.
The specifics of IoT makes it challenging to get the same level for security as e.g. laptops. On many systems it is not possible to even install the agent, which limits a lot the possibility to react quickly on the endpoint itself (e.g. via SOAR). There are dedicated solutions developed already by market EDR leaders that can work both agent-based and agentless, but definitely the first option gives a lot more possibilities to control the endpoint.
Therefore, solutions that we know for IT, need to be specifically crafted and adjusted for IoT devices.
The examples mentioned above come from smart homes, but what about industrial IoT, where the devices need to be onboarded quickly and safely to the environment, and later on controlled properly in terms of their security posture?
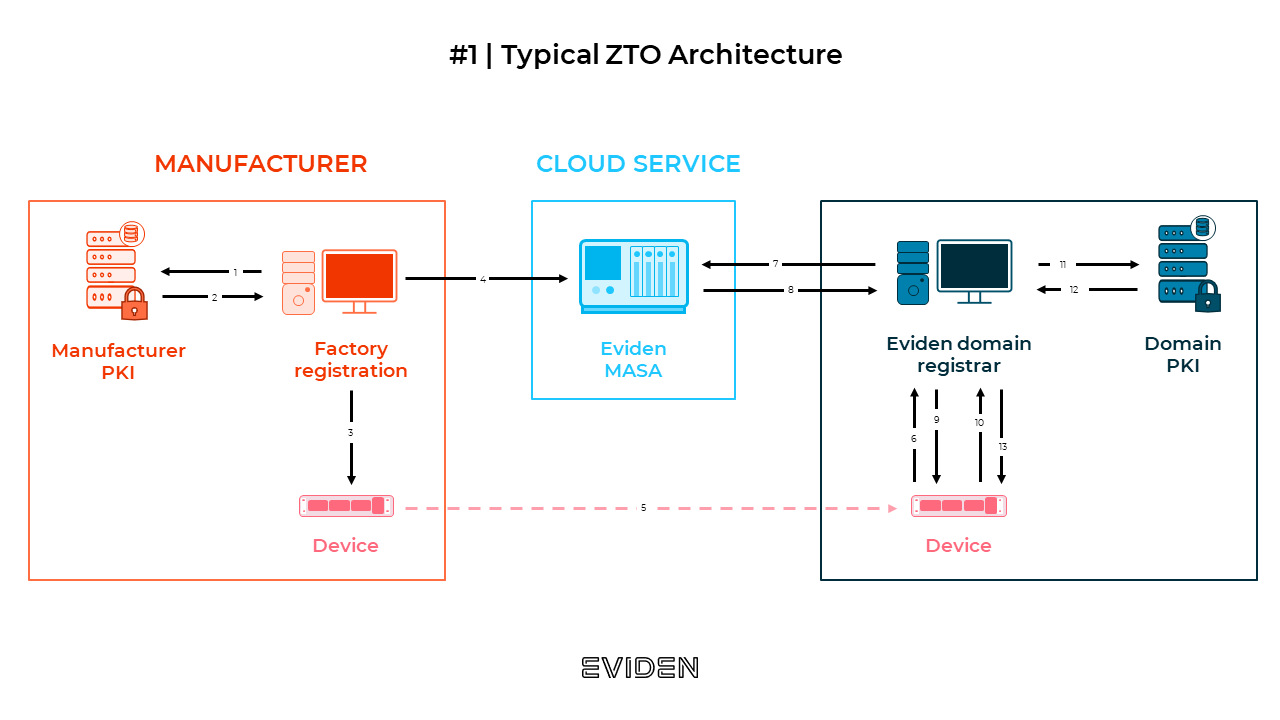
To answer the needs of industrial IoT, Eviden is currently preparing a solution called Zero Touch Onboarding (ZTO). It offers a way to securely connect new industrial devices with your network, minimizing the risk of e.g. DDoS attacks. Zero Touch Onboarding, as the name itself reveals, will also use automation to substantially reduce the time to configure a new device and install it in the new environment.

How does ZTO work?
Traditional way of connecting new devices to the environment assumed configuration, registration of the device, recording it in the commissioning tool and other activities – all of them had to be done manually, which not only meant high, unnecessary workload, but manual activities that are also more prone to errors and could result in incidents. In turn, in ZTO architecture, a device gets its immutable identity and keys already in manufacturing site and another, local identity in customer site. In this way, the device is secured from the very beginning, even before it reaches the customer’s site. Later on, thanks to automation, the manual registration process is not necessary – the device is ready to robust operations and secure communication in a very short period of time.
Having strong background in identity management, Eviden supports this process by providing main components of ZTO architecture:
- MASA (Manufacturer Authorized Signing Authority) – a trusted authority to check that device comes from reliable, recognized manufacturers;
- Domain Registrar – which operates as a local entity allowing the device to retrieve a certificate in an automatic and secure way;
- Domain PKI to issue to device digital certificates and ensures that their ZTO solution is fully compliant with IETF standards.
Another very prominent area where connected devices are quickly developing is the automotive market. Although the first connotation with “intelligent cars” may be Tesla, nowadays the concept of connected car or connected fleet is developed by all manufacturers. And it’s not as new as we may be thinking: the implementation of ECUs (Electronic Control Units) that gather information on the various parts of the vehicle and their performance, started already in the ‘70s.
Statistics shows though that this enhancement may bring considerable risk – from data breach and break-ins to various frauds, location tracking or even malware – cars need to be now protected just like any other type of connected device.
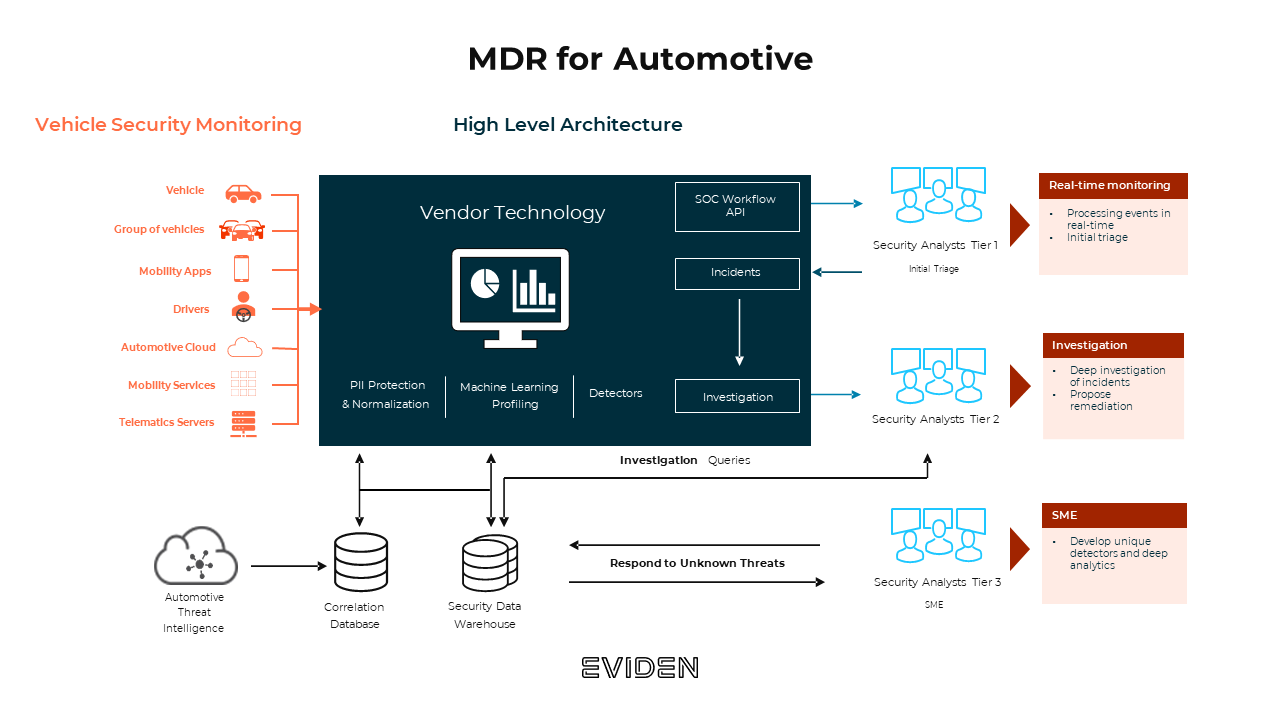
This need is already addressed – the market offers solutions proficient in securing vehicles. One of the examples can be Eviden’s MDR for automotive service. For this service, Eviden partners with 3rd party automotive security solutions that gather the data from vehicles, mobility apps as well as the automotive cloud itself and can further feed Eviden’s MDR solution. Using AI and machine learning, adjusted specifically to automotive protocols, the tools are able to detect anomalies and notify the security operations team that, in turn, initiates a respective incident response procedure. In this way, connected fleet can be effectively secured.
To summarize, connected devices already cover and facilitate many aspects of our private and professional life, which means, they need to be secured more than ever in history. However, both the states and private manufacturers as well as cybersecurity vendors and service providers alike see this growing threat and are already adapting the law, products and services to address it.
It’s important though to be aware of the risks that may be brought to our homes, offices etc. when using connected devices and, when using them, not only rely on the technology itself, but also on our common sense. Some basic security measures (like not leaving mobile phone in a public place or not connecting to public, unsecured wi-fi) can spare us a lot of stress that may be caused of lost data, valuables and even public image.
References:
Cyber Resilience Act: https://www.europarl.europa.eu/doceo/document/A-9-2023-0253_EN.html
ENISA (The European Union Agency for Cybersecurity) website: https://www.enisa.europa.eu/
Process description for enforcing Cyber Resilience Act: https://oeil.secure.europarl.europa.eu/oeil/popups/ficheprocedure.do?reference=2022/0272(COD)&l=en
About the author
Gabriela Gorzycka,
Global Head of Endpoint Threat Management

Gabriela Gorzycka is the Global Head of Endpoint Threat Management at Eviden.
In her role, Gabriela is mostly focused on strategy and management of delivery of cybersecurity services to over 150 customers out of numerous locations worldwide.
Her main areas of focus are endpoint protection, data protection, mobile and IoT security services, and among the others are Endpoint Detection and Response, Encryption or Data Loss Prevention. She has been a member of Atos’ Experts community, focusing her research and expertise on IOT and OT security.
She also has a strong process background (ITIL V3 Expert) and holds ISO certifications in Service Management and 20000 and 27001.