What is sovereignty and why it does matter?
What is sovereignty and why it does matter?
Preparing organizations for a sovereign digital future
Dear community members,
Welcome to the sixth edition of Atos Digital Security Magazine! In this edition we will tackle the strategic need to put digital sovereignty at the heart of the digital revolution.
In a world where most data is processed and stored across geographical borders, often using foreign technologies, many governments are raising valid concerns around data, technological and digital sovereignty.
In this edition, we will address many aspects of digital sovereignty — not just because the term itself may be overused, misused or misunderstood — but because there are very important underlying ideas that need to be clarified before strategic decisions are made.
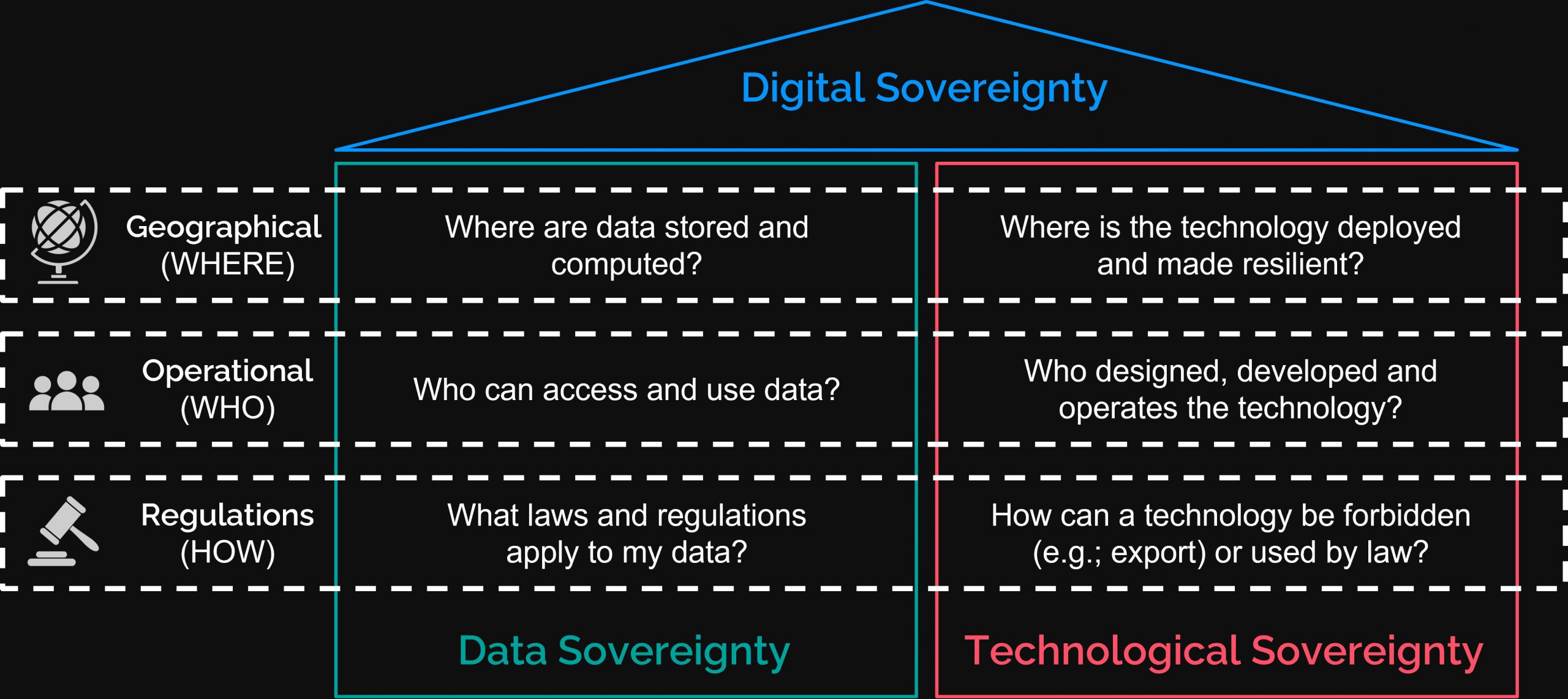
Indeed, it is crucial to agree on the definition of sovereignty in the digital world. Data sovereignty refers to the degree of control an individual, organization or government has over the data they produce and work with (whether local or online). In contrast, technological sovereignty is the degree of the control the organization has over the technology it uses.
Data sovereignty and technological sovereignty are the two pillars of digital sovereignty, which can be defined as the degree of control an organization has over its entire digital environment, including data, applications, software, systems, and hardware. Which is aligned to the WEF definition “the ability to have control over your own digital destiny – the data, hardware and software that you rely on and create.”

Zeina Zakhour
Vice President Global CTO – Digital security
Member of the Atos Scientific Community

Vasco Gomes
Global CTO for cybersecurity products, Distinguished Expert
Member of the Atos Scientific Community
A closer examination reveals that cybersecurity is at the heart of data sovereignty and helps enhance technological sovereignty.
It’s important that organizations understand that digital sovereignty is not an “all or nothing” proposition. Digital sovereignty exists in varying degrees on a scale which is constantly in flux.
Governments and organizations advocating for digital sovereignty need to adopt a risk-based approach. They must carefully assess their level of control over data and technology, and take great care to ensure that sovereignty does not come at the cost of agility — a key factor to thriving in the Digital Age.
As many organizations make the massive move to the public cloud and embrace mobile/remote working (which has greatly accelerated during the COVID-19 crisis), they must measure the risks to their digital sovereignty. When they delegate technological choices data hosting and data processing to a provider, they put themselves at the mercy of that provider and its respective regulatory authority.
As a result, a hybrid cloud approach is gaining significant traction. Hybrid cloud leverages several different cloud solutions in parallel: from the least trusted to the most trusted, or even a disconnected, on-premises deployment. Data can be processed and hosted in different environments, depending on its business sensitivity.
This modular approach helps organizations leverage the potential of large providers to enhance the competitiveness of their less sensitive business processes. At the same time, they can protect their most sensitive business processes by keeping them under their own control or the control of more trusted providers.
Most importantly, organizations should not overlook the fact that digital sovereignty can become a competitive advantage by putting data sovereignty — and consequently, trust and transparency — at the core of their digital transformation.
Digital sovereignty is a growing concern in our increasingly digitalized world. Yet, policy makers, governments and enterprises must master the art of balancing digital agility with digital sovereignty, as this will be key to competitiveness.
In this edition of Atos Digital Security Magazine, we will answer some important questions about digital sovereignty:
- How and how much should I increase the control I have over my data?
- How do I measure that degree of control in the first place?
- Does the nationality of a technology provider matter?
- Given the growing extraterritorial nature of some laws, how much does physical location matter?
- Are there architectural concepts and ideas that can foster digital sovereignty?
- How can CISOs support the development of digital sovereignty and autonomy?
Thank you for reading, and we hope you will benefit from these insights and observations!
Be the first to know the latest insights from the market.
The cybersecurity community is growing and is nurtured by the deep knowledge provided by the experts.
Register to our newsletter to be informed first of the release of next editions of Atos Digital Security Magazine.
It is each quarter, free and you can read it anywhere.

