Prescriptive IAM: anticipate trends, identify risks and [re]act automatically
While the deployment of Identity and Access Management (IAM) processes might still be behind the curve in some organizations, many companies have now reached a level of maturity that enables them to exploit most of the traditional and strategic features delivered by IAM solutions.
However, due to the complexity of governing identities and access in today’s information systems, the deployment of IAM in an organization does not signify the end of the close attention a security officer will have to dedicate to IAM.
Over time, new users, business processes, networked infrastructures, cloud applications and marketplaces mean that security administrators will struggle to stay confident on their IAM policies and configurations. They must constantly verify that the original strategy they put in place remains efficient. They’ll have to anticipate trends that could impact the settings they decided on. Of course, they will also have to detect and protect from both external and internal threats that could affect or misuse IAM technologies and assets.
Augmenting IAM processes with hybrid artificial intelligence
Prescriptive IAM is our answer to these tough challenges that security officers and administrators face. Our goal is to arm them with tools that not only predict problematic situations, but also anticipate risks and propose solutions to avoid that problems occur. Prescriptive IAM is not just about recommending corrective actions, but about [re]acting automatically!
What help do we then expect artificial intelligence (AI) to contribute to IAM?
First, we expect AI to think and anticipate situations instead of security officers, mimicking the administrators’ brain. It should help define both high-level and detailed rules, to be alerted when conditions are met or thresholds are crossed. Doing so, it would emulate the decision making ability – or reasoning – of a human expert. This is the role of symbolic AI.
Symbolic AI is implemented in decision management systems or business rule management systems. Rules are easy to understand for developers and security officers. They can be easily maintained, and modified and deployed without stopping the IAM solution. Because you define them, rules only help detect situations that you’re explicitly searching for.
Security officers would also expect AI to highlight facts that are invisible to them – the proverbial needle in a haystack. This is the role devoted to statistical AI, or machine learning. It applies when the nature of the problem is complex, with too many variations and nuances to be covered by a well-defined set of explicit rules or concepts. Machine learning is a mathematical approach, where the system analyzes the data for certain patterns. The ingenious part is that the system determines on its own which patterns to look for, learning from thousands of examples. The system implicitly learns the rules that we cannot write down explicitly.
Our prescriptive IAM combines these two technologies, as an innovative hybrid AI approach.
How to plug it into an IAM infrastructures?
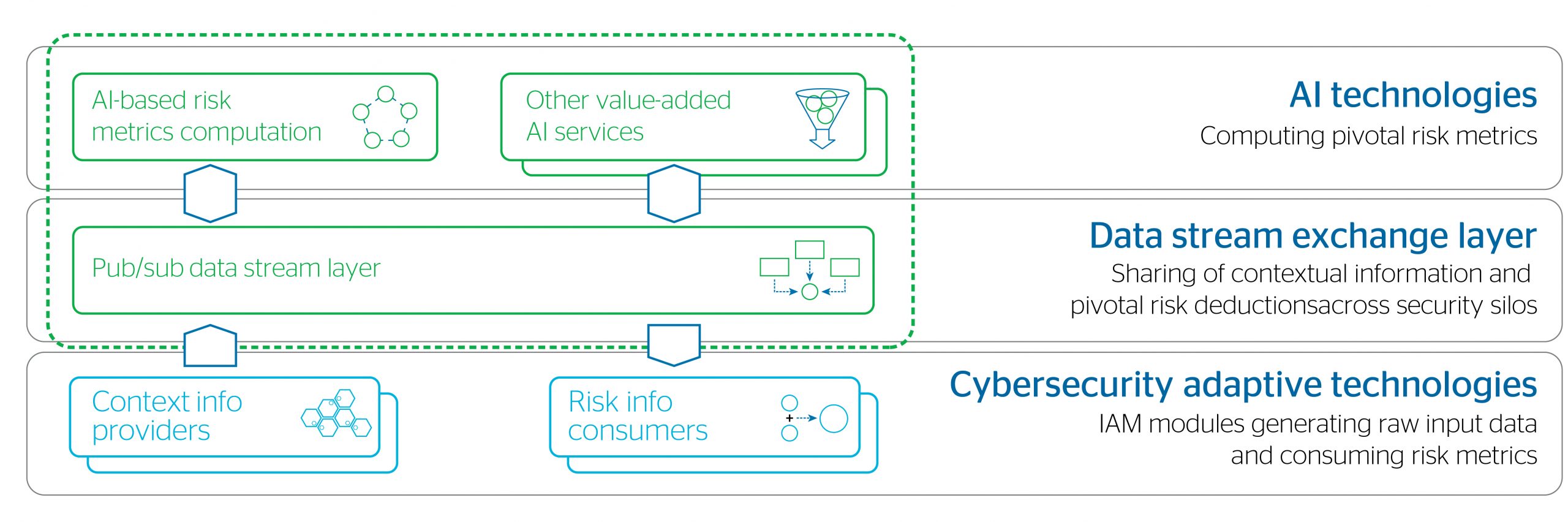
To avoid any big bang effect, our hybrid AI must adapt smoothly to existing IAM deployments. To do so, we consider risk as the pivotal notion between any source of meaningful data and the IAM modules. The notion of risk is intuitive for humans and can be easily interpreted and exploited by computers.
The prescriptive IAM is based on a future-proof design, leveraging a high throughput data stream exchange layer, which is in charge of sharing contextual information and risk deductions. It is cloud-ready by design, to the deliver horizontal elasticity mandatory for supporting huge amounts of data. This incoming information is stored in a data lake, where symbolic AI and statistical AI take their input from.
Most importantly, the architecture is open, so clients and third parties can plug in their own AI modules with specific objectives and risk computation algorithms – yet still interoperate seamlessly with IAM modules deployed in the organization.
Contributing to a global zero trust approach
At its core, the zero trust principle is based on the fact that traditional perimeter security is no longer sufficient. Usages and threats evolve rapidly, so there’s no trust by default anymore.
By collaborating with all security stakeholders and analyzing 360° insights about all activity, prescriptive IAM contributes to implement zero trust. Through the computation of pertinent risk metrics, the deductions from hybrid AI deliver adaptive access governance and control.
The overall added value of prescriptive IAM is to increase the security of access control to align with the zero trust approach. It helps security officers anticipate actions related to identity and access governance. It enforces adaptive security decisions with contextual awareness, not the simple black-or-white decisions that we see today. It will collaborate with all adjacent security domains, including security operations centers, user behavior analytics, threat intelligence and data loss prevention.
With AI-augmented identity and access management capabilities, we can make prescriptive intelligence actionable, acting automatically and adaptively on all IAM processes.
About the author

Thierry Winter
CTO Evidian IAM products and member of the Scientific Community, Atos
Graduated from the French Ecole Nationale Supérieure des Télécommunications, Thierry Winter started his career within the software department of Bull, by carrying out projects for network and applications management. He has filed several patents on QoS management and security.
In 2000, he took the lead of the security R&D of the Evidian company, with a focus on Identity and Access Management. As part of his duties as Evidian CTO, he’s driving the Research and Development activities for the different Evidian product lines.
He has participated in many Eureka, FP7 and H2020 collaborative projects, targeting security governance. He has been the initiator and project coordinator for three successful terminated ITEA projects; two received the golden achievement award in 2002 (PEPITA) and 2011 (MULTIPOL).
Distinguished Expert, member of the ATOS Scientific Community, Thierry is co-president of the Cyber&Security Hub in the Systematic Paris-Region ICT cluster.
Interested in next publications?
Register to our newsletter and receive a notification when there are new articles.
 Download the magazine overview
Download the magazine overview