Applying zero trust concepts in digital workplace
The digital workplace platform
As companies move towards a modern digital workplace, the platform on which it is built is becoming increasingly cloud-based and uses modern, secure authentication and communication standards and protocols. It will typically consist of:
- A cloud-based authentication and authorization solution with multi-factor authentication (MFA) included as standard
- Device management including provisioning, patch management and application management
- Threat and vulnerability management
- Collaboration tools and services
- Policy enforcement points/conditional access
- Data classification, labeling and protection solution
- Data loss prevention controls, both on devices and within the collaboration services
Simply by BUILDING and MOVING to a
modern digital workplace platform,
you can increase the security posture
of the workplace and
lay the foundation for adopting zero trust.
Zero trust and digital workplace
Zero trust originated in 2003 as a micro-segmentation approach to controlling access to services, but it has proven challenging to implement. One of the primary reasons why zero trust has not yet been widely adopted is its limitations when dealing with the cloud-based SaaS services of today’s digital workplace.
Zero trust evolved between 2014 and 2017, championed by Google, Microsoft, Forrester and Gartner. This evolved approach provides access controls to services and data based on both user identity and device identity. Policy enforcement points are used to validate the user’s identity, authorization to access a service and device posture. For example, to verify that the device is registered, managed, encrypted, patched, not jailbroken, compliant with defined security policies and in a trusted location. This approach to zero trust can also be combined with the micro segmentation approach for on-premises applications and services if required.
Complex enforcement rules can combine the user and device identities to decide, for each service, whether to allow or block access to the service, request additional user authentication, or allow restricted read-only access based on the risk and compliance measures.
I have been fortunate enough to help many digital workplace clients take the first step towards zero trust. Very few of them realize just how easy it is to begin improving the security of their services and reaping the benefits of zero trust with only a few small changes.
Companies that have completed the journey to a modern digital workplace find that adopting zero trust becomes easier and benefits can be realized much faster. Most of the key components for user and device identity, compliance and policy enforcement points are already part of the solution — but are rarely employed in the context of zero trust.
The integration challenge
The biggest challenge for digital workplace customers who want to continue their zero trust journey is encountered by those with a mixed approach or a best-in-class approach (rather than a vertically integrated approach) for vendor and product selection. For example, a best-in-class product for threat or identity management may not be the best fit product for the zero trust model.
It is important to understand that vendor and product choices in a digital workplace will impact the zero trust journey. A level of integration between the components is required to enable policy enforcement points — to validate both users and devices in a comprehensive manner using triggers based on behavior or threat level.
When I started looking at zero trust in 2018, I understood this integration challenge and built a tool for solution architects that uses a matrix of integration data between various vendors and products. The tool enables us to model the current and future modes of operation for the zero trust journey based on the client’s vendor and product selections. The sample output is shown in below.
| Zero Trust Readiness | 100% | Status |
| Identity and Access Management | ||
| Azure AD | |
| Device Management | ||
| Intune / Co-Managed | |
| Threat Management | ||
| Microsoft Defender for Endpoint | |
| Zimperium zIPS | |
| Microsoft Defender for Endpoint | |
| Policy Enforcement Points | ||
| Azure AD CA | |
| Cisco ISE | |
| Pulse Secure | |
| zScaler IA | |
| McAfee SkyHigh | |
| zScaler PA |
Today, there are still no common standards for sharing risk or threat information between vendors and products. Most vendors have built direct integration between their product(s) and sources of risk/threat data, but this integration varies with the mix of products being used. Understanding and using this in product selection for digital workplace solutions is key to zero trust success.
Applying zero trust in the digital workplace
Below is an example scenario that helps illustrate why zero trust is a powerful force for good and not just a marketing gimmick. It illustrates the key data flows between digital workplace components.
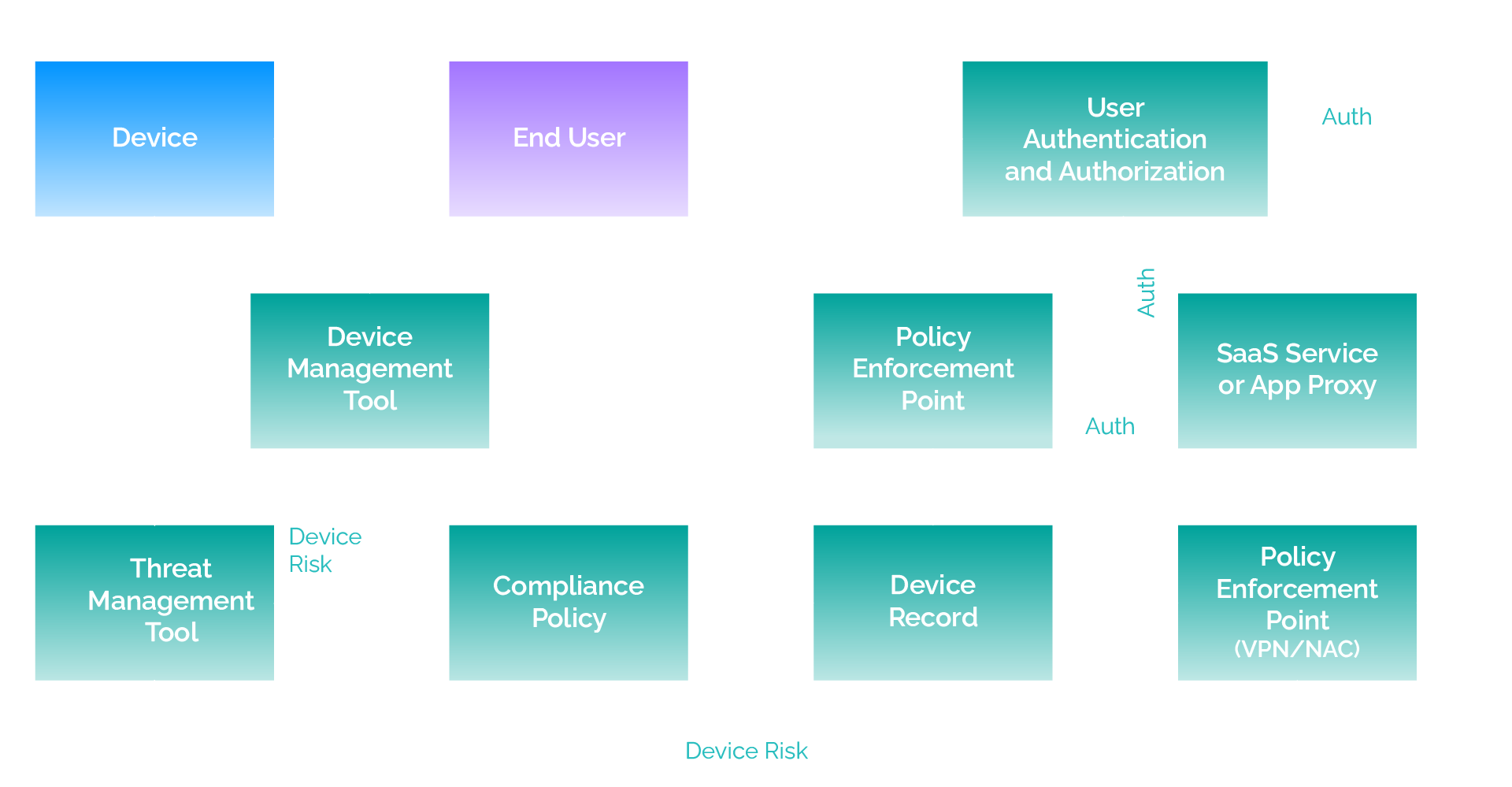
Let’s say a user opens an email with zero-day malware attached as an invoice from a supplier. The threat protection agent on the device identifies the risky behavior, even though it cannot 100% identify the attachment as known malware. It informs the threat management tool, which then raises the device risk to medium.
Because the threat management tool is integrated as part of a zero trust model, the device management tooling is now aware of the device risk change and marks the device status as non-compliant in the device record based on compliance policy rules.
The user attempts to connect to the corporate network via VPN and is prevented from doing so, since the VPN solution is acting as a policy enforcement point. It is integrated with the device management tooling and has queried the device status as part of policy enforcement, so it now knows that the device is non-compliant. The user then attempts to access a SaaS service (such as Microsoft 365 or Salesforce) but is prevented from doing so — or is only allowed to access a limited scope of services based on the policy enforcement point rules.
In the background, the threat management tooling has received similar signals from multiple devices in the organization, so it raises the device risk for all of them to high based on the policy enforcement point rules. This effectively isolates those devices from any company resource.
Meanwhile, the security operations center (SIEM) has already been alerted by the threat management tooling and the case is under investigation. The threat is eventually remediated, the risk level returns to normal, and the user can once again access the applications and services.
The result is a fully automated and immediate enforcement
of zero trust security policies, driven by the basic components found in any modern digital workplace. They can be applied to any SaaS application that uses an identity provider with a policy enforcement point/conditional access functionality integrated with a device management solution, VPN, NAC or PROXY solution able to query the device’s compliance status. The same scenario could work for any of the available compliance measurements – device not patched, device not encrypted, device jailbroken, etc.
At a time when digital workplace has evolved so quickly, zero trust has become a key path to keep data safe and regain control. The way forward to success in this transformation journey will inevitably rely on how well zero trust will be integrated and automatically enforced in the digital workplace.
About the author

Simon Hardy
Digital Workplace CTO, Atos
Simon has been with Atos for over 25 years and is currently working as a CTO within the Digital Workplace CTO Office helping to define future strategy, innovation and participating in customer innovation and solution workshops. Prior to this Simon was the Global Digital Workplace Chief Architect within the Global IDM WSDS team leading the technical design and evolution of the Atos Digital Workplace offering and was the architect behind the Atos CHESS 2.0 program that moved 80,000 Atos Windows devices to be Azure AD Joined, Windows 10 and fully cloud managed by Intune between 2018 and 2019 where Atos become one of, if not the largest, consumers of Intune cloud managed Windows 10 devices at the time.
Previously Simon has held positions within Global Portfolio as a Product Manager and Portfolio Architect, UK Portfolio as a Technical Design Authority, Technical Consulting as a Practice Manager and before that a Senior Consultant working with some of the most security conscious customers in the UK.
Simon lives in Kettering, England with his wife and 2 children and collects and restore old video games consoles, arcade machines and computers from the 1970s/1980s/1990s and prior to covid was part of a team running large scale retro events twice per year.
