Ransomware infections: Lessons from the trenches
Ransomware landscape of 2022
Ransomware attacks have been on the rise in recent years, and 2022 was no exception. According to the latest DataProt ransomware statistics, the predicted frequency of ransomware attacks is one every 11 seconds. Ransomware gangs did not spare (and won’t spare) any industry as era of ransomware as-a-service (RaaS) opened the door to lucrative and dynamic opportunities for them.
Year of LockBit
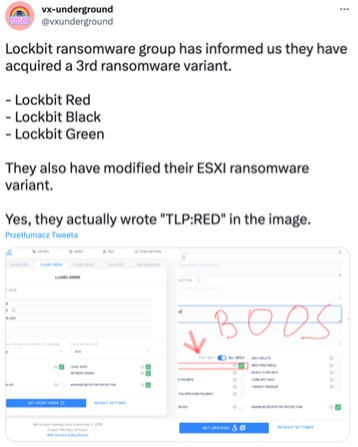
LockBit, discovered in 2019, returned in 2022 and became the most active and dangerous ransomware. It is not slowing down and aims to be on podium in 2023, impacting organizations across industries around the globe with the exception of Russia and former CIS countries because of their affiliate program rules – automated vetting process by fear of prosecution in these areas of the world.
2022 was also the year when LockBit, the criminal organization behind the ransomware of the same name, introduced its first ransomware bug bounty program, rewarding not only vulnerabilities but also “brilliant ideas” or doxing (revealing personal information) of affiliate program managers.
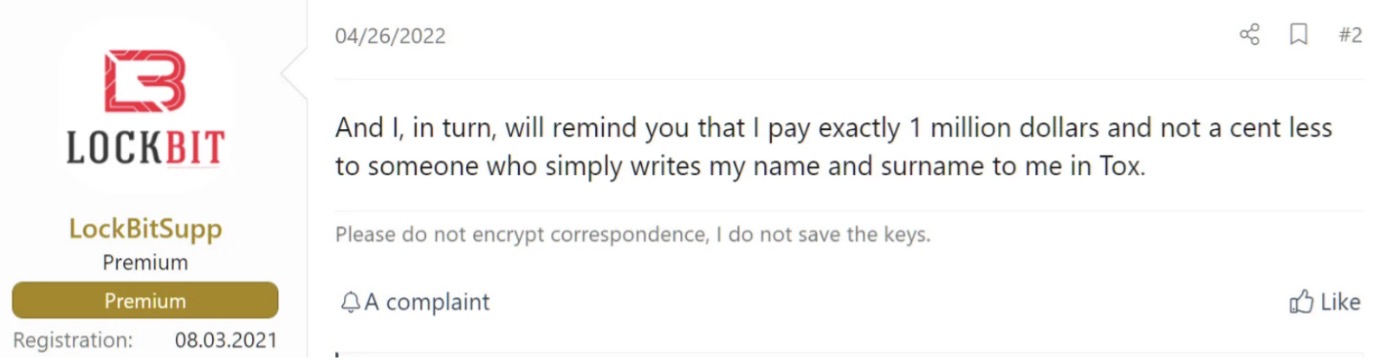
In addition, 2022 brought us ransomware lessons learned regarding the “hack back” strategy. A distributed denial-of-service (DDoS) attack took down the LockBit ransomware operation’s leak website, which appeared to have been launched in response to cybercriminals publishing data stolen from Entrust (a LockBit victim). The counterattack only slowed LockBit’s ability to leak the stolen data slightly, and failed to prevent the imminent disclosure.
After the attack, LockBit enhanced its DDoS resiliency and incorporated DDoS as part of the extortion step in its modus operandi. Though the DDoSers behind the counterattack remain unknown, the “hack back” strategy was a failed attempt to stop the data leak and drew immediate press attention to the attack.
Extortion at a new level
Ransomware infections are always designed with two main objectives:
- To disrupt the victim’s operations. A malware deployment can be a smokescreen to cover up the real intention of the attack.
- To get a ransom, which is always associated with extortion.
Decryptors aim for swift restoration and data exfiltration, followed by threat of publishing sensitive/secret data, DDoS attacks (LockBit, AlphV/BlackCat) or even creating personalized extortion services by notifying employers and customers about the leak (Cl0p, AlphV/BlackCat). Ransomware gangs have strengthened their approach by “hardcoding” extortion into their operations.
Good old TTPs
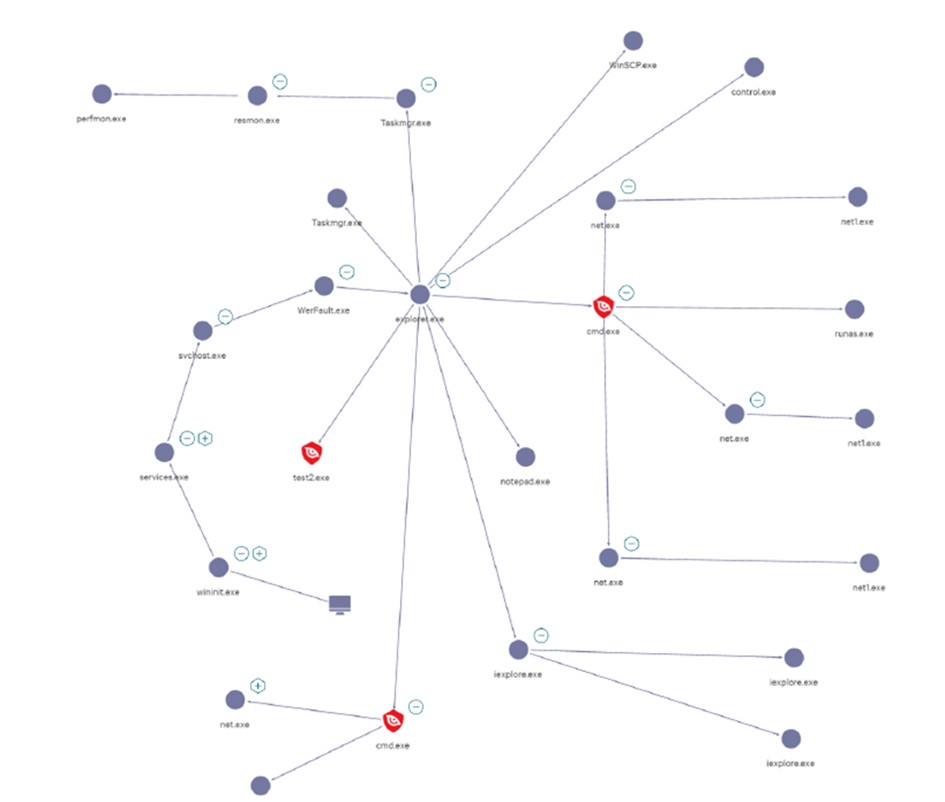
One of the most important lessons learned from ransomware is that it is not just a single piece of malware that encrypts and exfiltrates data. It is a full-blown multi-stage attack that employs multiple tactics, techniques and procedures (TTP) which rely on known vulnerabilities and tools.
This combined TTP approach is a very effective method to compromise many companies. Hence, when creating our “ransomware prevention checklist” below, we included common TTPs.
Reconnaissance and initial access
- Social engineering: phishing and insider access, through Remote Server Administration Tools (RSAT) like AnyDesk, TeamViewer, MobaXterm, mottynew.exe, ScreenConnect and WinSCP.

Source - Drive-by-download (Qakbot, SocGholish)
- Vulnerabilities (Exchange ProxyShell/ProxyLogon, VPN Auth Bypass/RCEs)
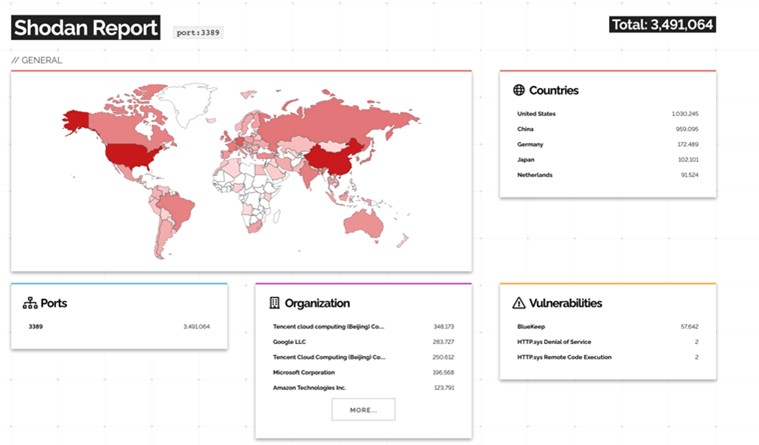
- Too much exposure (RDP, SMB exposed to the Internet, VPN with no MFA)

Hosts with RDP port exposed to the Internet - Compromised accounts
- Public repositories like GitHub
- Dark Web full of info stealers offers – like RedLine, Vidar
- Public Credential leaks
- Cooperation with other Threat Groups
- Previous Incidents
Execution and persistence
- Execution on its own or through scheduled task
- Powershell Empire
- VPN access
- Create additional VMs
Defense evasion
- GMER, PC Hunter and Process Tracker
- Group policy to disable MDE
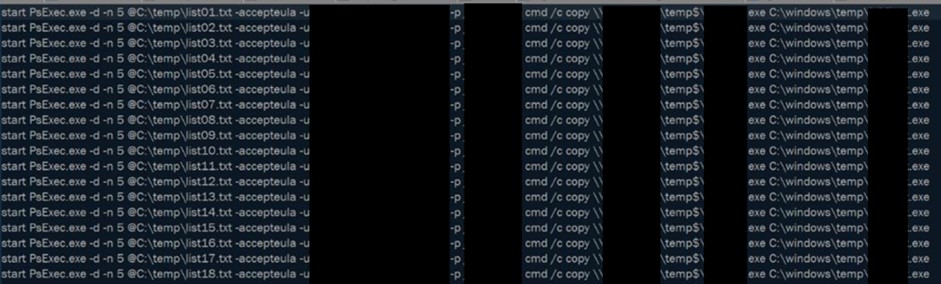
Lateral movement
Exfiltration
- Cloud storage tools like MEGA, FreeFileSync and RClone
- StealBit malware
- filetransfer[.]io
- Compromised M365 inboxes tampered with rules to exfiltrate mails
- WinRAR, 7zip
- WinSCP
- FileZilla
Impact
- Local and network encryption
- AES with key encrypted by RSA (generated with BCryptGenRandom)
- Removing administrators accounts
- Destruction of VMWare ESXi environment
- vssadmin usage to destroy VSS
How can you protect yourself from ransomware
Know about yourself better than attackers do
There is no place like home for an attacker who has found an environment full of shadow IT. Only a reliable configuration management database (CMDB) that is constantly updated will enable you to implement an effective ransomware defense and response strategy. One emerging technology — external attack surface management (EASM), which inventories your exposure — is a game changer in this fight.
The hygiene factor
Lessons learned from ransomware show that we continue to make the same mistakes when it comes to vulnerability remediation; therefore, you must ask yourself the following questions:
- Do I have a vulnerability management program – including scanning and a well-defined remediation process – in place to remediate 0-days/critical CVEs in few days?
- Do I have control over which of my services are exposed to the Internet?
- Which of my ports are open to the Internet?
- Which of my applications may be used in which environment within my organization?
- Do I have multi-factor authentication (MFA) implemented everywhere, especially for administrators? (Adversaries always look for them)
- Do I have control over my Active Directory domain, including secure configuration, identity protection and strict monitoring of changes to GPOs, sensitive accounts and UEBA?
These are just a few of the questions that we usually encounter during an incident response (IR). You can find more at https://www.cisa.gov/stopransomware/ransomware-guide
Don’t panic, it’s just ransomware
Incidents happen, so be prepared and create an effective IR plan. Here are some of the most common ransomware lessons we’ve learned from our IRs:
- Appoint a crisis management taskforce for efficient coordination
- Isolate (but don’t shut down) hosts and networks with ransomware infections
- Preserve highly volatile artifacts like firewalls, domain controllers and VPNs
- Don’t restore any system before securing evidence
- Collect detailed cyber threat intelligence (CTI) about ransomware to enhance your IR plan
- Get ready for a lot of work (Mean time of recovery is measured in weeks)
EDR is your best buddy
In our experience, all ransomware victims had no endpoint detection and response (EDR) solution or platform in place. IR without EDR takes 2-3 times longer to respond and recover than with it.
Attack starts outside your organization
Detecting your problems before adversaries do is a key step in ransomware prevention. Digital risk protection services (DRPS) will help you identify credential leakage, stolen information being sold and publicly available credentials as early as possible.
Takeaways
One of the key lessons we learned from ransomware in 2022 is that we don’t apply the lessons learned from ransomware attacks fast enough. Bad actors have been exploiting old vulnerabilities (made famous from 2018 to 2021), launching familiar phishing campaigns and still achieving success. We must start immediately with the basic hygiene by running vulnerability checks, closing unnecessary ports and installing EDRs, followed by implementing EASM, leakage monitoring, IR playbooks, red teaming and threat hunting. Our ultimate goal should be to build resilience not only against ransomware, but also against any known or unknown threats that are yet to come.
About the author

Aleksander Pawlicki
Global CERT Incident Response Lead, Senior Atos Expert, Security Enthusiast
In charge for technical leadership of Atos Global CERT, which provides services of Digital Security and Incident Response (DFIR), Threat Intelligence (TI) and Threat Hunting (TH) to Atos and its customers.
Responsible for leading incident response for large investigations or crisis.
Security enthusiast, who strongly believes in purple team philosophy.